Tutorial by: NightShade1
Hello Everyone
To configure a L3 Rogue ap detection you need to know a few things before.
1-You can detect this with APS but the aps need to be in the same vlans, controller approach is just much better.
2-This just apply for a particular site, i mean if you want to rogue detect a remote site which you dont have a controller you can do it with an AP(but this is not covered in this tutorial
3-You will need to add the IPS/IDS license for Enforcement.
Enforcement can take different shapes, including containing rogue APs by performing denial-of-service (DoS) attacks wirelessly, ARP cache poisoning on the wire, shielding valid clients from connecting to rogue APs, and blacklisting cients so that they are
unable to attach to the WLAN
Lets begin!
To this to work what you need to do is:
1-Trunk all the vlans you want to monitor to the Controller and on the controller trunk them back to the switch
Now how do you know which VLANS you should trunk?
Well thats an easy question to answer... All the vlans that the end users has access to connect rogue APS. I mean you wont trunk vlans like Server vlans, or things like that which a end user on your company you know has no access.
So
Trunk all those vlans in which they got access.
Note: Remember, you need to create all these vlans on the controller even if you are not using it in them. LEt say you need to inspect vlan 10,11,12,13,14,15. Then this means you need to:
1-create those vlans on the controller
2-trunk them to the switch
3-Trunk them from the switch to the controller back.
Note:Normally i plug the controller to the clients Switch Core so i got access to all the vlans without doing too much in their network.
Good. Now after you did this you need to go to the CLI
POST 6.1.3.2
(Office_Controller) (config) #ids wms-general-profile
(Office_Controller) (IDS WMS General Profile) #learn-system-wired-macs
The command for PRE 6.1.3.2 you do it on the config i mean:
(Office_Controller) (config) #wms general learn-system-wired-macs enable
To check its on you issue the command
#show wms general
You will see something like this
General Attributes
------------------
Key Value
--- -----
poll-interval 60000
poll-retries 3
ap-ageout-interval 30
adhoc-ap-ageout-interval 5
sta-ageout-interval 30
learn-ap disable
persistent-neighbor enable
persistent-valid-sta disable
propagate-wired-macs enable
learn-system-wired-macs enable
stat-update enable
You will see learn-system-wired-mac enable
Now you need to wait for a while and you should start looking those rogues APS appering on your dashboard on security tab
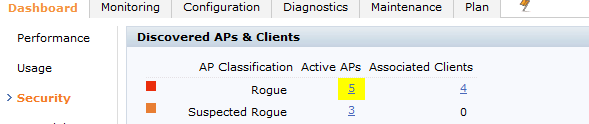
Now remenber in the IPS /IDS configuration you have to put to contain automatically rogue APS
As a personal configuration i always put rogue ap containment on but i uncheck the suspected rogue ap containment... The Rogue APS is something that the controller is 100% sure its on your network! but a suspected rogue AP it could be a neighbor AP?
This is done on the AP group-->IDS-->IDS Unathorized Device
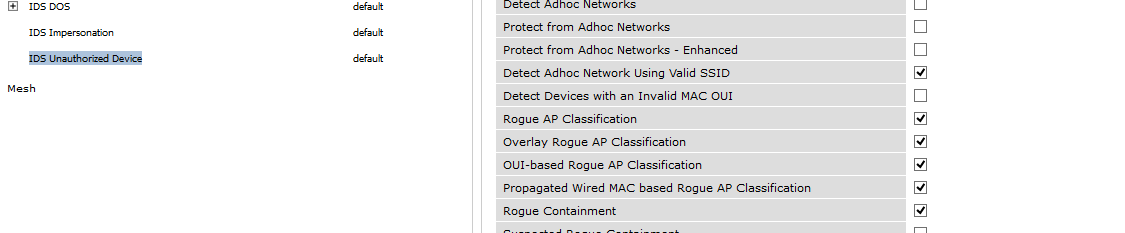
If you dont want to contain anything and you just want to know if you got Rogue APS, just uncheck rogue containment and also suspected rogue ap containment...
Note: As general rule here please DONT USE DEFAULT PROFILE to configure IDS/IPS Profiles in general, create new ones please. Sometimes you can do a misconfig and you can return to default withot any config easily and then look where you were mistaken. When i was starting to configure this, it was a great help for me, and i still doing it, i never toch default config for this. I always create a new one.
