Hey guys,
Thanks a ton for the responses! The 'IF-MAP' feature was something that I was totally unaware of. It looks like it offers a more pin point finger print of what the device really is. Sounds like a great feature that I am definitely going to investigate and enable.
I just wanted to clarify on what I was trying to ask as I don't necessarily think I did such a good job on it.
Currently we use a custom attribute that is added to company owned Windows laptops. We do this to identify which devices have full access to our production network. Then in one of our Enforcement Profiles we use it to evaluate the user request. In order for a user to be allowed onto the wireless the request must come from a device which has this custom attribute (among other things).
When I look at the Event Viewer log I can see this attribute appear under the 'Computed Attributes'
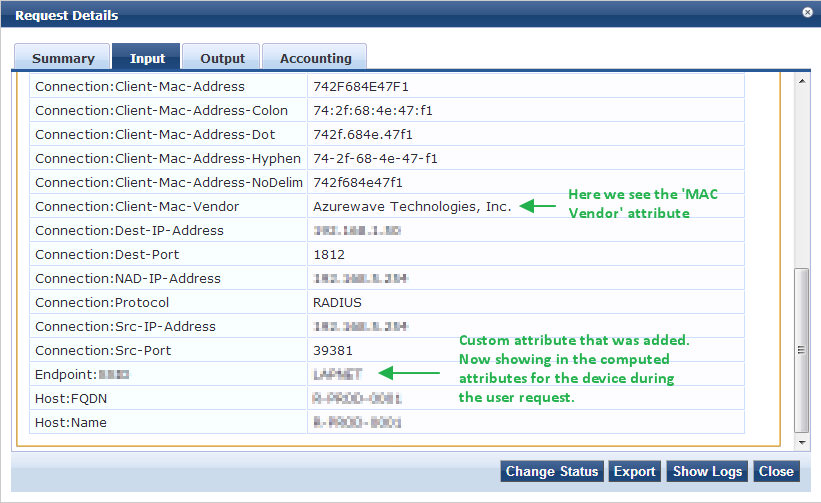
If I look at the rest of the 'Computed Attributes' I do not see any of the other attributes/parameters generated by DHCP FP that are available in the Endpoint Profile of the device itself. Below is a screenshot of the Endpoint Profile for the device which is being used to make an authentication request.

We do not Onboard these devices. We use EAP-PEAP to authenticate them.
If I look at the values that are available from the drop down list for 'Attributes'

I have marked the attributes that were added by us. Everything else in this list was already there. I believe this appears in the CPPM by default. These attributes are available to be evaluated in either your Role Mapping rules or in Enforment Policies.
Here is a shot from just an example Role Mapping rule
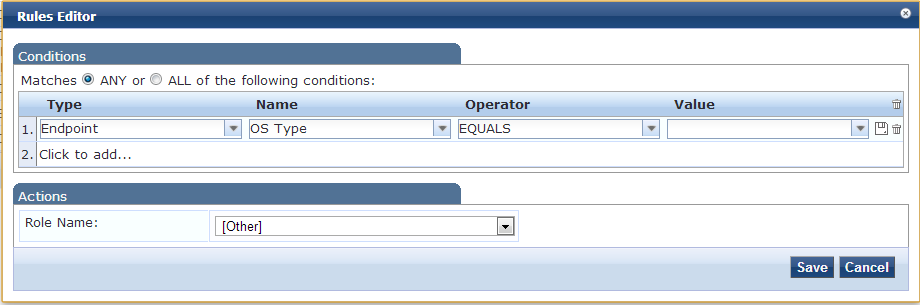
Okay so hopefully I am not completely making this confusing up until this point. I thin I am having a hard time explaining what's going through my head :(
We say that we can use the values that are computed via DHCP finger printing, HTTP analysis, etc. to evaluate requests. I have been under the impression that we can only use values that actually show in the client request (show in the Event Viewer). So if we go back the screenshot of the client request above, there is no value that tells me what the Operating System is for exmaple. But we have a parameter from DHCP FP which is 'OS Family' = 'Windows' in the Endpoint Profile.
And if we look at the Attributes in the drop down list the ones that would identify the OS for example might be 'OS Version' or 'OS Type'.
But in the values available from the DHCP finger printing there is no parameter called 'OS Type'. There is however 'OS Family'. So does 'OS Type' = 'OS Family'?
But even if it did, I don't think I could evaulate it because it isn't a 'Computed Attribute' contained within the Client Request. Because technically in the Endpoint Profile for the device the attribute hasn't been defined.
It would seem that when the attribues are 'computed' only attributes that have been defined in the 'Attributes' section of the Endpoint Profile can be used to do evaluation. The one exception to this (at least to me at this point) is the 'MAC Vendor' which can be evaluated using 'Connection:Client-Mac-Vendor'.
So to refine my original question. I don't think I am fully following how we can use the parameters generated by the DHCP FP, HTTP analysis, etc to evaluate a client request (with the exception of the 'MAC Vendor'). Aruba provides us a list in the drop down menu of the values that we can evaluate, we can add custom values, which great. But values generated by DHCP FP do not seem to be available.
Sorry for the long winded explanation! As I started to read your responses and go over my original question I started realizing maybe I didn't ask it correctly.
I don't think I did a much better job either, but hopefully I helped a little. There is probably something I am not getting!
Thanks again!
Cheers