This how-to configures RADIUS authentication on an AVOCENT ACS6000 console server running v2.5.0.10 firmware and integrating their authentication with a Clearpass version v6.4.4.70162 via Radius.
The AVOCENT device will be configured to give admin access to the users that belong to a specific Active Directory group.
- Clear Pass Configuration (v 4.4.70162)
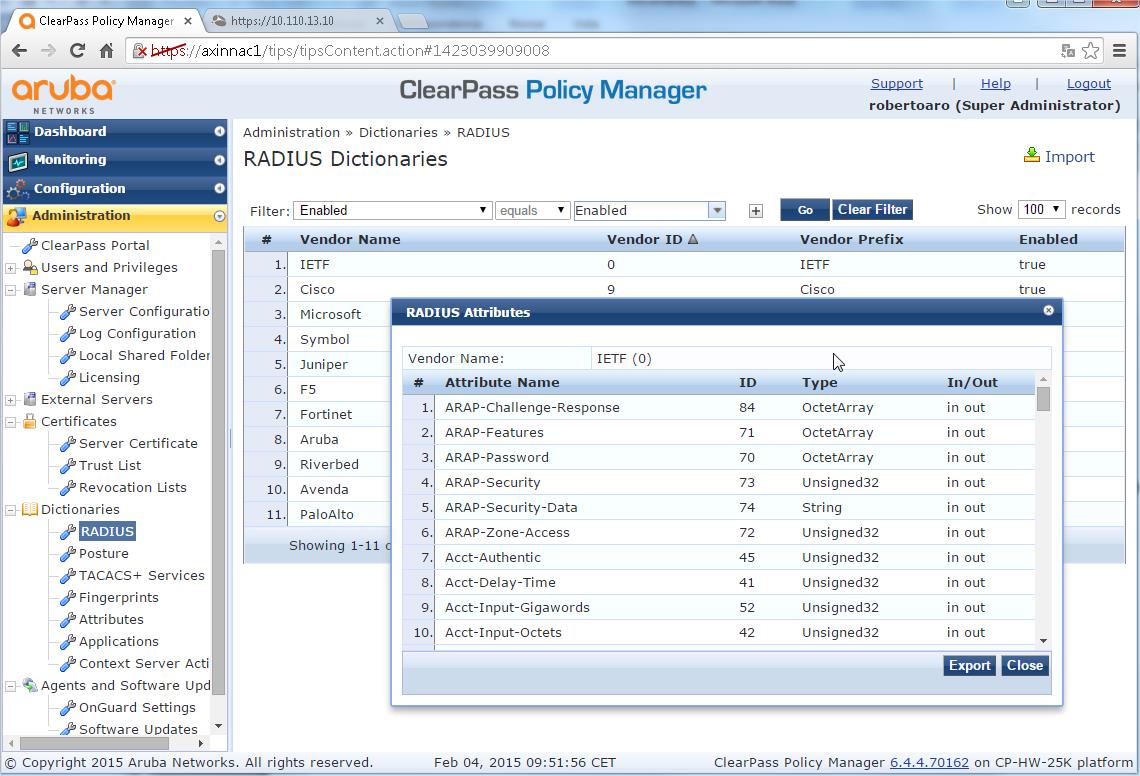
- Enabling the Radius Avocent Dictionary:
We do not need the Avocent ACS Dictionary installed inside Clearpass because we will use Radius: IETF standard attributes
- Add the Device to Clearpass:
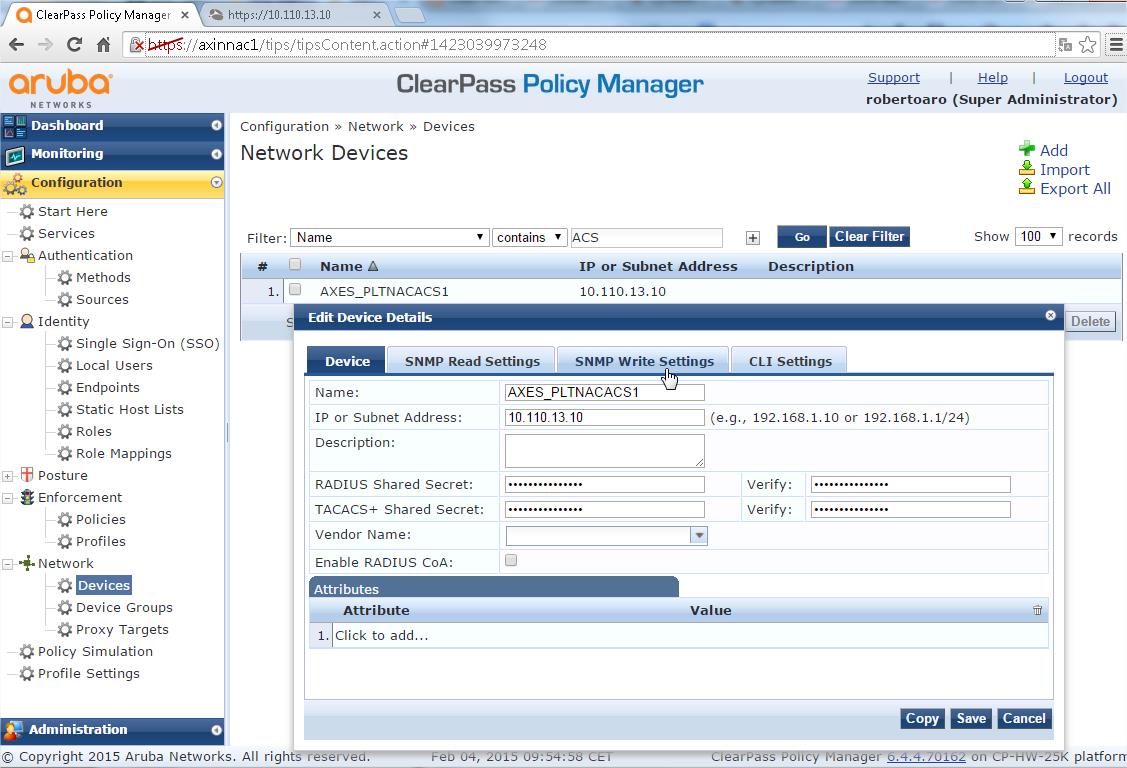
- Configuration > Network > Devices
- . Select "Add Devices"
- Name = <Name you'd like>
- RADIUS Shared Secret = <Your shared secret> & Verify = <Your shared secret again>
