Requirement:
Configuring MAC-based authorization on OfficeConnect 1920S Switches to authenticate across ClearPass
Solution:
OfficeConnect switches send EAP-MD5 authentication requests when you enable MAC-Based authentication. ClearPass needs to be configured for EAP-MD5 authentication for this to work.
EAP-MD5 cannot be performed across the Endpoint Repository in ClearPass, so you need to create an Allow-All MAC Static Host List. You can create a new Static Host List on ClearPass that allows all devices by following this article.
Even though we are authenticating across an Allow-All Static Host List you can still authorize across the Endpoint Repository and apply the appropriate enforcement depending on the category of the device and deny other devices after profiling if desired.
Configuration:
The configuration on the OfficeConnect Switch for MAC-Auth as below along with configuring a RADIUS server with the Clearpass IP

Once the MAC authentication is enabled on a port with Clearpass configured as the RADIUS server, the Switch will start sending EAP-MD5 requests to the ClearPass.
You can configure your service to accept requests with service categorization rules like below

In the authentication method you need to configure EAP-MD5 as the authentication method
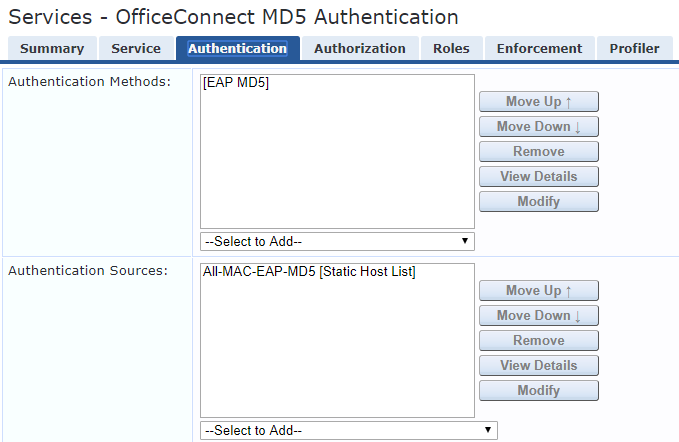
As the authentication source you need to create a new authentication source and map the the Static Host List you create. The Static Host list you need to create is as shown below.
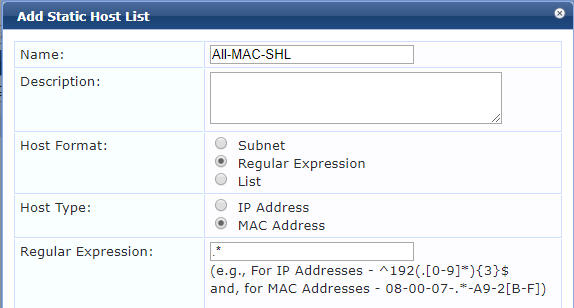
The Regular Expression to allow all MAC addresses is .*
That Static Host List will allow any device that connects to get through the authentication phase after which you can authorize the device across the Endpoint Repository to assign the appropriate enforcement based on the Device Type or Category.
You can setup your service to authorize across the Endpoints Repository

