Thanks for staying with me on this, Colin. I really appreciate it.
So to answer your questions, yes, the correct Service is being hit, however it isn't working as planned.
Here's what I'm trying to do...I only want peripheral devices that can't do .1x (VoIP phones, Aruba AP's and Printers) to be authenticated against the Endpoints DB. To avoid any spoofing, one of the criteria in the Enforcement policy is that the entry in the Endpoints DB has to be marked as "known", as well as the OS Family must match the device type, i.e a device posing as an Aruba AP must be fingerprinted as using the Aruba OS. All of these extra caveats are simply to prevent spoofing. I don't want to inject roles and dynamic vlans correlating to those roles. I want the switch ports to run the show for VLAN assignment. I want ClearPass to say "yes, it's a known peripheral. turn the port on" or "no, I don't know who you are, keep the port off".
So while testing all of these settings I've created the following service (I'm still using ACE in the title since you were here last year :-)
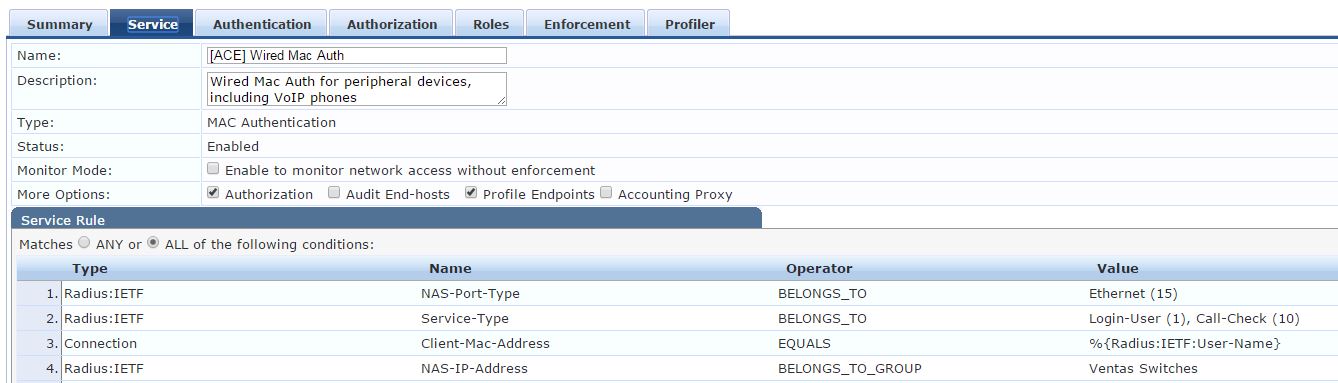
Authentication Tab
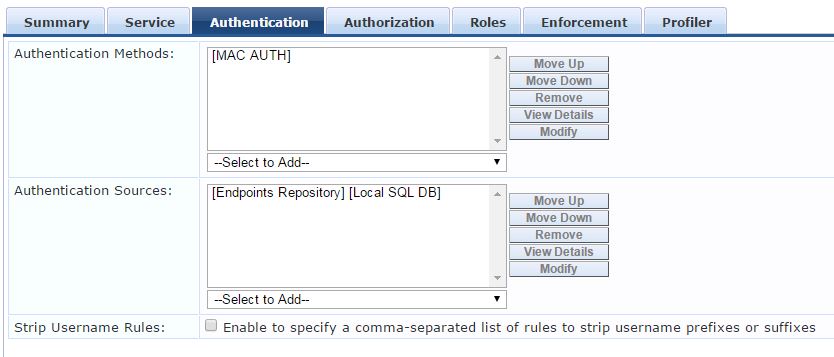
Authorization Tab
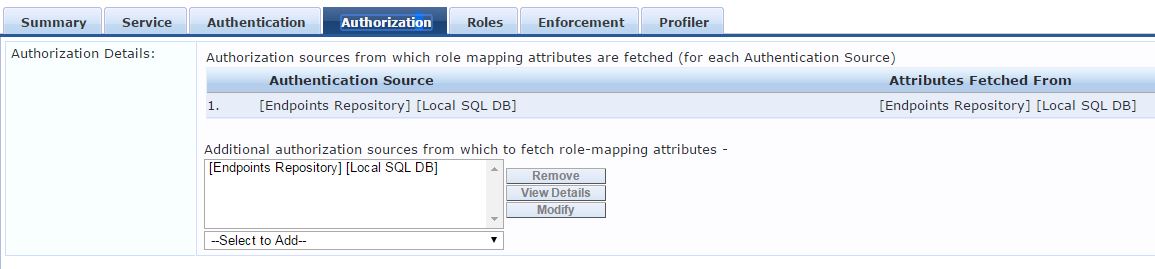
Roles Tab (not really using them, but just in case I have this in there):
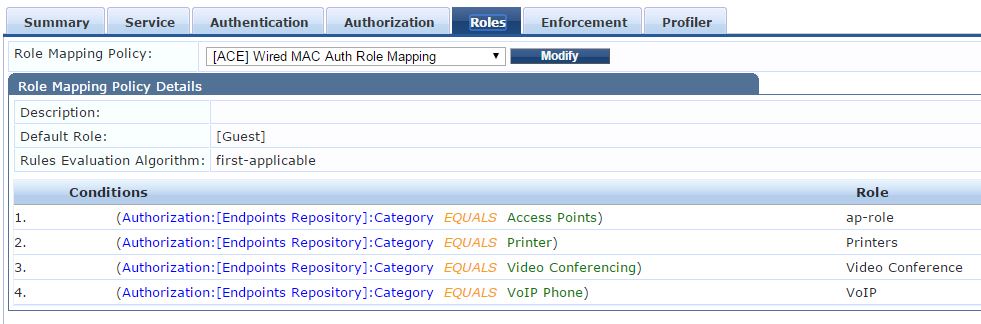
Enforcement Tab
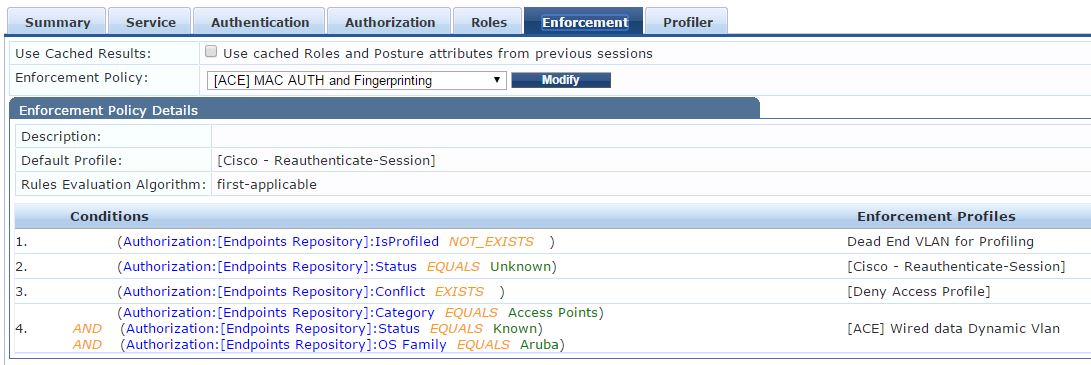
Enforcement Profile 'Dead End VLAN for Profiling' (VLAN 999 is a null VLAN with IP Helpers pointed to ClearPass only)
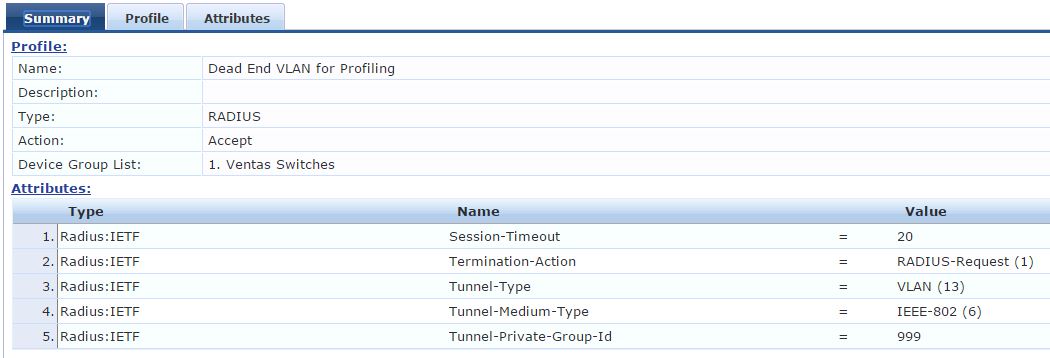
Enforcement Profile '[ACE] Wired data Dynamic Vlan' (the %{Device:data} value uses the configuration of the switch port vs. a dynamic VLAN assignment from ClearPass).