- Vendor Name = <Blank> (Vendor “Avocent” is not included inside the predefined list)
- Select "Save"
- Add the Device to a New Device Group:
Using device groups for everything in Clearpass is the best option to organize devices. This step is OPTIONAL
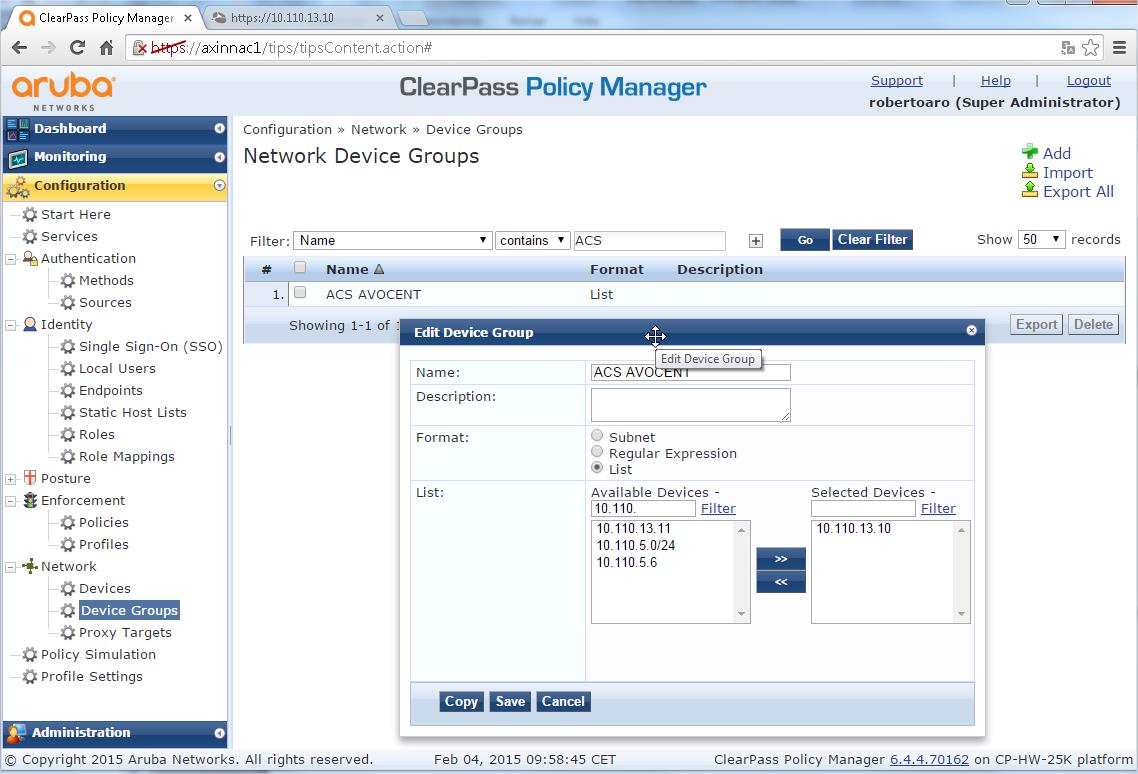
- Configuration > Network > Device groups
- Select "Add Device Group"
- Fill in the "Name" field. I'll be using "ACS AVOCENT" in this example
- Select "List" under "Format"
- Under the "List", move the Avocent Device (Their IP address will be listed) from the "Available Devices" to "Selected Devices"
- Click "Save"
- Create an AVOCENT Enforcement Profile:
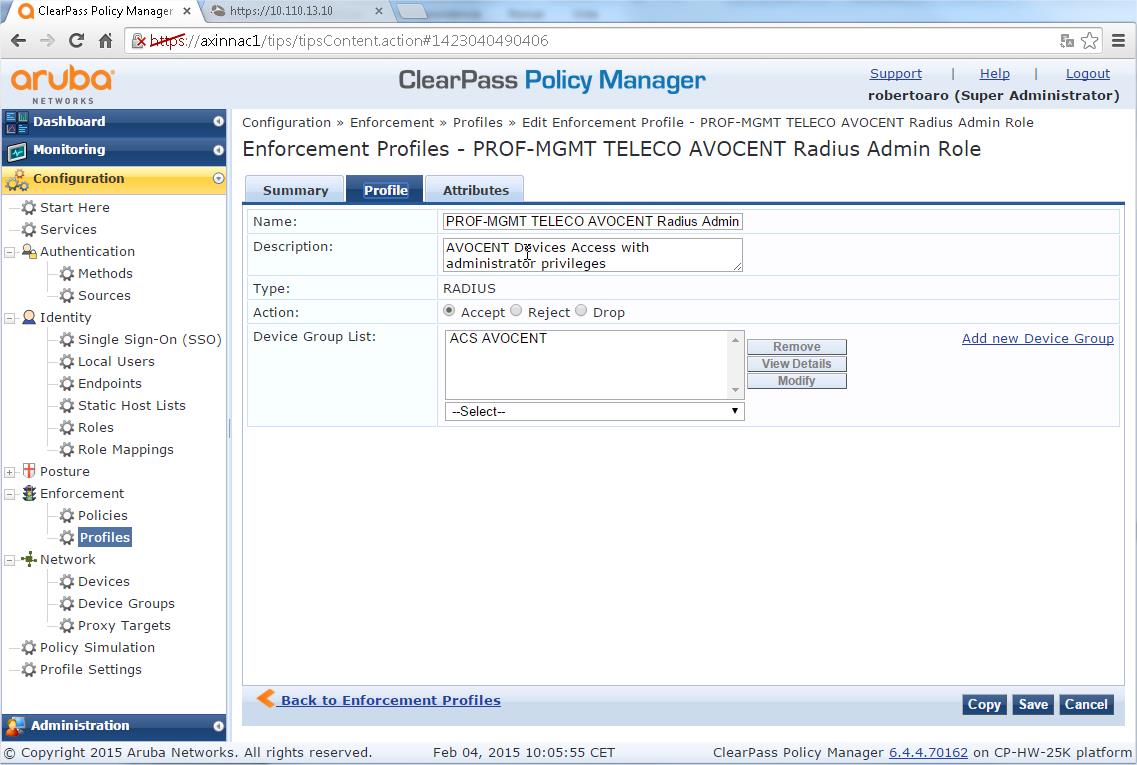
- Configuration > Enforcement > Profiles
- Click "Add Enforcement Profile"
