In this blog post I want to share the WPA IE, RSN IE and details of wireless security as it relates to layer 2 frames. The (IE) stands for Information Element.
These IEs can be found in 802.11 Management frames. More specifically Management subtype frames. In this blog post we will dive head first into wireless security 101, specifically from a frame perspective.
For clarification there are Information Fields and Information Elements.
“Information fields are fixed-length mandatory fields in the body of a management frame”
“Information elements are variable in length and are optional.”
Curiosity of CWAP
WEP
Early in 802.11, the only means of security was WEP. WEP stands for Wired Equivalent Privacy. It had a very short shelf life and was quickly exploited. Aircrack-ng and other tools are used to exploit replayed IVs (Initialization Vectors) whereby exposing the WEP key. WEP was used for encryption and did not have a means of authentication. Vendor specific implementations allowed for DYNAMIC WEP. Whereby 802.1X was used for authentication and WEP was used for encryption. Dynamic WEP was never part of the 802.11 standard. WEP was deployed in OPEN or SHARED authentication, but not to be confused with true user authentication.
WPA
WiFi Alliance introduced a stop gap called WPA. WPA stands for Wireless Protective Access. WPA comes in two flavors. 802.1X (Enterprise) and PSK (Shared Key). 802.1X uses the EAP (Extensible Authentication Protocol). PSK uses a shared key between the access point and client radio. WPA uses TKIP (Temporal Key Integrity Protocol) as a means of encryption. When WPA is used specific WPA security information can be found in the WPA IE.
WPA2 / 802.11i
The official standard 802.11i, also called WPA2, has an almost identical frame work as WPA. WPA2 / 802.11i also comes in two flavors, 802.1X and PSK, like WPA. WPA2 / 802.11i uses CCMP (Counter Mode with Cipher Block Chaining Message Authentication Code) as a means of encryption, TKIP is optional according to the spec.
NOTE: You often see TKIP and AES referenced when securing a WiFi client. Really it should be referenced as TKIP and CCMP, not AES. TKIP and CCMP are encryption protocols. AES and RC4 are ciphers, CCMP/AES and TKIP/RC4. You can see vendors are mixing a cipher with a encryption protocol. If taking an exam an easy way to remember the difference is to remember TKIP and CCMP end in ‘P’ for encryption protocol.
Transitional Network
Assume you have a WPA/TKIP SSID today and you want to move to WPA2/AES. This is an example of a transitional network. You are transitioning from WPA to WPA2.
In the real world, this presents challenges. Not all clients like seeing WPA and WPA2 IEs in the same beacon, or TKIP and CCMP for that matter. In my experience Apple devices don’t like seeing both. In other words, deploying an SSID with ‘mix mode’ can act as a means of transition, however some clients break or act oddly when both security mechanisms are used.
Group Cipher
Did you know that multicast and broadcast traffic in 802.11 is encrypted separately from unicast traffic ? Group Cipher identifies the type of encryption used for the multicast / broadcast traffic. When multiple ciphers are used in an SSID, group cipher will drop to the lowest cipher type. The reason for this you ask ? Assume you have a TKIP only client on a transitional WLAN supporting both TKIP and CCMP. If the group cipher was AES, the TKIP clients would not be able to understand the multicast or broadcast traffic, because it doesn't understand the CCMP cipher. On the other hand, CCMP clients can understand TKIP. Just know that the group cipher encryption will drop to the lowest encryption in a transitional network where TKIP and CCMP are supported.
Pairwise Cipher
Pairwise Cipher identifies the type of encryption used for unicast traffic. What is unique about the Pairwise Cipher is that EACH client negotiates a very unique encryption key between the client and access point. This encryption key is so unique that each time you roam from AP to AP the key is renegotiated. In other words, during each roam you always do a 4 way handshake that creates new encryption keys for the unicast traffic between the client radio and the access point radio. It should also be mentioned you will receive a new group key from the new access point.
Cipher Suites
Each cipher uses a very unique identification which represents a very specific encryption type. Note the WPA IE uses another suite of numbers. Our focus in this blog post is WPA2/802.11 RSN. You will also find the capture utility used will often times fill in the name of the mechanism used.