Cheers
Carlos
Hello Everyone
To configure a L3 Rogue ap detection you need to know a few things before.
1-You can detect this with APS but the aps need to be in the same vlans, controller approach is just much better.
2-This just apply for a particular site, i mean if you want to rogue detect a remote site which you dont have a controller you can do it with an AP(but this is not covered in this tutorial
3-You will need to add the IPS/IDS license for Enforcement.
Enforcement can take different shapes, including containing rogue APs by performing denial-of-service (DoS) attacks wirelessly, ARP cache poisoning on the wire, shielding valid clients from connecting to rogue APs, and blacklisting cients so that they are
unable to attach to the WLAN
Lets begin!
To this to work what you need to do is:
1-Trunk all the vlans you want to monitor to the Controller and on the controller trunk them back to the switch
Now how do you know which VLANS you should trunk?
Well thats an easy question to answer... All the vlans that the end users has access to connect rogue APS. I mean you wont trunk vlans like Server vlans, or things like that which a end user on your company you know has no access.
So
Trunk all those vlans in which they got access.
Note: Remember, you need to create all these vlans on the controller even if you are not using it in them. LEt say you need to inspect vlan 10,11,12,13,14,15. Then this means you need to:
1-create those vlans on the controller
2-trunk them to the switch
3-Trunk them from the switch to the controller back.
Note:Normally i plug the controller to the clients Switch Core so i got access to all the vlans without doing too much in their network.
Good. Now after you did this you need to go to the CLI
POST 6.1.3.2
(Office_Controller) (config) #ids wms-general-profile
(Office_Controller) (IDS WMS General Profile) #learn-system-wired-macs
The command for PRE 6.1.3.2 you do it on the config i mean:
(Office_Controller) (config) #wms general learn-system-wired-macs enable
To check its on you issue the command
#show wms general
You will see something like this
General Attributes
------------------
Key Value
--- -----
poll-interval 60000
poll-retries 3
ap-ageout-interval 30
adhoc-ap-ageout-interval 5
sta-ageout-interval 30
learn-ap disable
persistent-neighbor enable
persistent-valid-sta disable
propagate-wired-macs enable
learn-system-wired-macs enable
stat-update enable
You will see learn-system-wired-mac enable
Now you need to wait for a while and you should start looking those rogues APS appering on your dashboard on security tab
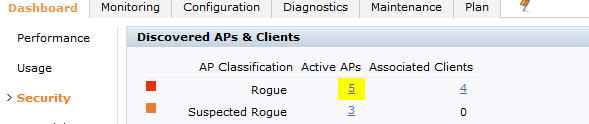
Now remenber in the IPS /IDS configuration you have to put to contain automatically rogue APS
As a personal configuration i always put rogue ap containment on but i uncheck the suspected rogue ap containment... The Rogue APS is something that the controller is 100% sure its on your network! but a suspected rogue AP it could be a neighbor AP?
This is done on the AP group-->IDS-->IDS Unathorized Device
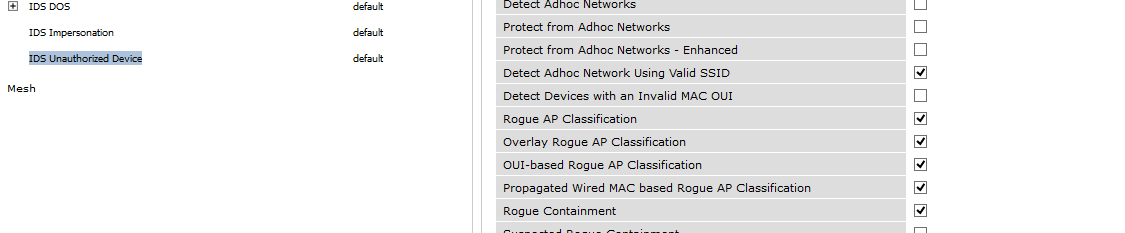
If you dont want to contain anything and you just want to know if you got Rogue APS, just uncheck rogue containment and also suspected rogue ap containment...
Note: As general rule here please DONT USE DEFAULT PROFILE to configure IDS/IPS Profiles in general, create new ones please. Sometimes you can do a misconfig and you can return to default withot any config easily and then look where you were mistaken. When i was starting to configure this, it was a great help for me, and i still doing it, i never toch default config for this. I always create a new one.
Cheers
Carlos