- Select "RADIUS based enforcement" as the Template
- Under "Profile" TAB provide a name, "AVOCENT RADIUS Admin" or similar
- Make sure that "Accept" is set under "Action", the Description filling field is optional
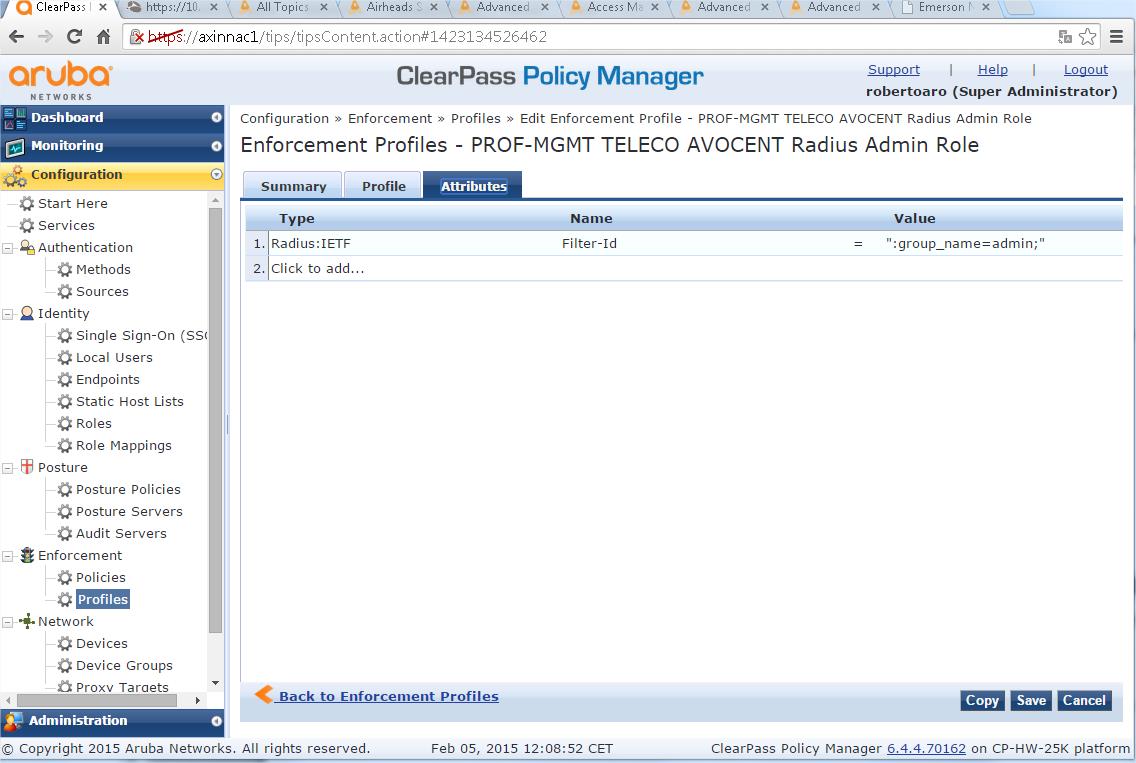
- Under Attributes TAB (THIS IS THE KEY, if you know what we are doing, this is the information you are looking for):
- Type - "Radius: IETF" (we will use a standard IETF Attribute)
- Name - "Filter-Id",
- Value - ":group_name=admin;"
VERY IMPORTANT STEP: The Users Group named "admin" is configured by default inside your AVOCENT devices. You could define a different Users group name (for example the “group-access-console-port-one"). Then, you should define the additional Users Group inside the AVOCENT devices assigning the specific privileges to the group.
