Hello! I was struggling few days ago to give a solution to this, the idea of dekvn helped me alot, see below what I did:
My case: The WLC request re authentication to the Clearpass with aleatorias time (it is a Ruckus WLC, there is no option to configure reauth timer), the cache police has been expired, so the clearpass responded with a limited ACL (the posture was unknown). The onguard agent in the cliente device keeps showing healthy(because for the agent, there is no new auth request (bounce)), but the client was with a limited ACL.
Solution:
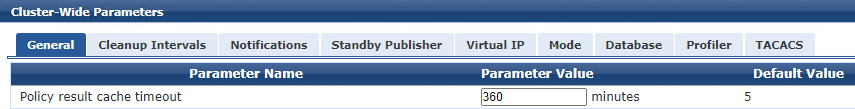
1. Increase the time of policy cache to 6 hours(Administration --> Server Manager --> Server Configuration --> Cluster-Wide Parameters). Policy result cache timeout).
This will tell to Clearpass hold the posture token for 6 hours, the token will only change in less than 6 hours if the onguard agent tells it to the Clearpass (e.g.: Machine was healthy, and now is quarantine).
2. Create an endpoint attributes called 'last-posture' (I'm Brazilian, so is in portuguese 'Ultima Postura') (Administration --> Dictionaries --> Attributes). Entity: Endpoint / Type: String)

3. Create three enforcement profiles (Configuration --> Enforcement --> Profiles). The template is 'ClearPass Entity update enforcement':
(Post_authentication)
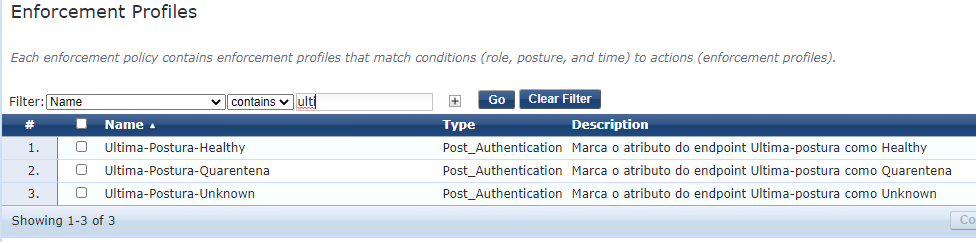
These three enforcement will fill the field created in last step with the last posture
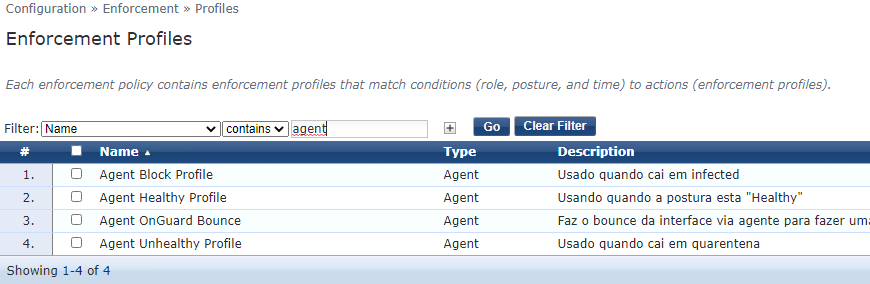
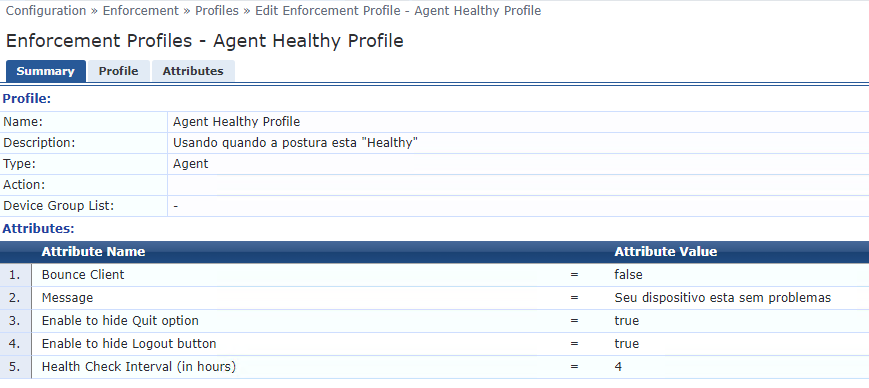
4. Create one enforcement profiles only for Bounce through onguard agent (Configuration --> Enforcement --> Profiles). The template is 'agent enforcement':
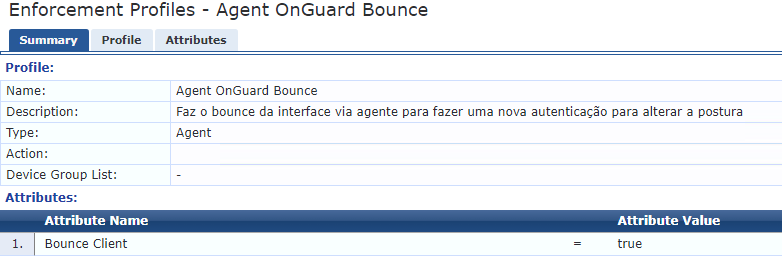
I'm assuming that you already had create the health/quarantine enforcement, I'm showing below the agent enforcement that I have
5. Add to healthy enforcement, the option "Health Check Interval" to 4 hours. - The Agent will generate a new log in access tracker every 4 hours.
Observe that bounce cliente = False. (we will use other enforcement to bounce the client when necessary).
