1) All Endpoints, Guest Devices and IPAM entries are deleted ; Roku is factory defaulted.
2) Turn on Roku
3) Roku attempts to connect to open SSID. Here's the configuration as the Access Tracker sees it.
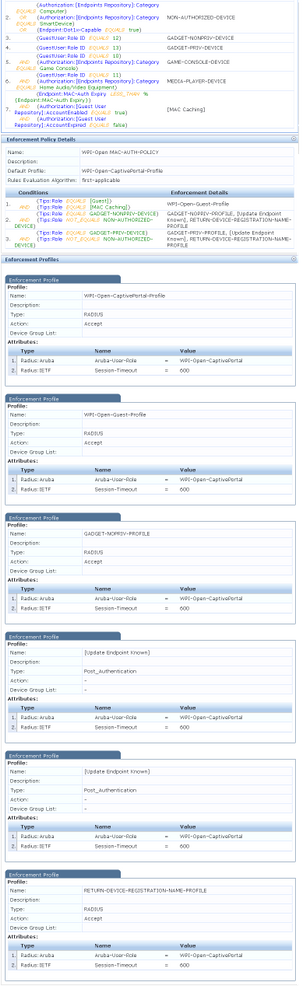
4) Roku is registered in IPAM
5) IPAM Triggers update to Endpoint via PATCH /api/endpoint/mac-address/XXXXXXXXXXXX and the following JSON:
{
"status": "Known",
"attributes": {
"Owner": "bjhiggins@wpi.edu",
"IPAM-Hostname": "rogues-roku.dyn.wpi.edu",
"IPAM-AdminState": "OK",
"IPAM-NAS-IP-Address": "",
"IPAM-NAS-Port-ID": "",
"IPAM-RADIUS-VLAN": "",
"IPAM-TimeStamp": "2017-07-19 00:00:01 EDT",
"Guest Role ID": "",
"MAC-Auth Expiry": "",
"Username": ""
}
}
6) IPAM Triggers creation of Guest Device via POST /api/device?change_of_authorization=true with the following JSON:
{
"mac": "XXXXXXXXXXXX",
"enabled": "1",
"role_id": 12,
"sponsor_name": "bjhiggins@wpi.edu",
"visitor_name": "rogues-roku.dyn.wpi.edu",
"airgroup_enable": "1",
"airgroup_shared": "0",
"airgroup_shared_user": "bjhiggins@wpi.edu",
"airgroup_shared_role": "authenticated",
"airgroup_shared_location": "default",
}
7) The moment the Guest Device is created, I have a WEBAUTH Service execute with a REJECT. The alert is "WebAuthService: User 'B0-EE-7B-97-7F-33' not present in [Guest Device Repository](localhost)".
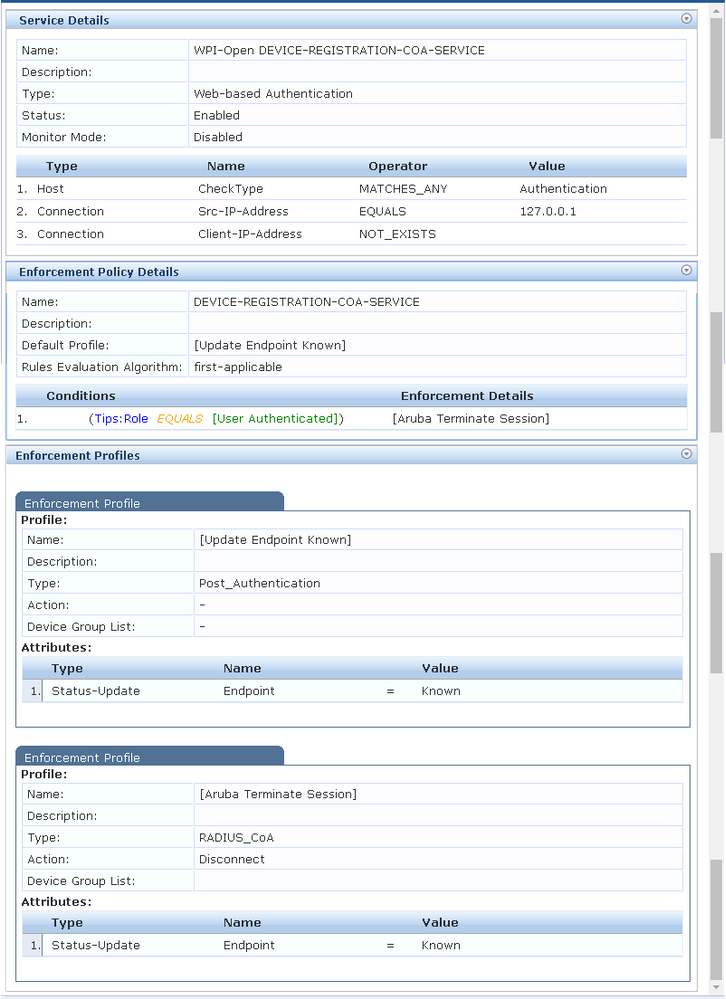
8) After the 600 second session time out, the device connects properly using the WPI-Open MAC-AUTH-SERVICE.
I've tried playing around with the API Explorer and using POST /api/device without the CoA flag, then using a PATCH /api/device/mac/XXXXXXXXXXXX with the CoA flag - with the assumption of let's create the Guest Device then CoA against it. But I don't see the "WPI-Open DEVICE-REGISTRATION-COA-SERVICE" execute in the Access Tracker on the PATCH.