- Create a AVOCENT Enforcement Policy:
- Configuration > Enforcement > Policies
- Click "Add Enforcement Policy"
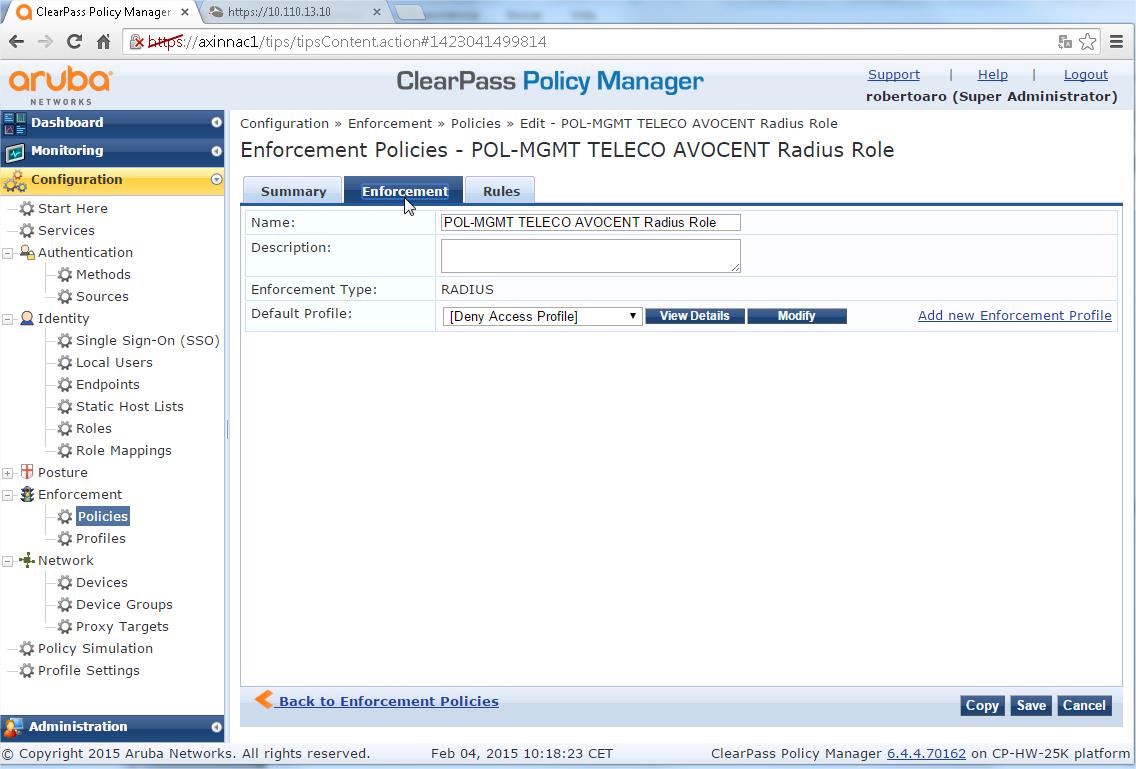
- Under "Enforcement" TAB, provide a name, "AVOCENT Login Enforcement Policy" or similar
- Verify that RADIUS is the "Enforcement Type", as you can not to modify lately this parameter (you should delete and create a new Enforcement Policy if you do not define the right Type)
- Select "[Deny Access Profile] for the "Default Profile
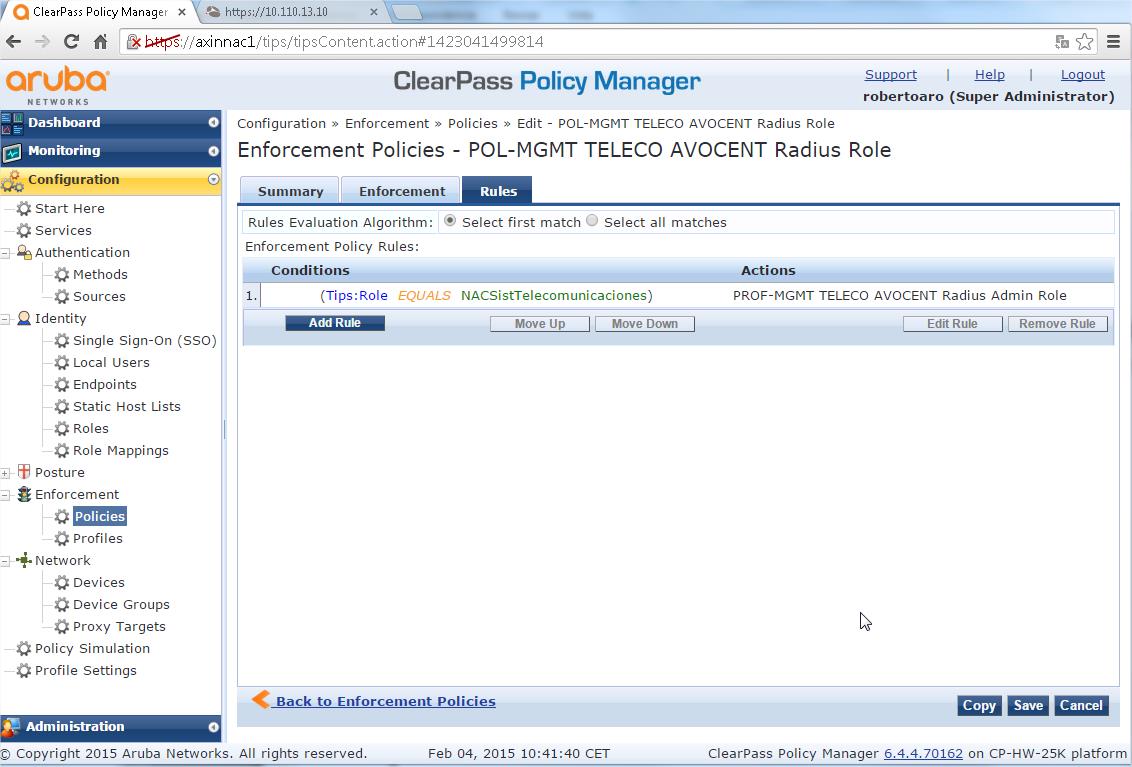
- Select "Rules" TAB and click "Add Rule"
- You should apply the previously defined profile with the condition defined in your organization (typically you will use one AD group membership to assign the role), this is a sample with the AD group "NACSistTelecomunicaciones":
- Type - Tips
- Name - Role
- Operator - EQUALS
- Value - NACSistTelecomunicaciones
- Enforcement Profiles > "Profile Names" > "PROF AVOCENT RADIUS Admin", ie the Enforcement Profile you defined previously
- Click "Save" to Save the Rule
- Click "Save" again to Save the whole Policy
VERY IMPORTANT STEP: You could define additional Rules (repeating the Rule creation Steps) to associate the remaining user groups with other AD groups following your convenience.