Cipher Suite
00-0F-AC-01 WEP40
00-0F-AC-05 WEP104
00-0F-AC-04 CCMP
00-0F-AC-02TKIP
AKM
Authentication Key Management is used to identify the authentication supported on an SSID. In other words, is 802.1X or PSK supported.
AKM Suites
Each AKM uses a very unique identification which represents a very specific authentication type. Note the WPA IE uses another suite of numbers. Our focus in this blog post is WPA2/802.11i RSN.
AKM Authentication Key Management
00-0F-AC-01 802.1X (EAP)
00-0F-AC-02 PSK
Based on what you just learned. Study the following IEs.
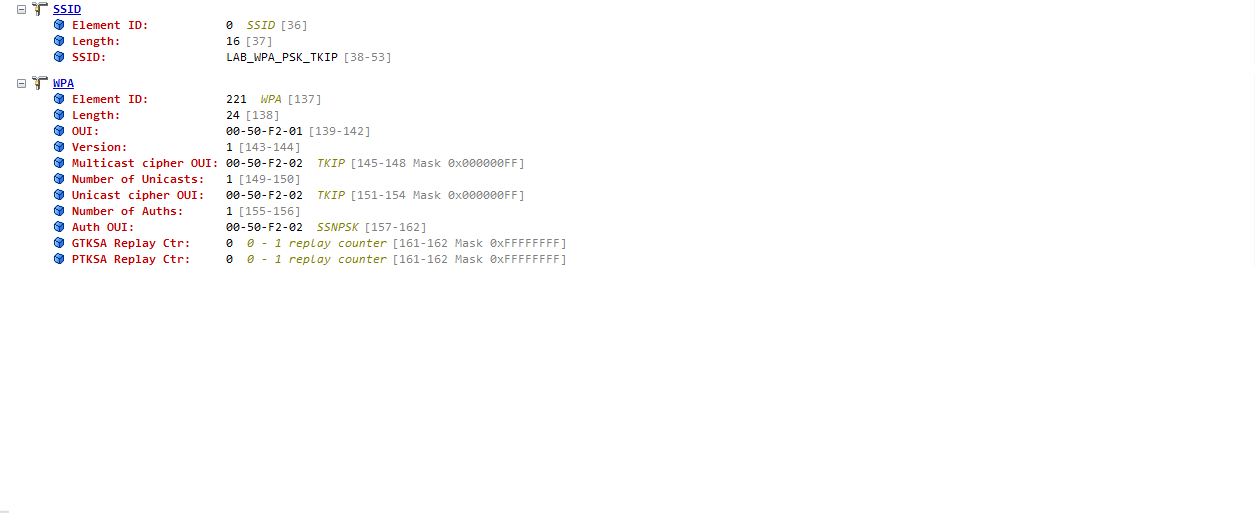
