I'm trying to setup VLAN enforcement on a Cisco SG300 - the swich is logging:
11-Aug-2014 14:16:56 :%SEC-W-SUPPLICANTUNAUTHORIZED: username teststudent with M AC 00:11:25:d8:42:83 was rejected on port gi2 because Radius accept message does not contain VLAN ID
11-Aug-2014 14:16:56 :%AAAEAP-W-RADIUSREPLY: Invalid attribute 65 ignored - tag should be 0
11-Aug-2014 14:16:56 :%AAAEAP-W-RADIUSREPLY: Invalid attribute 64 ignored - tag should be 0
The Clearpass Access-Accept message looks like this:
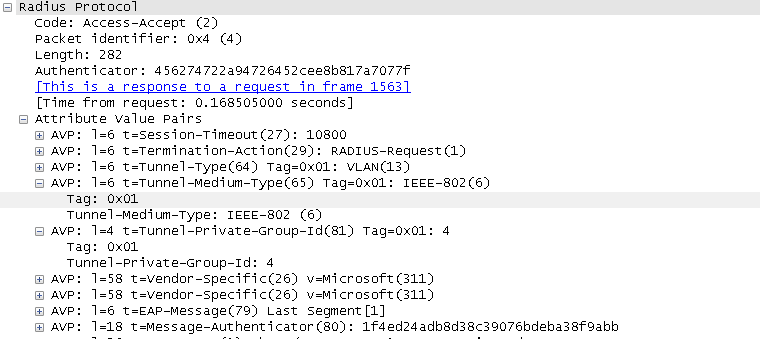
Cisco documentation notes:
As noted in RFC2868 , section 3.1: The Tag field is one octet in length and is intended to provide a means of grouping attributes in the same packet which refer to the same tunnel. Valid values for this field are 0x01 through 0x1F, inclusive. If the Tag field is unused, it must be zero (0x00). Refer to RFC 2868 for more information on all RADIUS attributes.
It would seem that Clearpass is using the tag appropriately since the value pairs all do indeed reference the same tunnel. I'm guessing the Cisco switch is logging "rejected on port gi2 because Radius accept message does not contain VLAN ID" simply because of the "invalid attribute" for tunnel-type and tunnel-medium-type.
Anyone have any insight into this? Is there a way to set the tag to 0x00 instead of 0x01?
Thanks,
Aaron