- Create a AVOCENT Radius Login Service:
- Configuration > Services
- Click "Add Service"
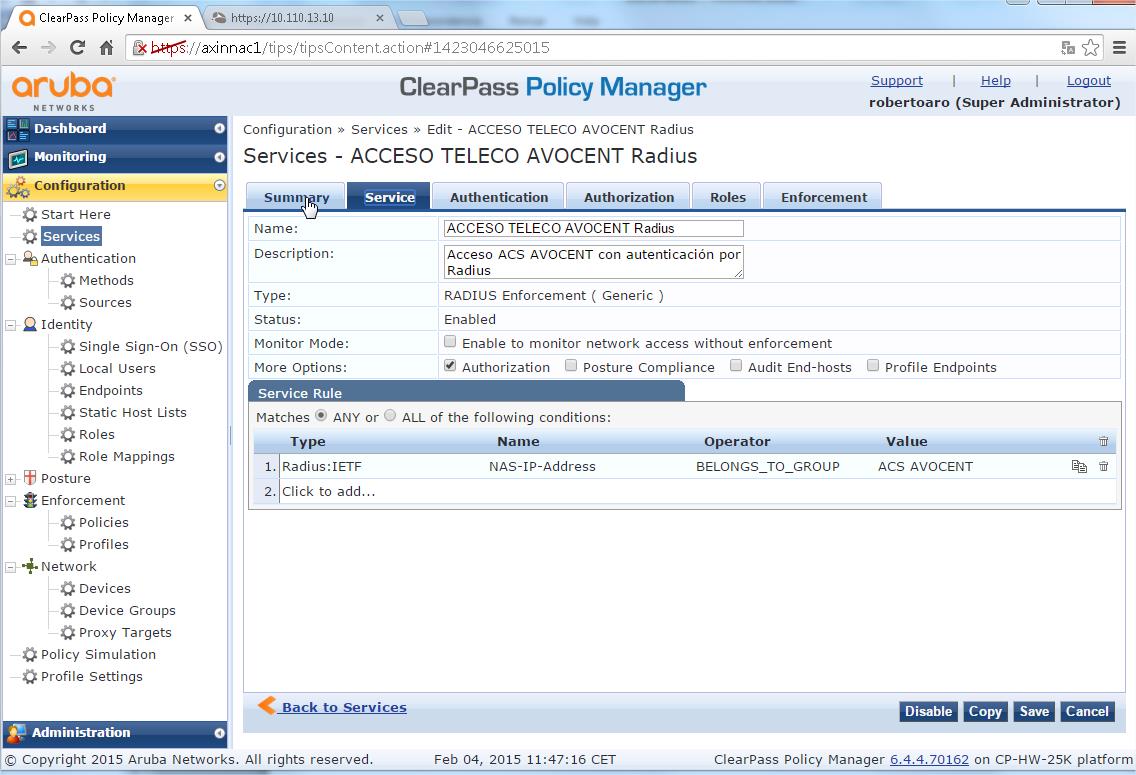
- Select "Type" of "RADIUS Enforcement ( Generic )", as you can not to modify lately this parameter
- Provide a name for the service, "AVOCENT ACS Login", the Description field is optional
- Under "Service Rule" enter the following:
- Type - Radius:IETF
- Name - "NAS-IP-Address"
- Operator - "BELONGS_TO_GROUP"
- Value - "ACS AVOCENT"
VERY IMPORTANT NOTE: You could reach the same goal using the condition Connection:NAD-IP-Address "BELONGS_TO_GROUP" "ACS AVOCENT". The Key here is that the Value corresponds with the Device Group Name you defined previously.
- Under Authentication:
- Authentication Methods - PAP
- Authentication Sources - <your AD>
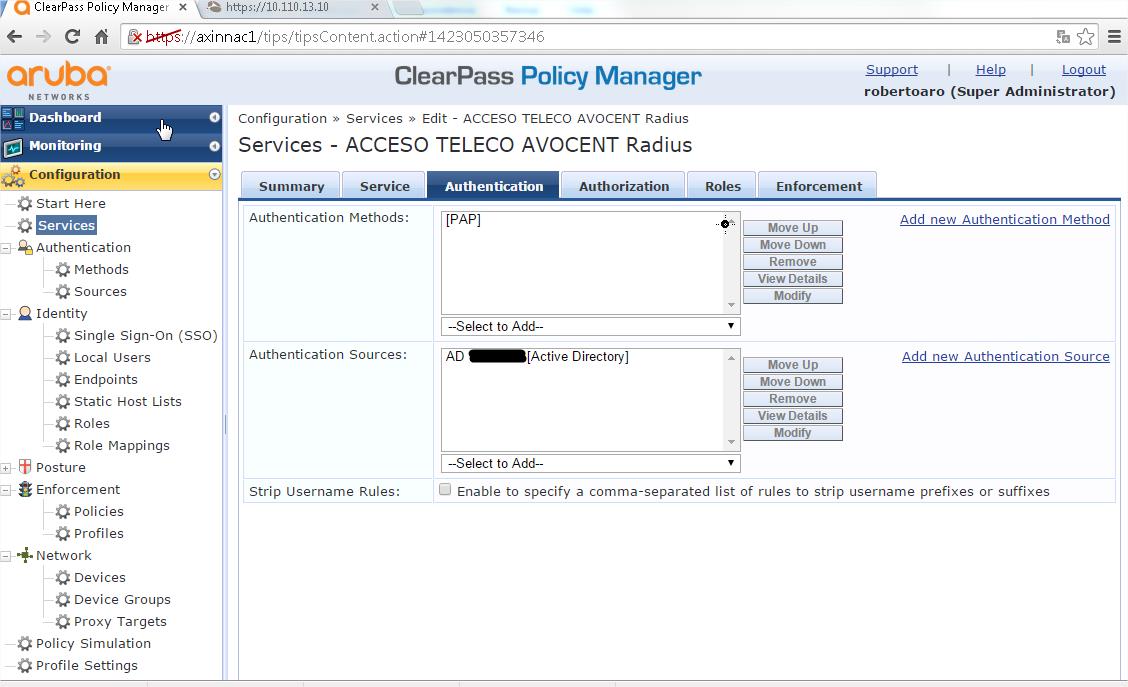
