@Willem Bargemanwrote:
Hi,
The subnet mask is a inverse mask. This is the reason why the ACL is not working. Please try to change the ACL to the following
ip access-list extended "TEST"
10 deny ip 192.168.10.0 0.0.0.255 192.168.2.0 0.0.0.255 log
20 deny ip 192.168.20.0 0.0.0.255 192.168.2.0 0.0.0.255 log
30 deny ip 192.168.32.0 0.0.0.255 192.168.2.0 0.0.0.255 log
40 deny ip 192.168.33.0 0.0.0.255 192.168.2.0 0.0.0.255 log
50 permit ip 0.0.0.0 255.255.255.255 0.0.0.0 255.255.255.255
I would advise to at this ACL as a inbound ACL to each VLAN which you want to block traffic from.
Hi Willem,
Thank you for your reply.
The oddity is back again unfortunately - i've readjusted it to be an inverse subnet mask.
ip access-list extended "TEST"
10 deny ip 192.168.10.0 0.0.0.255 192.168.2.0 0.0.0.255 log
20 permit ip 0.0.0.0 255.255.255.255 0.0.0.0 255.255.255.255Added TEST as an inbound rule on VLAN100
vlan 100
name "SVRS"
untagged 1
ip access-group "TEST" in
ip address 192.168.2.1 255.255.255.0
dhcp-server
But still able to ping through without it hitting the DENY rule.
CORE# sh statistics aclv4 TEST vlan 100 in
Hit Counts for ACL TEST
Total
( 0 ) 10 deny ip 192.168.10.0 0.0.0.255 192.168.2.0 0.0.0.255 log
( 262 ) 20 permit ip 0.0.0.0 255.255.255.255 0.0.0.0 255.255.255.255
Just for kicks - I did a DENY host to my single host (source) 192.168.10.11 to (destination) 192.168.2.51
It still passed through the ACL.
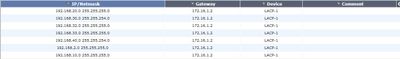
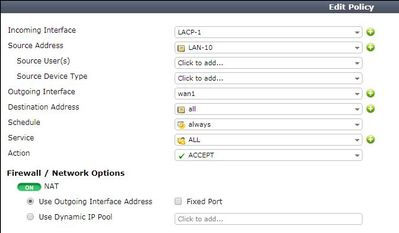
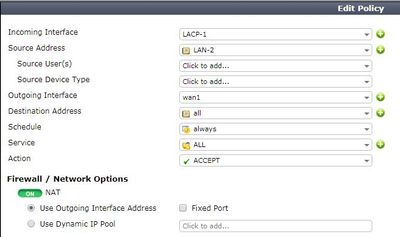
Firewall routing and policies as below: