Hi,
You can achieve this through the user role( Post Auth role). create a policy which will not allow the guest to access the internal network.
Create a role with the following policy,
Step 1 : create an alias for your internal network ,
Ex:
netdestination internal_NW
(config-dest) #network 20.1.1.0 255.255.255.0
Step 2 : create policy as follows
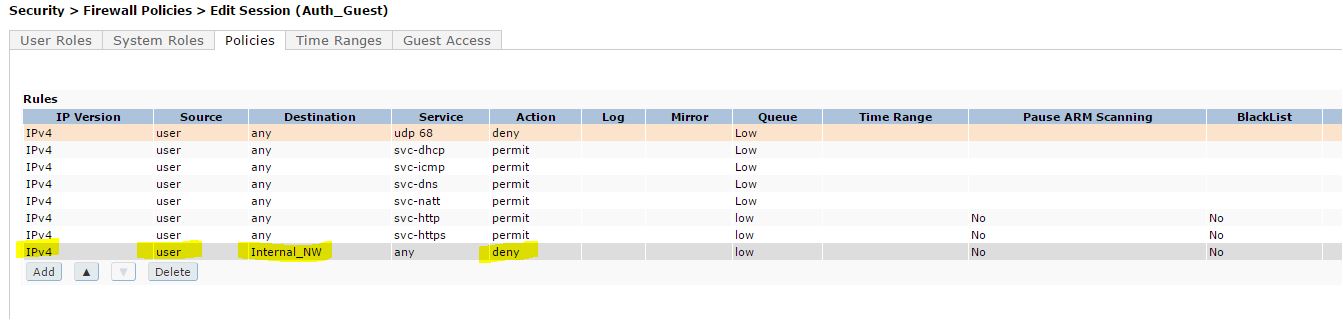
Step 3 : map this policy to the role which is the authenticated role for all CP authenticated users
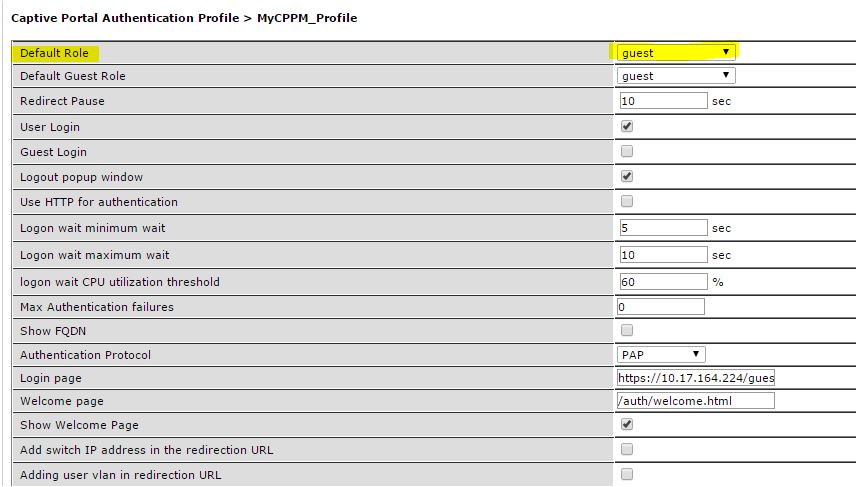
Hope you got some idea now.
Please feel free for any further help on this.