Hi,
Sorry, I should have included this detail in the original post.
What radius server are you using?
- We are using ClearPass version 6.6.8
Did you configure it to send the chain of intermediates?
- I am not entirely sure of what you mean by this. I am assuming this is in regards to what certificates you upload into ClearPass?
- I can say that I have importanted the entire certificate chain in the CPPM and set the radius certificate as our commercially signed CA.
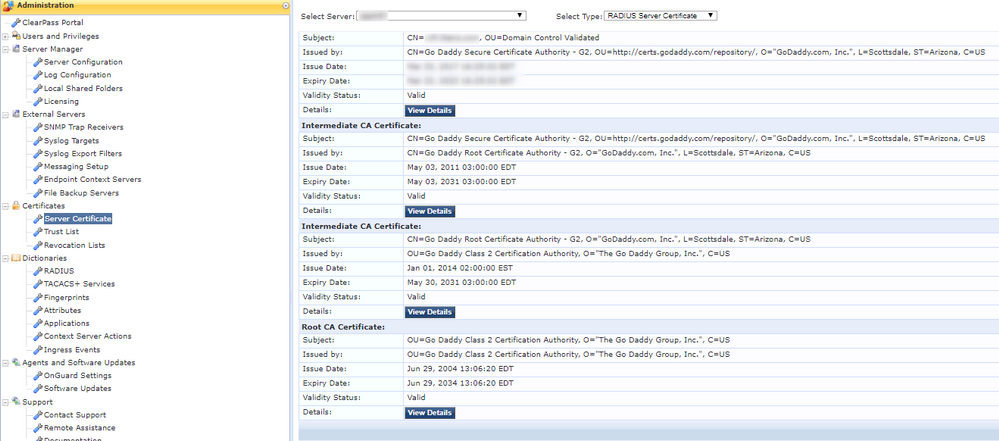
- I also imported the chain under Administration > Certificates > Trust List. All certificates in the chain are listed in the Trust List.
On our clients, by default the following two certificates are already there and trusted by default.
- Go Daddy Class 2 Certification Authority
- Go Daddy Root Certificate Authority - G2
In the wireless profile pushed by GP, I have set the policy to trust both of these certificates.
The only certificate in question now is the Go Daddy Secure Certificate Authority - G2. This certificate is not in any of the Windows certificate stores.
Given your explanation, it would appear that the clients only need to trust the root CA (Go Daddy Class 2 Certification Authority).
While I was testing the the Aruba tech we did a test and disabled the "Verify the server's identity by validating the certificate". When we did this, the clients were able to connect successfully leading us down the path that there is a certificate issue.
When we added the Go Daddy Secure Certificate Authority - G2 to the trust store on the clients, the clients were then able to connect. Would this then indicate that the ClearPass itself is not correctly sending the intermediate CAs?
Based on the wireshark screenshot above though, it appears as though the server is sending the entire chain, but the client is not responding.
Any ideas as to where the issues may be?