Sure we have all heard of 802.1X, but how does it work? What are the necessary items required making the authentication successful? Stay tuned
802.1X is a layer 2 port based network access control process originally defined in 1998 in IEEE standard 802.1d-1998. The latest standard is 802.1X-2013
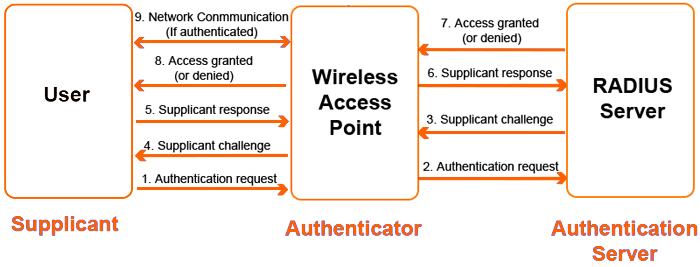
Any .1X network will have 3 working participates. (Sometimes the Authenticator can also be the Authentication Server)
- Authentication Server –Typically a RADIUS server*- contains or accesses a database to check credentials of a user then relays the info to the authenticator to allow or deny access.
- Authenticator – Allows access to the network and communicates with the Auth. Server.
- Supplicant – The client device attempting to get access into the network.
Authentication Process
The process is similar to getting into an invitation only gathering. Upon arrival at the gathering you (supplicant) will meet the doorman (authenticator). You will provide your name (credentials) to the doorman (authenticator). He will then check his list (auth server / database), and if your name is indeed on the list you will be granted access to the gathering. This is a very simple way of explaining the process.The actual process is a bit more involved:
The supplicant and authentication server will have to be configured to use the same EAP type.
First the supplicant will associate to the Ap or authenticator and send an EAPOL Start packet**. The authenticator will respond to the EAPOL with an identity request. The supplicant will then respond with the identity, for instance a username. The authenticator will then forward this onto the authentication server. The authentication server will respond with a challenge for the supplicant. The challenge will be the password for that user account contained in the user database. When the supplicant receives the challenge request it will respond with the password for the user account. The authentication server will then check the credentials against the entry for the account in the database. If all checks out the authentication server will respond with an accept packet and the authenticator will grant access to the supplicant.
Supported EAP types:
- EAP-TLS—The EAP-TLS (Transport Layer Security) uses Public key Infrastructure (PKI) to set up authentication with a RADIUS server or any authentication server.
- EAP-TLV- The EAP-TLV (type-length-value) method allows you to add additional information in an EAP message. Often this method is used to provide more information about a EAP message.
- EAP-TTLS—The EAP-TTLS (Tunneled Transport Layer Security) method uses server-side certificates to set up authentication between clients and servers.
- EAP-SIM—The EAP-SIM (Subscriber Identity Module) uses Global System for Mobile Communication (GSM) Subscriber Identity Module (SIM) for authentication and session key distribution.
- EAP-MD5—The EAP-MD5 method verifies MD5 hash of a user password for authentication.
- EAP-FAST—The EAP-FAST (Flexible Authentication via Secure Tunneling) is an alternative authentication method to PEAP
- EAP-AKA—The EAP-AKA (Authentication and Key Agreement) authentication mechanism is typically used in mobile networks that include Universal Mobile Telecommunication Systems (UMTS) and CDMA 2000
- EAP-GTC—The EAP-GTC (Generic Token Card) type uses clear text method to exchange authentication controls between client and server. Since the authentication mechanism uses the one-time tokens (generated by the card), this method of credential exchange is considered safe.
- PEAP—Protected EAP (PEAP) is an 802.1X authentication method that uses server-side public key certificates to authenticate clients with server. The PEAP authentication creates an encrypted SSL / TLS tunnel between the client and the authentication server. The exchange of information is encrypted and stored in the tunnel ensuring the user credentials are kept secure.
- LEAP—Lightweight Extensible Authentication Protocol (LEAP) uses dynamic WEP keys and mutual authentication between client and RADIUS server.
* There are several different options for .1X authentication servers. For instance, IAS in windows. Now a lot of controllers can house the user data base. This will eliminate the need for a dedicted box for authentication purposes. (It is not recommended to try in large deployment only small deployments.)
** Only EAP traffic is passed prior to authentication.