Requirement:We might have a situation in NAC implementations with Onguard persistent agent where the NAS device sends an authentication request at random without the device actually losing network connectivity like in some minor cases of wireless roaming or in cases of re-authentication on wired switches. In these scenarios at the end device level the network interface is still up and running resulting in the Onguard agent on the client not detecting any network change, hence not sending any WebAuth request resulting in the client getting stuck in the initial role.
Solution:This article provides a solution for that problem by making use of Endpoint attributes that carry the Last Healthy TimeStamp and also the Last Health Status.These attributes can be used to make a policy decision to allow it on the network if its been marked as healthy within a given span of time. For instance if a device goes through health checks now and the NAS device decides to send another authentication request after say 3 hours without any disconnection on the end device then the client could be allowed on the network directly seeing that the client's last health status is healthy and the client was marked healthy within the last 8 hours.
Configuration:Firstly we need to create the endpoint attributes for carrying the Last Healthy TimeStamp and also the Last Health Status.
We need to navigate to Administration>>Dictionaries>>Attributes and click on Add as shown in the screenshot below to create new attributes.
Last-Healthy-TimeStamp is the name of the attribute, the Datatype is going to be Date-Time so that we can use it to tag the Endpoint Healthy Timestamp.
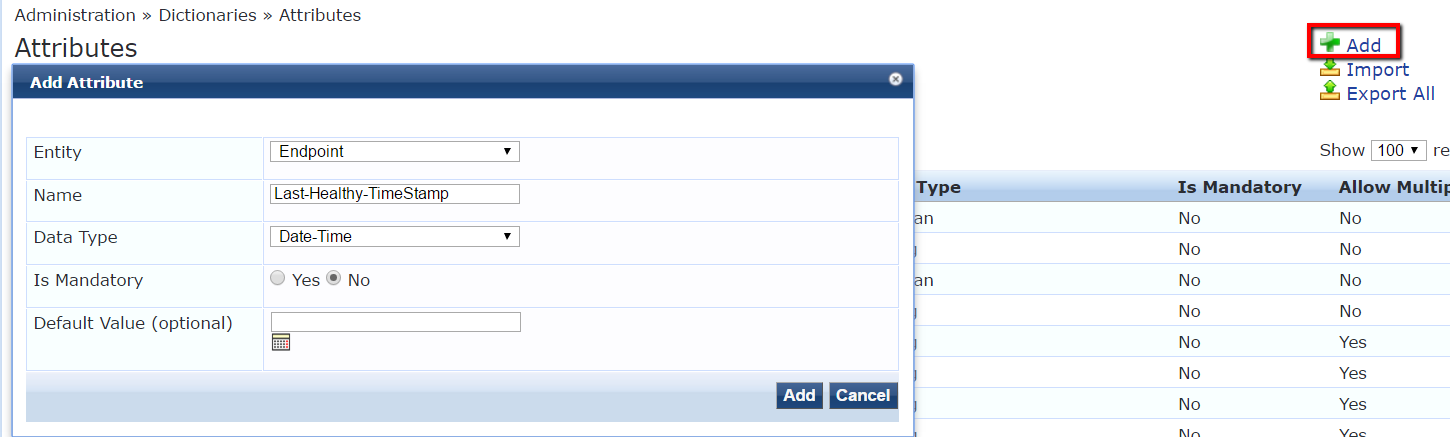
The other attribute we need to create is the "Last-Health-Status" which should be of Datatype String so that it can carry the last health status of an endpoint.