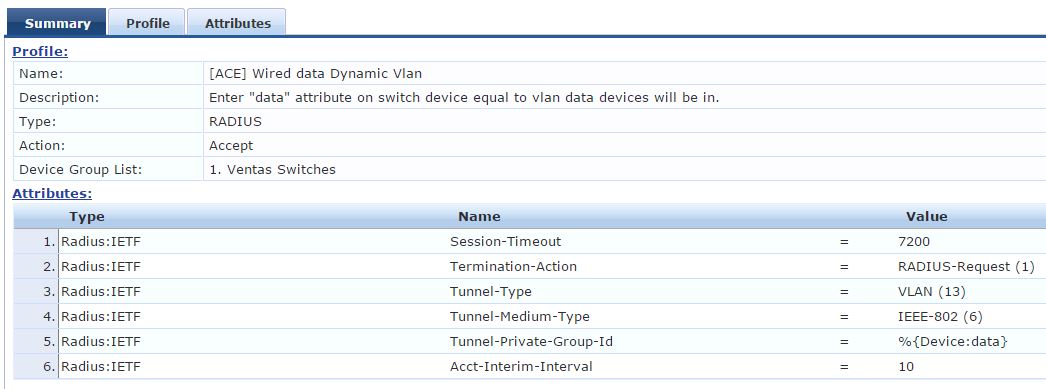
...and lastly, the Profiler Tab
So after plugging in the AP with all of the setttings above in place, here is what I get in Access Tracker (x3 times):
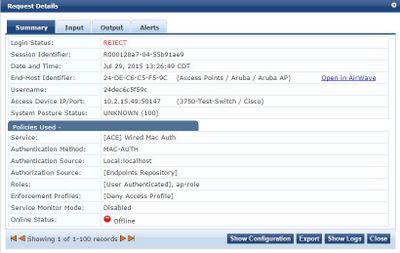
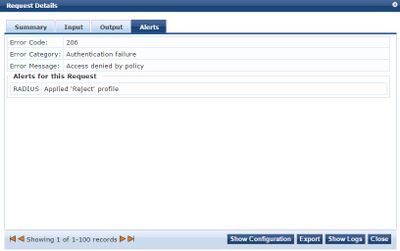
...and the device never gets fingerprinted
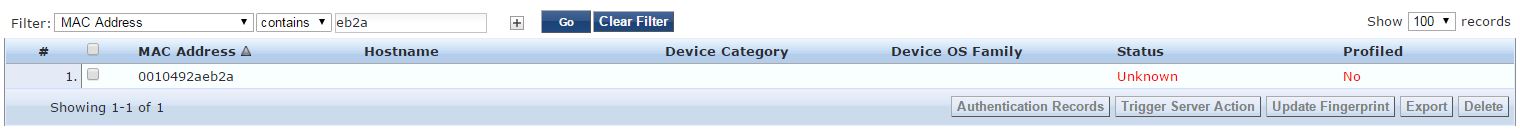
**It should be mentioned that yes, during testing I delete the entry from the Endpoints DB **
Things I've noticed:
1. When I change the method to 'Allow All MAC Auth' in the Authenticaton Tab the device gets fingerprinted and stays in the status of "unknown". However it is let on all the way as if ClearPass wasn't even in the mix.
2. Having the first rule in the Enforcement Policy of "If the device is not profile in the Endpoints DB, assign the device this NULL VLAN so it can get profiled" does nothing.
So I'm still at a loss on the flow. If all devices are to MAC Auth against the endpoints DB, how is any authentication possible if the device isn't profiled? What is it authentication against? With DHCP being L3, as well as DHCP being the process by which a device is fingerprinted and the Endpoints DB populated, how can an authentication take place on L2 when the L3 activities haven't happened yet? Forgive my ignorance, but this is simply not clicking for me.