Now all the 'backend magic' is completed, let's see the necessary changes in services now.
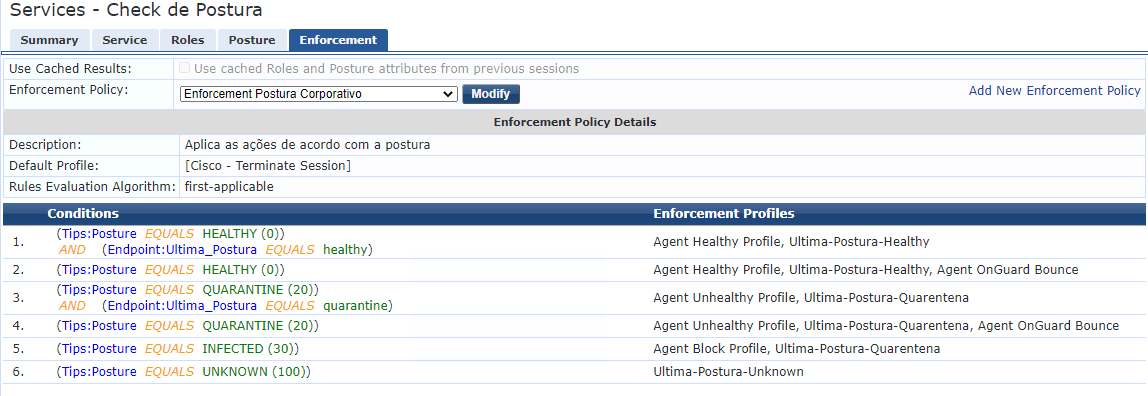
6. Change the enforcement of web based service of onguard to use the last posture
So... if the posture is Healthy and last posture is Healthy -> Do not take action and update the field last-posture to 'healthy'
If the posture is Healthy but the last posture IS NOT healthy -> Update the field last-posture to 'healthy' and SEND BOUNCE
If the client still healthy, I don't need to send COA or Bounce to the agent, so the Health Check each 4 hours, is transparent to the client.
Observe that I never send CoA to the device, all the changes occurs using the OnGuard Agent Bounce feature.
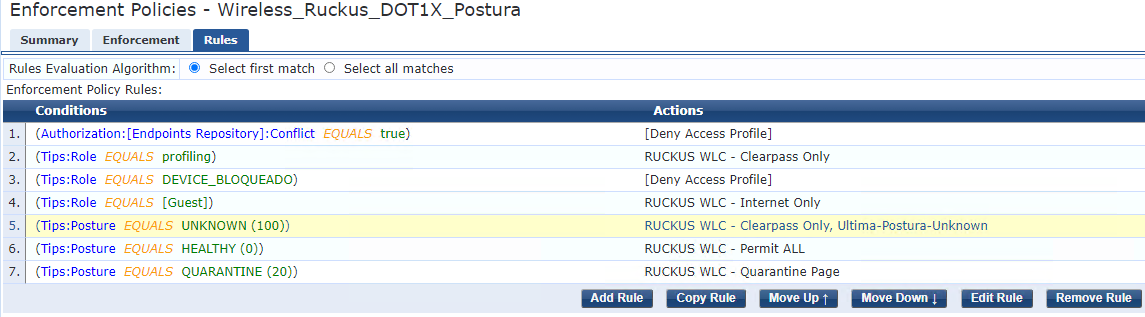
7. Now is necessary to change the enforcement of 802.1x service, I only need to add the enforcement 'ultima-postura-Unknown' when the posture is 'unknown'
(Healthy and Quarantine will be updated by the web based onguard service)
And that's it!
Clearpass will hold the token for 6 hours
Onguard will send info to the Clearpass each 4 hours
If posture of client still the same, no Bounce/CoA is sent
If the WLC ask Clearpass for client reauthentication, Clearpass will send the correct ACL based in last-posture
If the client went home, and come back after 6 hours, the 802.1x service will mark his token as unknown, forcing a Bounce when the Onguard web based service run.
I hope this helps someone with the same problem!
------------------------------
Bruno Andrade - ACMP, ACSP, ACCP, CWNA, CCNA R&S, RCNA, ICX, SPSX
------------------------------
Original Message:
Sent: May 05, 2021 11:14 PM
From: Richard Benedict Santero
Subject: Onguard without bounce / terminate session
Hi just starting doing the OnGuard, could you perhaps elaborate on how this will look in the Clearpass GUI?
------------------------------
Richard Benedict Santero
Original Message:
Sent: Nov 18, 2016 02:47 AM
From: Kevin Lauwerijs
Subject: Onguard without bounce / terminate session
A CoA is needed to make sure the switch applies a new role. This solution doesn't send a CoA when nothing has to change so there's no interruption. This is what I did:
1. Create a custom attribute named 'Last Health' (Administration --> Dictionaries --> Attributes). Entity: Endpoint / Type: String.
2. Create a post enforcement profile named 'Mark as Healthy'. Add the attribute created in step 1 with value 'Healthy'.
3. Create a post enforcement profile named 'Mark as Unhealthy'. Add the attribute created in step 1 with value 'Unhealthy'.
4. Edit the Onguard enforcement policy with conditions set in this order:
1 When Posture is not Healthy AND Last Health = 'Unhealthy' --> No CoA
2 When Posture is not Healthy --> 'Mark as Unhealthy' + CoA
3 When Posture is Healthy AND Last Health = 'Healthy' --> No CoA
4 When Posture is Healthy --> 'Mark as Unhealthy' + CoA