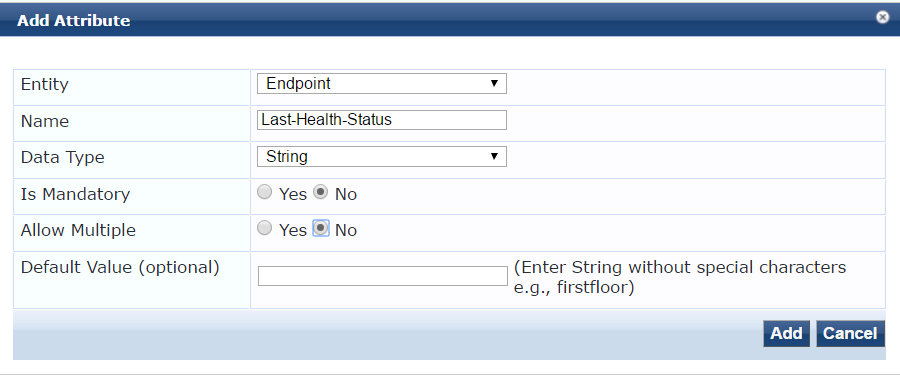
Once we create these two attributes we should be able to use them in our configuration and update these attributes with the appropriate values.
We should update the Last-Healthy-TimeStamp with the timestamp "now" whenever the client is found to be healthy in the WebAuth service. We need to create a filter in the Time Source Authentication source so that we have the timestamp for "now" in minutes in the Date-Time format.
You need to goto Configuration>>Authentication>>Sources>> Click on [Time Source] and then goto the Attributes tab and then try to add new filter as shown in the screenshot below
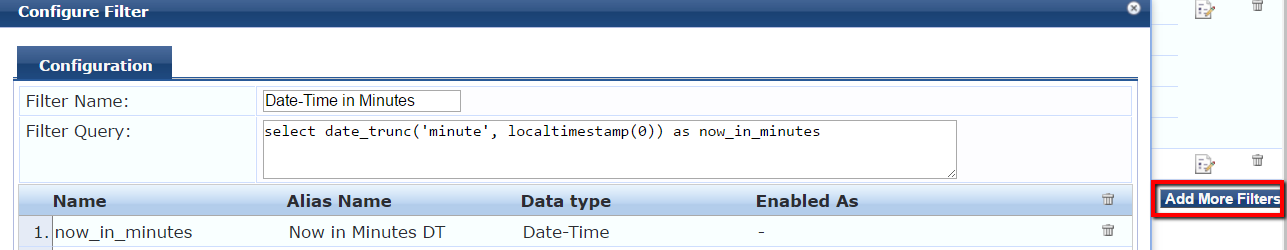
select date_trunc('minute', localtimestamp(0)) as now_in_minutes
now_in_minutes needs to be the name on filter configuration which is the value being returned by the query and Now in Minutes DT is the alias which we can use in our policies and conditions.
Once we have this filter ready we can use this to update the Endpoint with its value using an enforcement profile as shown below
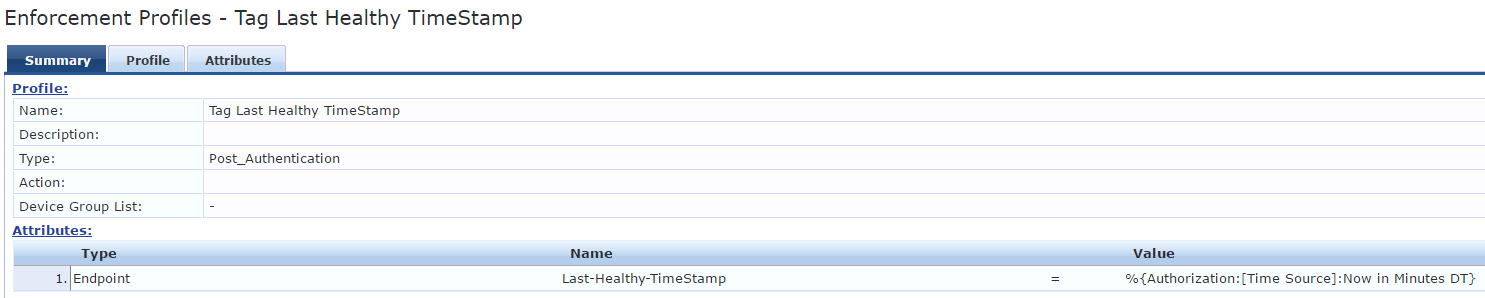
Similarly we can also update the Endpoint with the Last Health Status using an enforcement profile as shown below

so that we can check for Health Status along with the TimeStamp.
