Well this is actually a conversation that has come over from the S3500 side of things, so hopefully it is still relevant.
So far the logon lifetime timer being set to 1 min is working for us.
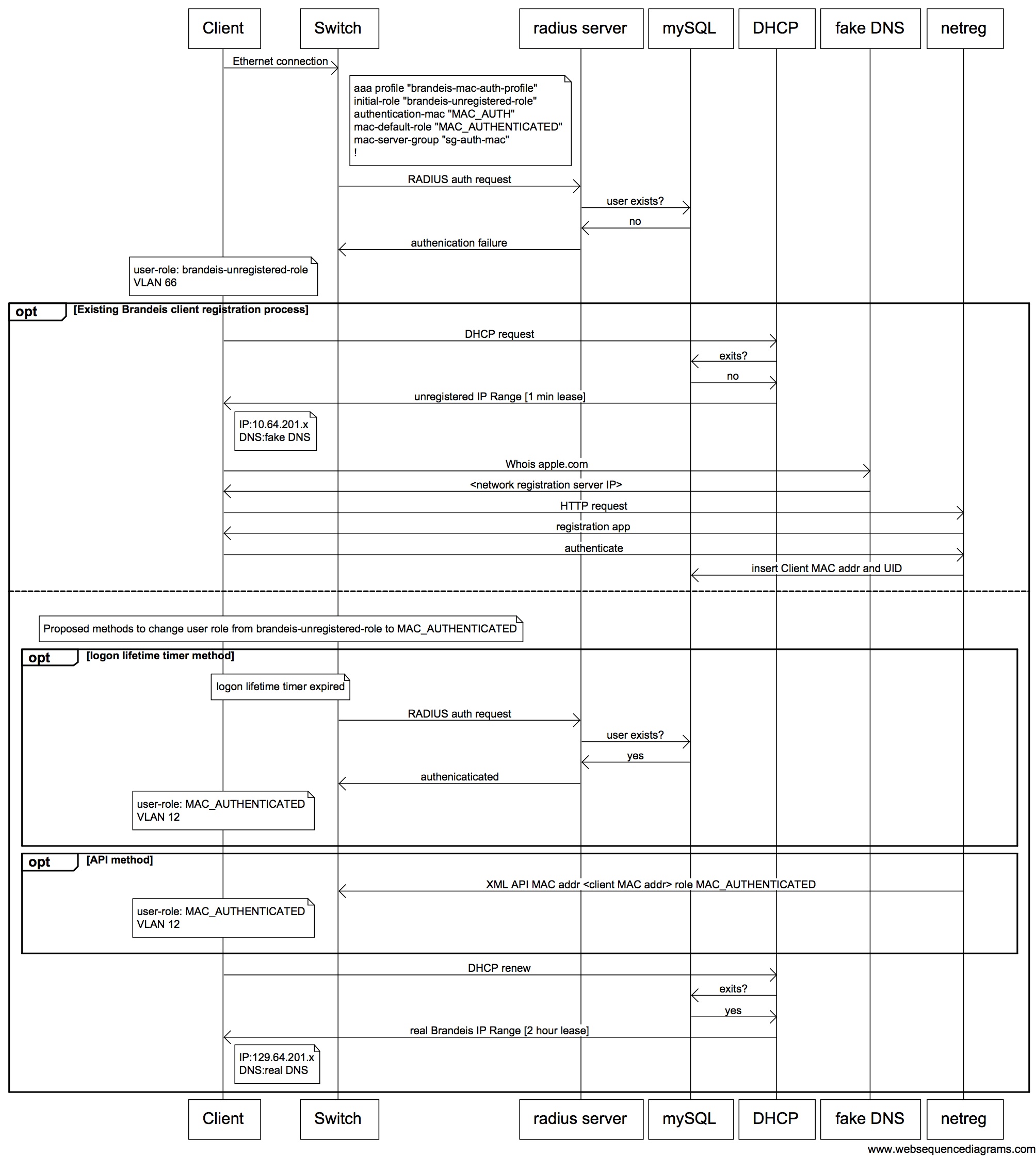
What Brandeis is trying to accomplish is to have a user in a mac auth profile re-attempt authentication every min after a failure. Why? Because we have device registration server that uses a captive portal to register the users mac addr. Once the registration is successful the user needs to have the role changed. When a user is in the default role for the aaa profile the re-auth timer won't trigger.
What I have seen is that this DOES work. (we are on AOS 7.1.1 (mobility switch))
Feb 14 12:11:36 :522005: <INFO> |authmgr| MAC=00:24:e8:a9:55:6a IP=10.64.129.105 User entry deleted: reason=logon role lifetime reached
Feb 14 12:12:36 :522005: <INFO> |authmgr| MAC=00:24:e8:a9:55:6a IP=10.64.129.105 User entry deleted: reason=logon role lifetime reached
That user was not in the logon roll but a default roll from the aaa profile.
Here is a time diagram of what happens.