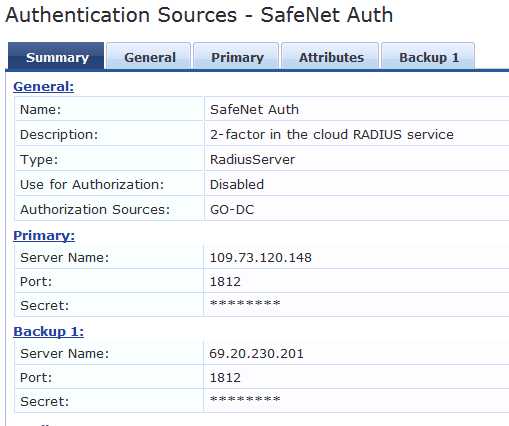
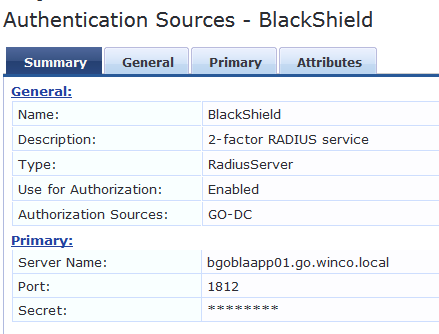
We've been using Blackshield for 2-factor RADIUS and are now moving to SafeNet.
I can authenticate users to one or the other, so now I'm ready to migrate.
To test, I built a service and put Blackshield in as a source and got it working, then I put SafNet in as a source and tested to make sure that worked too.
What I was hoping to do next is put them both in and have ClearPass try one and roll to the other if a user fails while we migrate users - the goal being to slip the change in without having to schedule a cut.
When I put both sources in the Authentication Sources box and click save, CPPM tells me that whichever one is first doesn't have an Authorization source set, so it must be listed last.
Both have Authorization sources, so I'm confused.
What am I missing?