Both these enforcement profiles can be used in the WebAuth service to tag the Endpoints with the Last Healthy Timestamp and also the Last Health Status when the client is Healthy as shown in the screenshot below

We can also update the Last Health Status for clients who are not Healthy so that when we try to allow the user to get on based on Last Healthy TimeStamp we can also make sure that the client's Last Health Status is Healthy.

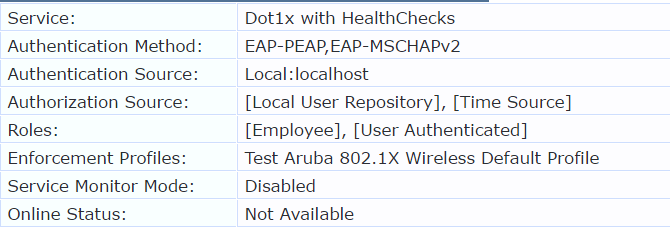
Once we have configured these attributes to be set on the Endpoint during WebAuth we can reference them in the 802.1x authentication service. .
We can create a filter based on the last health check time and allow a user authenticating within a certain time frame from the last healthy timestamp like 8 hours in this example.
The filter query should be configured as shown below in the [Time Source] authentication source.
select CASE
WHEN(EXTRACT(EPOCH FROM timestamp '%{Endpoint:Last-Healthy-Timestamp}') - EXTRACT(EPOCH FROM date_trunc('minute', localtimestamp(0) - interval '8 hours')))::int > 0 THEN 'true'
ELSE 'false'
END as HealthywithinEight
You need to click on "Add More Filters" , provide a name for the filter

The name should be "HealthywithinEight" and the alias can be anything, which in this example is "Healthy with 8 hours" with Data type "Boolean"
Once this is configured you should be able to reference it in any service. Your enforcement conditions could be configured as shown below in the service.
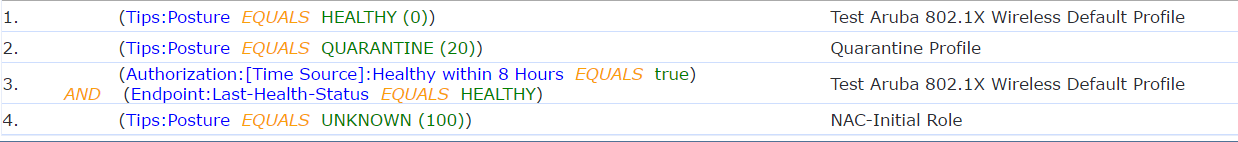
You should have the conditions having "Posture" above the condition that is referencing the "Healthy within 8 Hours" value as Posture is always current than endpoint attributes.
Once this is configured we can make sure that any requests that the NAS devices send without a corresponding WebAuth (due to no disconnect at the interface level) would be handled and the clients can be avoided from falling in the Initial Role and losing network connectivity.
VerificationWe can verify that if we see a WebAuth request with the client status as Healthy we are updating the Endpoint with Last-Health-Status and also Last-Healthy-TimeStamp
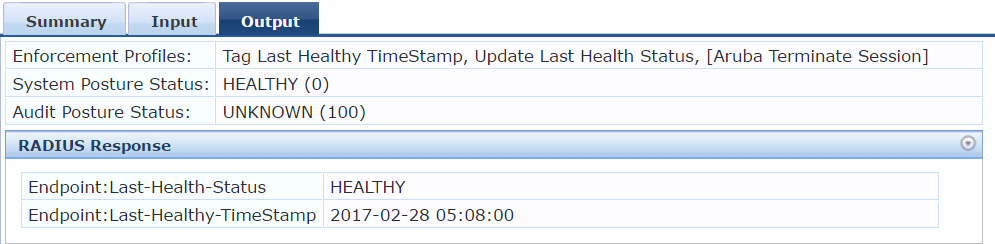
and subsequently if we see an authentication request without a corresponding Webauth within the next 8 hours you should be able to put the client in the post-auth role directly without having to goto the NAC initial role seeing that "Healthy within 8 Hours" is true.