- Under "Enforcement" > "Enforcement Policy" select the enforcement policy that we created > "POL AVOCENT Login Enforcement Policy"
- Click "Save"
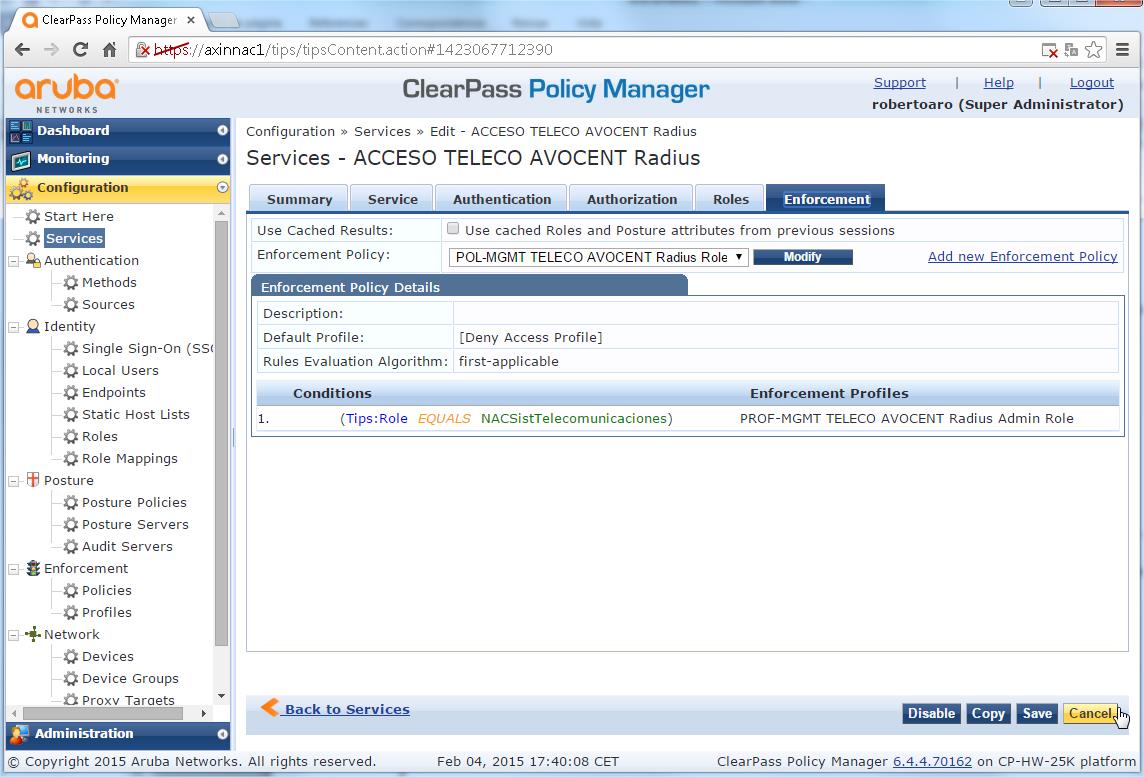
- You should click on the red dot to enable the Service (it becomes a green dot) and you should reorder (clicking on Reorder button) the Services according to your deployed Service Rules to avoid troubles.
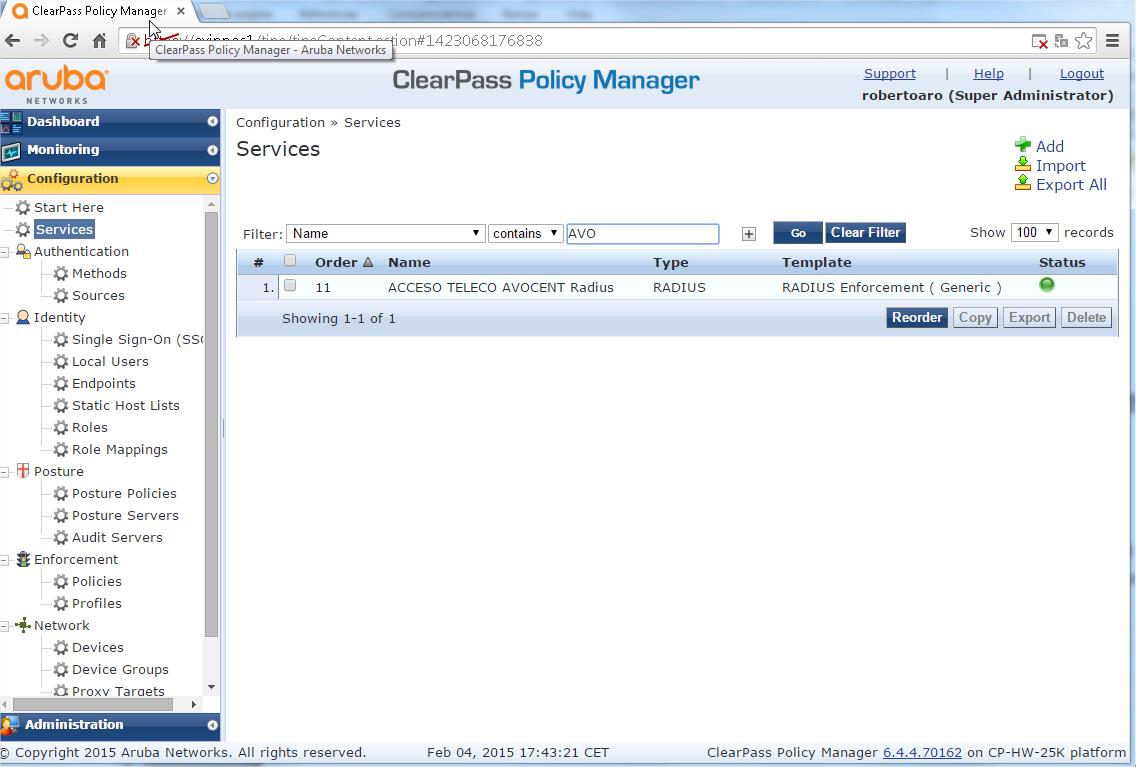
With this steps we have finished the ClearPass initial configuration needed for integrate with the Avocent device. The configuration could be extended with more roles with different privileges to comply with your organization needs.
- Avocent Configuration (v 2.5.0.10)
The configuration steps below will be done through the GUI.
Also we will include the CLI commands, but they will be simply listed, assuming enough Avocent CLI knowledge (it is a bit tricky and it is not very well documented).
