What you can do it allow the VPN traffic in the captive portal initial role.
Please check what is the initial role that users get when they are redirected to the captive portal, by default that is the guest-logon role.
If you add the required traffic for the VPN in that role, before the captiveportal roles, that traffic will be allowed 'through' the captive portal (not triggering the captive portal).
You can create a new policy to allow traffic to your VPN service, for example if the VPN service is at IP 180.31.210.88, and uses HTTPS (tcp-443) and NAT-T (udp-4500), you can create the following policy:
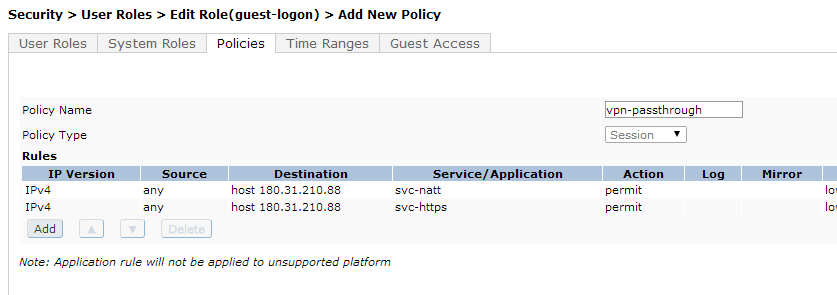
Then add this policy to your inital role for guest users, above the captive portal rules:

This will allow the traffic as defined in the vpn-passthrough policy, without requiring to use the captive portal. One note to add, if you need traffic other than HTTP and HTTPS, you may need to allow this also in the role that is applied after the logon. The default 'guest' role does only allow http and https.
Another approach can be to use the captive portal whitelist, where you create a named or IP destination in ADVANCED SERVICES, Stateful Firewall, Destination; and apply that to the captive portal whitelist (Security, Authentication, L3 Authentication, Captive Portal Authentication).
Command-line configuration: http://community.arubanetworks.com/t5/Command-of-the-Day/COTD-Allow-OCSP-Requests-In-Logon-Role/m-p/14624
Aruba Instant has similar methods to make this work, choose for Role-based in the Security tab for your SSID.
Herman