This article will have a focus on enabling, configuring and troubleshooting alarm for "ARP poisoning" on the Aruba Instant™ Access Points running Aruba Instant™ 6.2.1.0-3.3.0.0 Software.
A potential rogue machine in your LAN may poison your machines ARP cache so that the machine thinks that the attacker is the gateway or the destination machine. Then all packets to that machine will go through the rogue machine, and it will be, from the network’s standpoint, between the client and the destination machine. This is actually fairly simple to do, and is also fairly easy to detect as a result.
Possible ARP poisoning attacks are logged and an SNMP trap is sent.
The configuration and verification steps mentioned in this article are tested on IAP 105 running 6.2.1.0-3.3.0.0.
Environment : This article applies to all the IAPs running a minimum OS version of 6.2.1.0-3.3.0.0.
Arp poison check is security feature that enable the IAP to trigger an alert by intercepting all ARP requests and responses, and by verifying their authenticity and notifying the user about the ARP poisoning that may have been caused by the rogue APs.
You can configure ARP poison check using Instant UI or CLI.
In the Instant UI
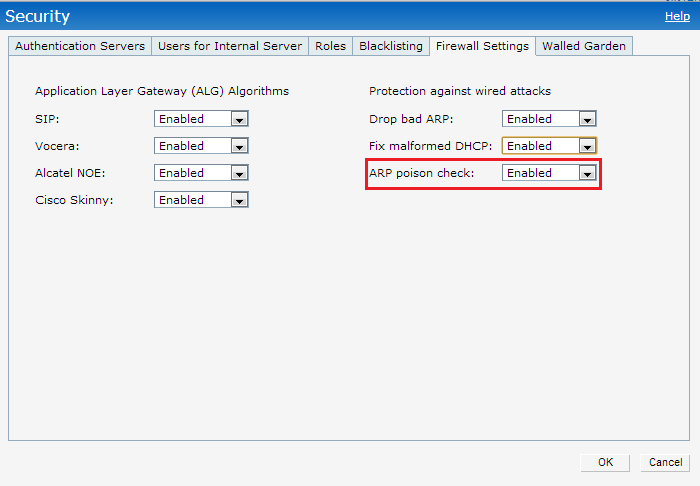
To configure ARP poison check :
1. Click the Security link at the top right corner of Instant main window.
2. Click the Firewall Settings tab. The Firewall Setting tab contents are displayed.
3. select the following check box:
- Select ARP poison check to enable the IAP to trigger an alert notifying the user about the ARP poisoning that may have been caused by the rogue APs.
4. Click OK.
In the CLI
To configure ARP poison check
(Instant Access Point)(config)# attack
(Instant Access Point)(ATTACK)# poison-check-enable
(Instant Access Point)(ATTACK)# end
(Instant Access Point)# commit apply
To configure SNMP Traps
Instant supports the configuration of external trap receivers. Only the IAP acting as the Virtual Controller generates traps.
You can configure SNMP traps using Instant UI or CLI.
In the Instant UI
To configure an SNMP trap receiver:
1. Navigate to System>Show advanced options> Monitoring. The Monitoring window is displayed.
2. Under SNMP Traps, enter a name in the SNMP Engine ID text box. It indicates the name of the SNMP agent on the access point. The SNMPV3
agent has an engine ID that uniquely identifies the agent in the device and is unique to that internal network.
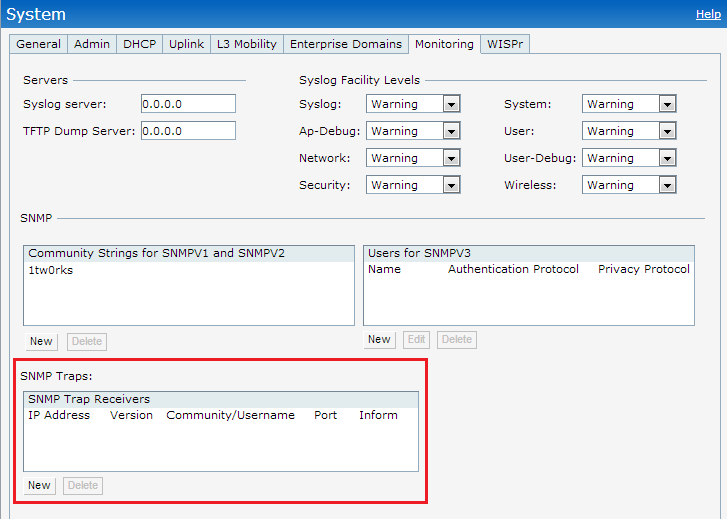
3. Click New and update the following fields:
- IP Address : Enter the IP Address of the new SNMP Trap receiver.
- Version : Select the SNMP version v1, v2c, v3 from the drop-down list. The version specifies the format of traps generated by the access point.
- Community/Username : Specify the community string for SNMPv1 and SNMPv2c traps and a username for SNMPv3 traps.
- Port : Enter the port to which the traps are sent. The default value is 162.
- Inform : When enabled, traps are sent as SNMP INFORM messages. It is applicable to SNMPV3 only. The default value is Yes.
4. Click OK to view the trap receiver information in the SNMP Trap Receivers window.
In the CLI
To configure SNMP traps:
(Instant Access Point)(config)# snmp-server host <IP-address> {version 1 | version 2 | version 3} <name> udp-port <port> inform
(Instant Access Point)(config)# end
(Instant Access Point)# commit apply
Traps used to report ARP poison check to a external SNMP Trap receiver :
wlsxTrapSpoofedIpAddress
wlsxTrapSpoofedOldPhyAddress
wlsxTrapSpoofedNewPhyAddress
To view the configuration status:
(Instant Access Point)# show attack config
Current Attack
--------------
Attack Status
------ ------
drop-bad-arp Enabled
fix-dhcp Enabled
poison-check Enabled
To view the attack statistics
(Instant Access Point)# show attack stats
attack counters
--------------------------------------
Counter Value
------- -------
arp packet counter 10
drop bad arp packet counter 3
dhcp response packet counter 0
fixed bad dhcp packet counter 0
send arp attack alert counter 3
send dhcp attack alert counter 0
arp poison check counter
garp send check counter 0