Basically, I'm trying to set an access rule on IAP105 in order to redirect dns traffic from 53 to 54. Apparently it works when I set one rule with destination nat to my first dns server(10.1.1.1). See the config below:
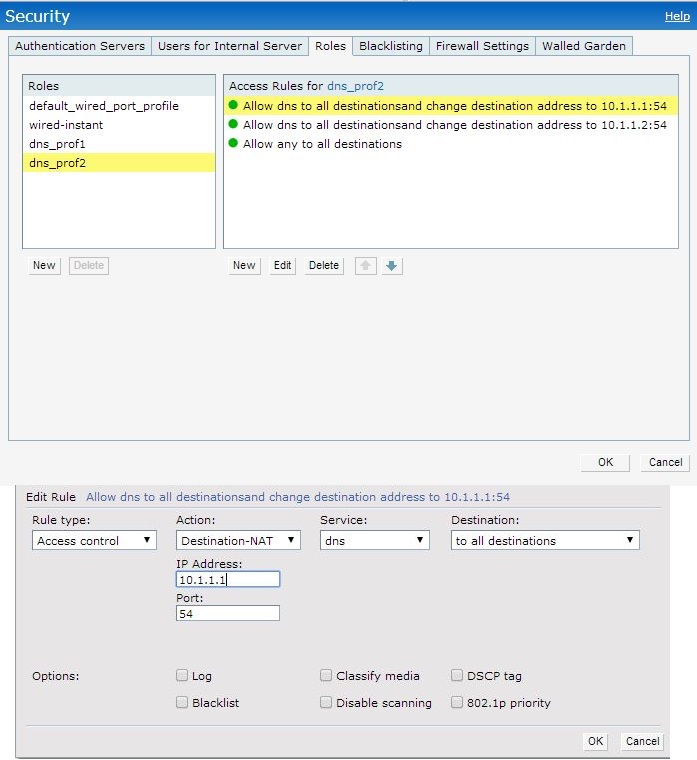
Now, when I add second rule to redirect to the same port 54 but to a second dns server(10.1.1.2), I have two dns servers listening on the same port, and click OK, the IAP would keep only last added rule.

IAP is running on 6.2.1.0-3.4.0.2_39953
Went through other posts, couldn't find an answer. Any help much appreciated. Thanks.