- Go to System > Security > Security Profile
Change the Security Profile to use "Port Access by Controlled by authorizations assigned to user groups" above Serial Devices paragraph and press "Save"
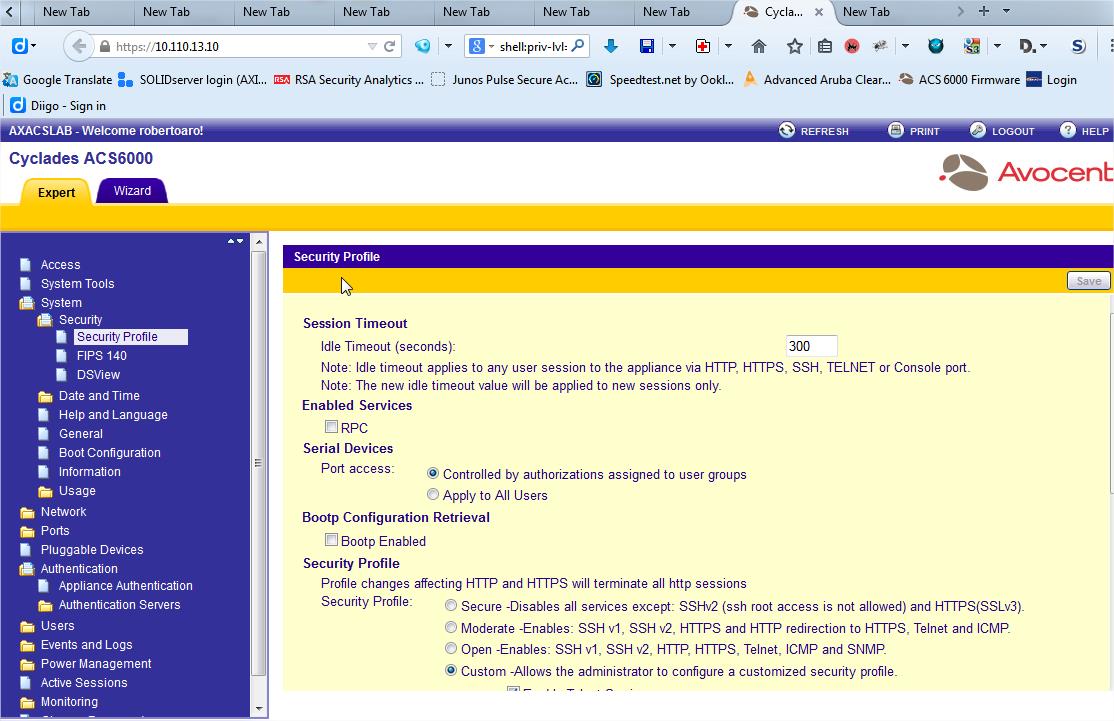
cd /system/security/security_profile
set port_access=port_access_per_user_group_authorization
2 Configure the Authentication Type to RADIUS/LOCAL in the Appliance Authentication sheet under Authentication Folder
Note: The "Enable fallback to Local type for root user in appliance console port" is optional, but it is strongly recommended.
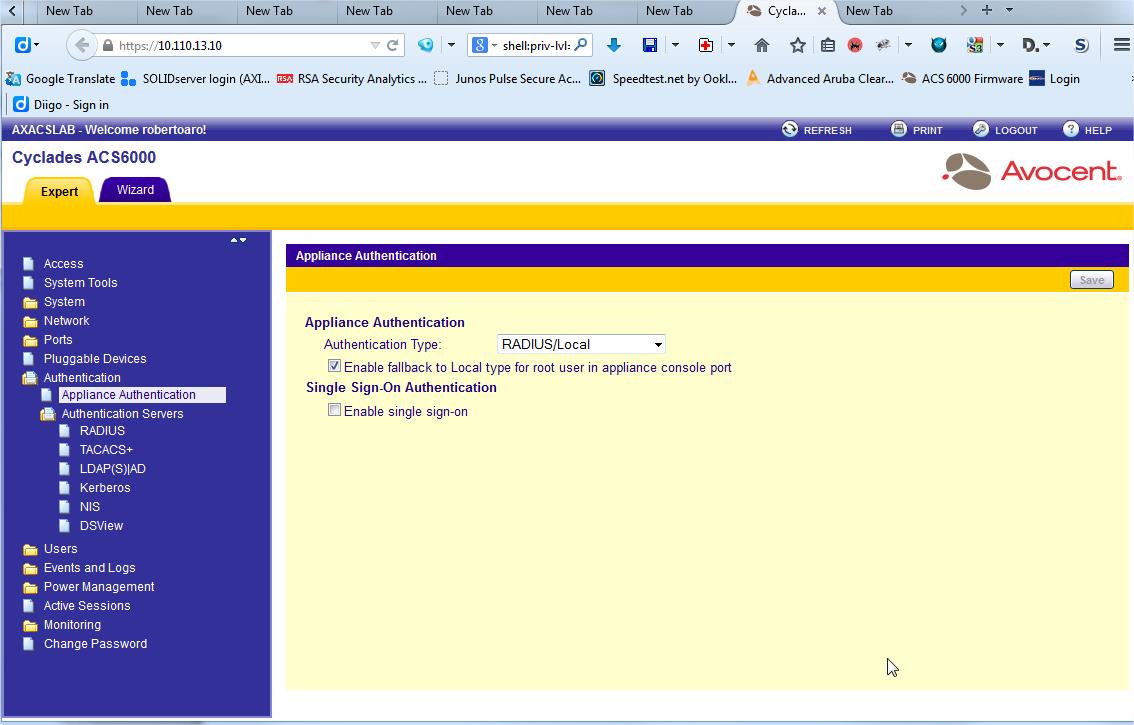
cd /authentication/appliance_authentication
set authentication_type=radius|local
set enable_fallback_to_local_type_for_root_user_in_appliance_console_port=yes
VERY IMPORTANT NOTE: You could reverse the change selecting the Authentication Type to LOCAL in the Appliance Authentication. It is better to no close the administration session, especially if the device is located in a remote place ;)
3 Configure Authentication Servers (again under Authentication Folder) to use your ClearPass servers as RADIUS servers and enter necessary parameters, and then, press "Save". In this example, the Authentication Server and Accounting Server is the same machine.
Note: There is no need to enable the Service Type Attribute since the Group Authorization will be set.
