Requirement:From ClearPass version 6.5 onwards we support REST API calls for performing most Guest operations as seen in the screenshot below.

This article covers creating, updating, deleting, fetching ClearPass guest accounts using REST API calls.
Solution:We assume that you have gone through the steps required to get the API Integration running. If that's not done please go through the document attached to get things started.
The Bearer oauth token that is in use in the examples below has been generated by following the steps attached in the document.
API call to create a new guest account
To create a new account the primary fields are username, password, role_id. The other attributes can be included upon requirement. Please note that the expire_time needs to be in epoch format.
curl -X POST "https://<ClearPass IP/hostname>/api/guest" \
-H "Content-Type: application/json" \
-H "Authorization: Bearer a6d2873200bee25768307c32ee22415ac8ad203a" \
--data '{
"enabled": true,
"expire_time": "1438562410",
"password": "Aruba@!23$",
"role_id": 2,
"username": "testaccount"
}'\
-m 30 \
-v \
-k
The response from the server would tell us the status of the request. If you get an HTTP 200 status code as a response with data telling us details about the account, we are good. Any other HTTP status code would indicate a problem.
API call to update a guest account
To update a guest account you need to know the ID of the account. You would get the ID as a response when the account gets created. If you want to get the ID of the account otherwise, we can do a HTTP GET with the username as the filter and capture the ID from it. The ID for the Guest account we are trying to update is 3066. Please not that the ID of the account needs to be appended as a part of the URL. The HTTP Status Code that you would get for a successful update operation is HTTP 200 with the updated data.
curl -X PATCH "https://<ClearPass IP/hostname> /api/guest/3066" \
-H "Content-Type: application/json" \
-H "Authorization: Bearer a6d2873200bee25768307c32ee22415ac8ad203a" \
--data '{
"enabled": true,
"password": "Clearpass!23$",
"role_id": 2,
"username": "testaccount"
}'\
-m 30 \
-v \
-k
API call to delete a guest account
To delete a guest account as well we need the ID of the guest account. The status code you would see as a response for a successful delete operation is HTTP 204 with no data.
curl -X DELETE "https://<ClearPass IP/hostname>/api/guest/3066" \
-H "Content-Type: application/json" \
-H "Authorization: Bearer a6d2873200bee25768307c32ee22415ac8ad203a" \
-v \
-k
API call to fetch a guest account details
If we want to fetch details about a specific guest account we need to append the ID to the URL and perform a HTTP GET. The HTTP Status code that we get as a response for a a successful fetch along with the account data is HTTP 200.
curl -X GET "https://<ClearPass IP/hostname>/api/guest/3066" \
-H "Content-Type: application/json" \
-H "Authorization: Bearer a6d2873200bee25768307c32ee22415ac8ad203a" \
-m 30 \
-v \
-k
Configuration:The configuration required is covered in the document attached.
VerificationTo verify that all the operations are being performed via the API call we can login to the Guest module and observe the Manage guest accounts page.
Verification of the create account
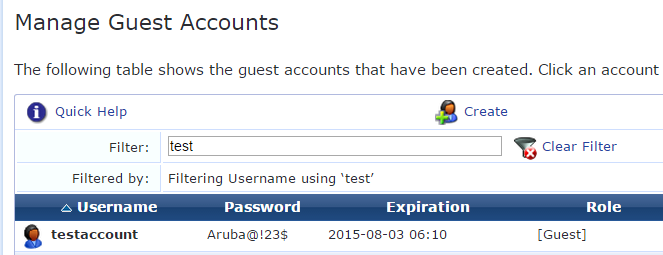
Verification of the update account
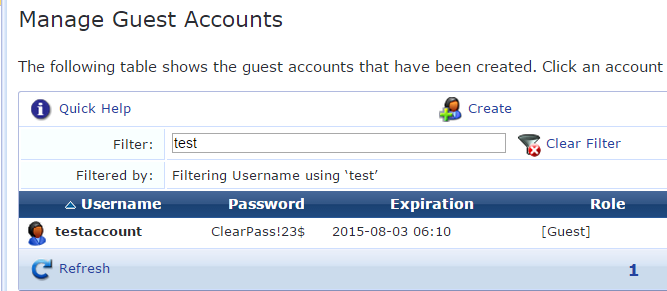
Verification for fetch account details
When you do a fetch operation you would see the data being returned in JSON Format.
{
"id": "3066",
"username": "testaccount",
"start_time": 1437765026,
"expire_time": 1438562410,
"sponsor_name": "apicall",
"sponsor_profile": "1",
"enabled": true,
"current_state": "active",
"notes": null,
"visitor_carrier": null,
"role_name": "[Guest]",
"role_id": 2,
"sponsor_profile_name": "IT Administrators",
"source": "api",
"_links": {
"self": {
"href": "https://<clearpass IP>/api/guest/3066"
}
}
}
Verification of delete guest account

Attachments:Getting_Started_ClearPass_6.5_HTTP_APIs.docx