WPA IE - PSK / TKIP
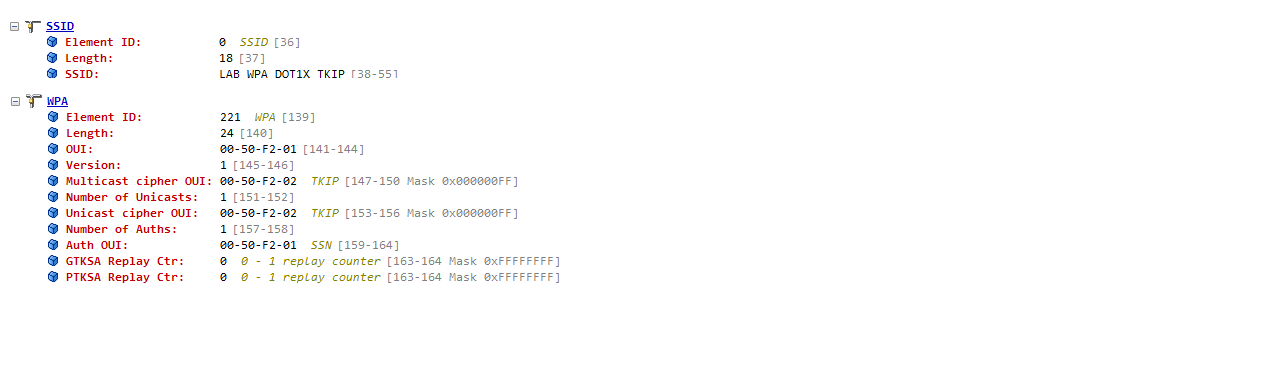
WPA IE - DOT1X / TKIP
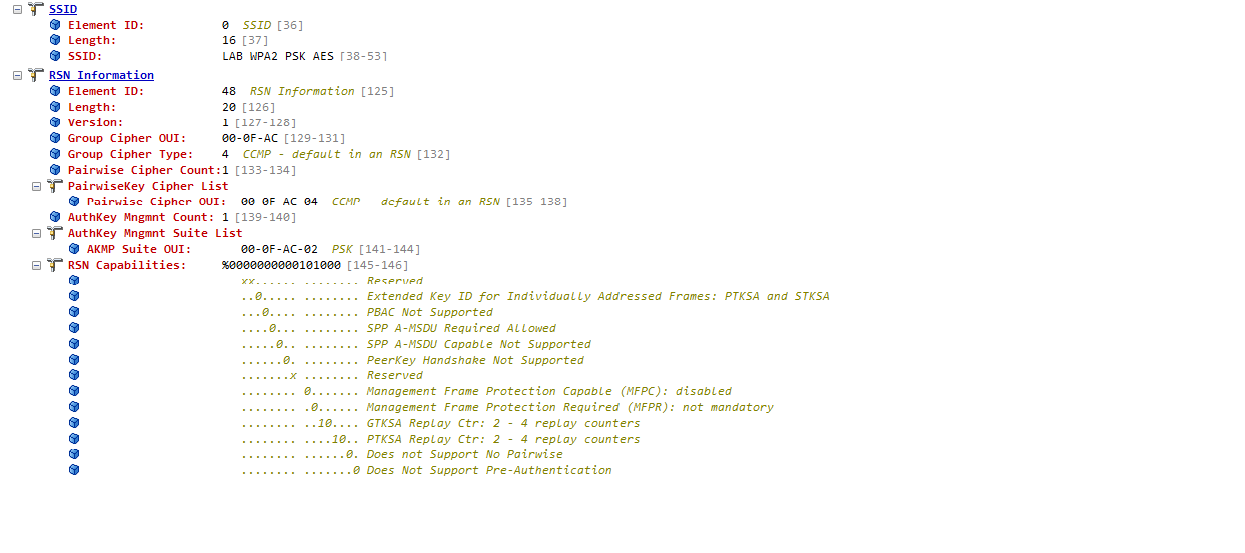
WPA2 RSN IE - PSK / CCMP
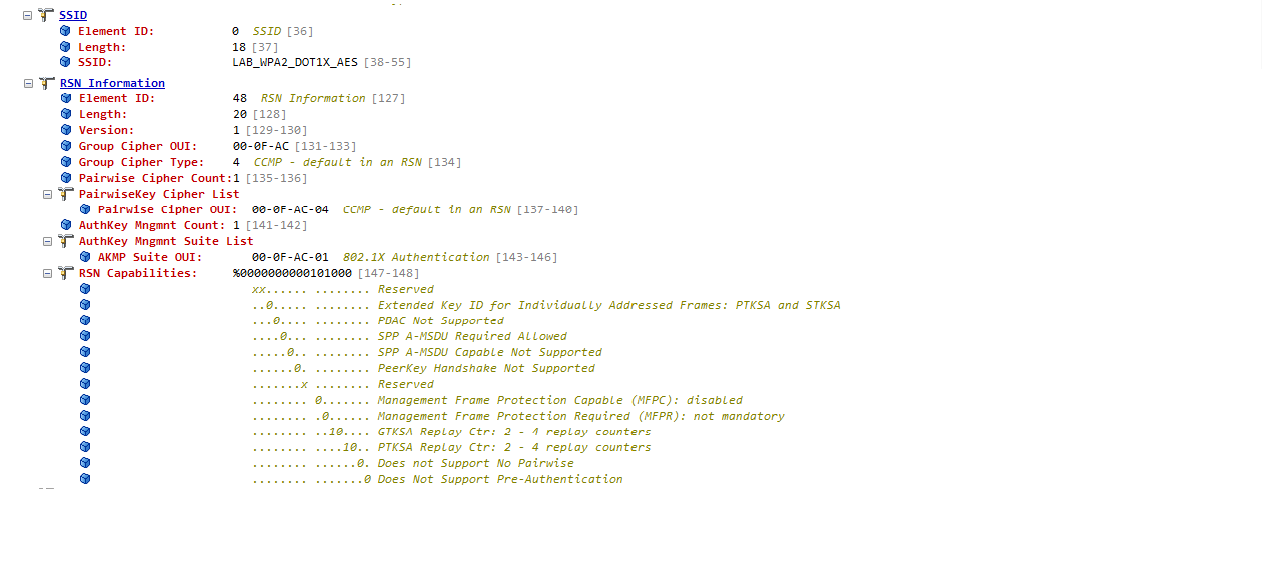
WPA2 RSN IE - DOT1X / CCMP
TRANSITIONAL NETWORK - WPA/WPA2/DOT1X/CCMP/TKIP
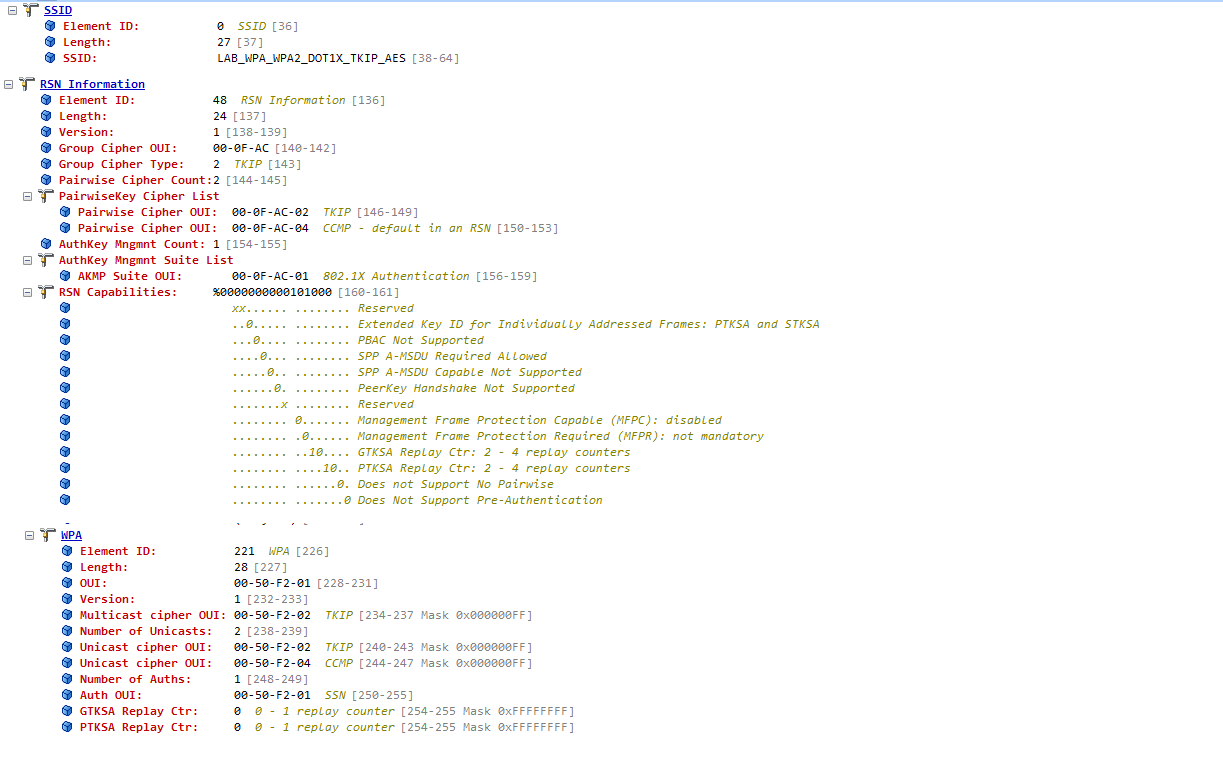
Enjoy!