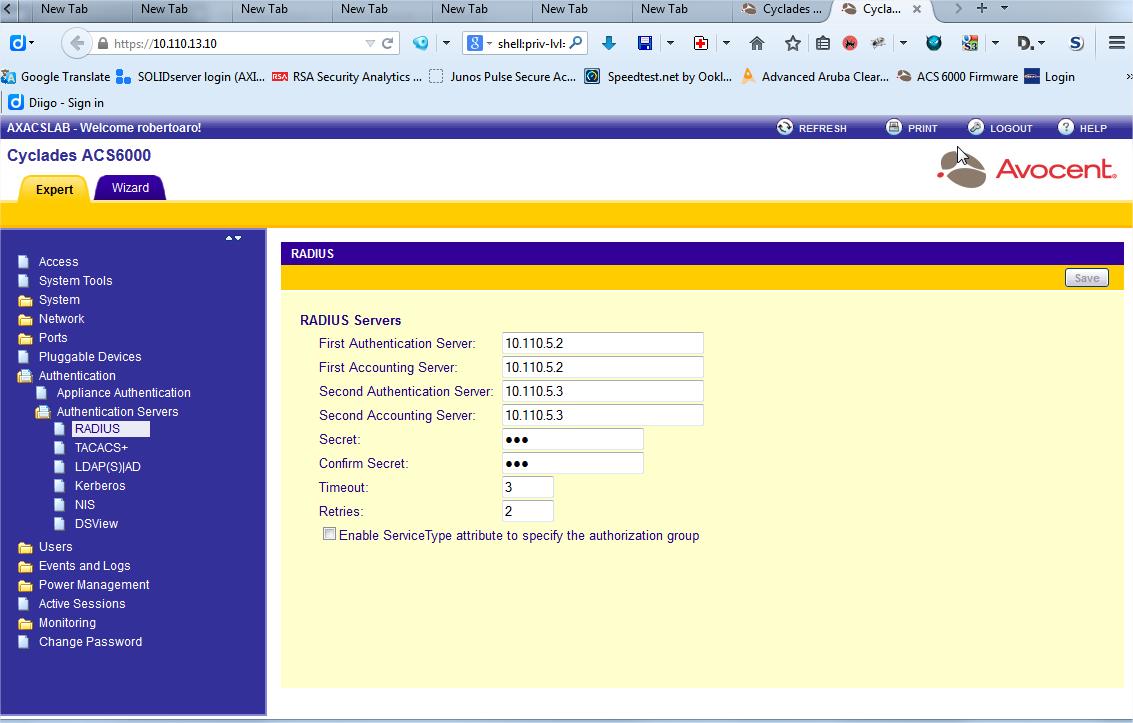
cd /authentication/authentication_servers/radius
set first_authentication_server=10.210.5.2
set first_accounting_server=10.210.5.2
set second_authentication_server=10.210.5.3
set second_accounting_server=10.210.5.3
set secret=xxxxxxxx
set timeout=3
set retries=2
set enable_servicetype=no
4 OPTIONAL: Create a new Authorization Group to control serial access and permissions. Note: In this example, we named the Authorization Group as ‘RadiusAdmin’. If you want directly ALL the privileges you should use the predefined “admin” User Group
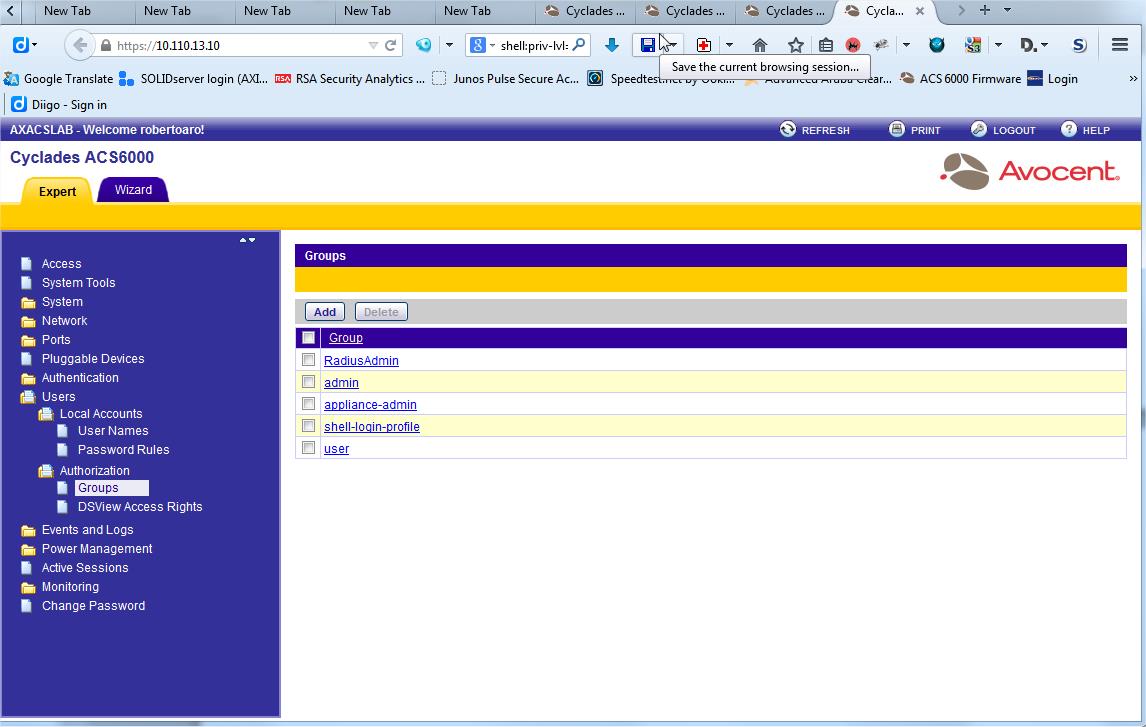
cd /users/authorization/groups
set name=RadiusAdmin
It is possible to assign the particular privileges using the CLI, however it is a bit tricky and a bit time consuming.
Now the Avocent device is also configured and it is time to try your new config.
Please, let me know if this how-to help you.
Anyway, this is the first approach to this problem, very common in my organization. If people liked, the howto improvements could be numerous: single sign on with the remote device console accessed will be the next one I understand it could be very interesting. Please, let me know your interest about possible how-to extensions (you could grant me Kudos, but it is only an idea ;)).