Then you can have rules that look for the device category and return the appropriate enforcement
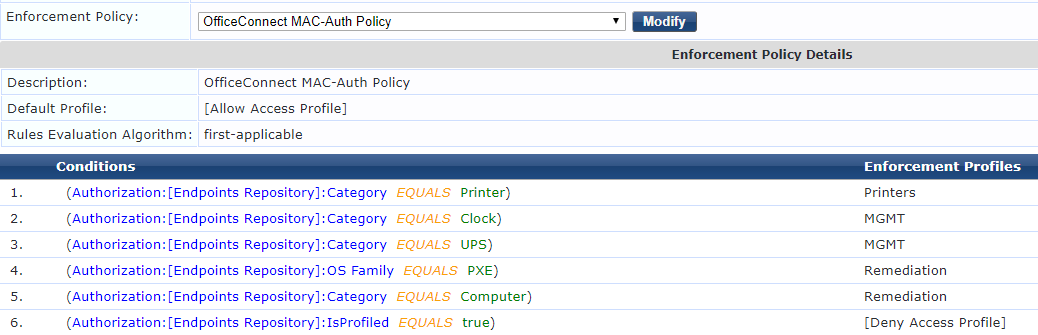
Please note that this article assumes that you have the required pieces setup for profiling the devices on ClearPass like the IP Helper on the network etc.
Refer to our profiling documentation if you want to understand how ClearPass profiling works.
Verification
Once we have all this configured we can see that the MAC Authentication would succeed with EAP-MD5 as the authentication method as shown below
Request Details Summary -
Session Identifier: R00001756-01-5b30c374
Date and Time: Jun 25, 2018 13:27:00 IDT
Username: 842519238D11
End-Host Identifier: 84:25:19:23:8d:11
Access Device IP/Port: x.x.x.x:10
Audit Posture Status: UNKNOWN (100)
System Posture Status: UNKNOWN (100)
Login Status: ACCEPT
Policies Used -
Service: OfficeConnect MD5 Authentication
Authentication Method: EAP-MD5
Authentication Source: SHL:All-MAC-EAP-MD5
Authorization Source: [Endpoints Repository]
Roles: [User Authenticated]
Enforcement Profiles: Printers
Service Monitor Mode: Disabled
Input RADIUS Attributes -
Radius:IETF:Called-Station-Id = ec-eb-b8-3c-ea-9e
Radius:IETF:Calling-Station-Id = 84:25:19:23:8d:11
Radius:IETF:Framed-MTU = 1500
Radius:IETF:NAS-Identifier = ec-eb-b8-3c-ea-9c
Radius:IETF:NAS-IP-Address = x.x.x.x
Radius:IETF:NAS-Port = 10
Radius:IETF:NAS-Port-Type = 15
Radius:IETF:User-Name = 842519238D11
Input Computed Attributes -
Authentication:ErrorCode = 0
Authentication:Full-Username = 842519238D11
Authentication:Full-Username-Normalized = 842519238D11
Authentication:MacAuth = KnownClient
Authentication:OuterMethod = EAP-MD5
Authentication:Posture = Unknown
Authentication:Source = All-MAC-EAP-MD5
Authentication:Status = MAB
Authentication:Username = 842519238D11
Authorization:Sources = [Endpoints Repository]
Connection:Client-Mac-Address = 84:25:19:23:8d:11
Connection:Client-Mac-Address-Colon = 84:25:19:23:8d:11
Connection:Client-Mac-Address-Dot = 8425.1923.8d11
Connection:Client-Mac-Address-Hyphen = 84-25-19-23-8d-11
Connection:Client-Mac-Address-NoDelim = 842519238d11
Connection:Client-Mac-Address-Upper-Hyphen = 84-25-19-23-8D-11
Connection:Client-Mac-Vendor = Samsung Electronics
Connection:Dest-IP-Address = y.y.y.y
Connection:Dest-Port = 1812
Connection:NAD-IP-Address = x.x.x.x
Connection:Protocol = RADIUS
Connection:Src-IP-Address = x.x.x.x
Connection:Src-Port = 40565
Date:Date-Time = 2018-06-25 13:27:00
Input Authorization Attributes -
Authorization:[Endpoints Repository]:Category = Printer
Authorization:[Endpoints Repository]:Conflict = false
Authorization:[Endpoints Repository]:Device Name = Xerox Printer
Authorization:[Endpoints Repository]:Hostname = sec842519238d11
Authorization:[Endpoints Repository]:OS Family = Xerox
Authorization:[Endpoints Repository]:Other Category =
Authorization:[Endpoints Repository]:Other Device Name =
Authorization:[Endpoints Repository]:Other OS Family =
Authorization:[Endpoints Repository]:StaticIp = false
Output RADIUS Attributes -
Radius:IETF:Session-Timeout = 10800
Radius:IETF:Termination-Action = 1
Radius:IETF:Tunnel-Medium-Type = 6
Radius:IETF:Tunnel-Private-Group-Id = 204
Radius:IETF:Tunnel-Type = 13