ArubaOS 8 - Setting up Remote Access Point (RAP)
The post shows the step by step configuration in setting up a Remote AP (RAP) in ArubaOS-8 (AOS8) on a standalone controller
This would be helpful for anyone new to AOS 8 and RAPs
Information is based on ArubaOS Version 8.3.0.0
Remote Access Points AOS6 versus AOS8
In AOS6: | In AOS8: |
Redundancy achieved by, terminating RAPs on VRRP-IP or LMS/BKP-LMS. | High level of redundancy achieved by, terminating RAPs on Cluster |
On Controller failure, RAPs Bootstraps and clients are de-authenticated. | Using L2 Connected Cluster, we can achieve Hitless AP failover and Hitless client failover. We can also do RAP and Client load balancing. |
Points to Consider.
Cluster is limited to max 4 nodes in case of RAP.
If you have a cluster of 4 Mobility Controllers, We should configure public-ip in all 4 controllers. It might be changing in the upcoming release
RAP will establish ipsec tunnels to all 4 controllers, but at any point of time only one A-AAC and on S-AAC will be established.
How to configure a Aruba Controller to terminate RAPs:
ArubaOS Version: 8.3.0.0
Controller Model: 7005
Controller Mode: Standalone
AP Model: AP-303H
Network Diagram: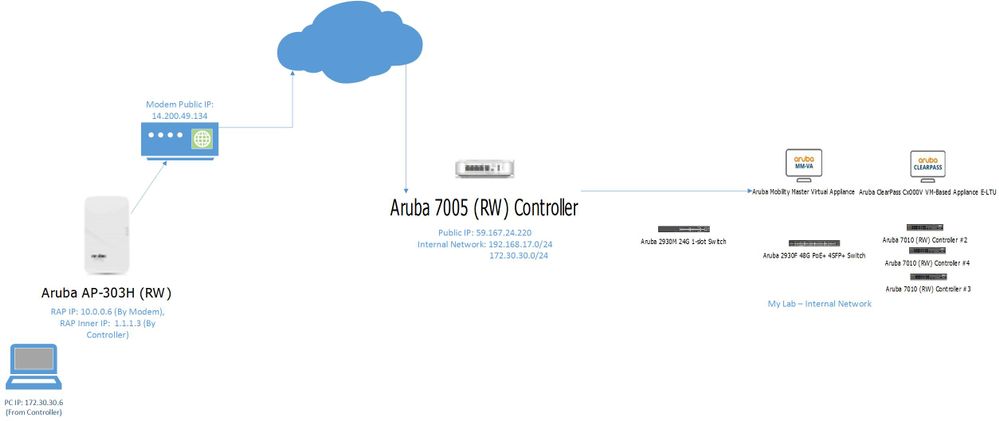
Bring up the Controller in Standalone mode:
Install the Licence:
RAPs do not require PEFV. Only the regular AP licenses (AP, PEFNG).
Mobility Controller -> Configuration -> System -> Licensing
Once Installed, Please ensure that "Feature Enabled" checkbox is ticked. This will enable the license.
Make the Physical Connections:
Aruba 7005 Controller - 0/0/0 - Connected to Internet (Public Network)
Aruba 7005 Controller - 0/0/1 - Connected to My Lab (Internal Network)
Create an L2 and L3 Interface:
L2 and L3 Interfaces - Configuration snippet:
Creating a user role for the RAP user:
//listing all the internal network, I should have access to.
netdestination internal-networks
network 192.168.17.0 255.255.255.0
network 192.168.26.0 255.255.255.0
network 172.30.30.0 255.255.255.0
network 172.30.29.0 255.255.255.0
!
//Tunnelling internal network traffic to Controller and other traffic are source natted.
ip access-list session split-tunnel
any any svc-dhcp permit
user alias internal-networks any permit
alias internal-networks user any permit
user any any route src-nat
!
user-role System-Engineer
access-list session global-sacl
access-list session apprf-system-engineer-sacl
access-list session split-tunnel
!
Configure VPN Pool:
Configuration -> Services -> VPN -> General VPN -> Add the Address Pools
Equivalent CLI Command:
ip local pool "rap" 1.1.1.1 1.1.1.100
If you have an MM and MD setup, to support Remote AP in cluster configuration, you need to use Cluster RAP Pool.
In GUI, Goto MM -> MM-Node
Configuration -> Services -> Clusters -> Controller Cluster RAP Pool
In CLI, To Create rap pool on MM/mynode node
lc-rap-pool cluster-rap-pool <StartAddress> <EndAddress>
Define RAP AP Group and related settings:
ap-group-profile contains virtual-ap-profile and ap-system-profile.
virtual-ap-profile contains aaa-profile and ssid-profile.
//user-role "System-Engineer" is linked to aaa-profile
aaa profile "default"
initial-role "System-Engineer"
authentication-dot1x "default-psk"
!
//Creating the ssid-profile
wlan ssid-profile "Employee-ssid_prof"
essid "KapilHome"
wpa-passphrase "Aruba123!"
opmode wpa2-psk-aes
!
//aaa-profile and ssid-profile is linked to the Virtual AP Profile.
wlan virtual-ap "Employee-rap-vap-profile"
vlan 30
aaa-profile "default"
ssid-profile "Employee-ssid_prof"
!
//Creating the ap-system-profile
ap system-profile "rap-AP-system-profile"
lms-ip 59.167.24.220
ap-console-password "Aruba123!"
bkup-passwords "CP0010727!+^>"
!
//virtual-ap-profile and ap-system-profile is linked to the AP-Group
ap-group "raphome"
virtual-ap "Employee-rap-vap-profile"
ap-system-profile "rap-AP-system-profile"
!
Note:
You can also create WLAN using the wizard under "Configuration -> WLANs".
All the configuration are done on the "default" ap-group.
Name you choose for ssid in WLAN Wizard, is used as name for virtual-ap profile, aaa profile, authentication-dot1x profile and ssid-profile.
Whitelist the Remote AP:
Aruba7005 -> Configuration -> Access Points -> Whitelist -> Remote AP Whitelist.
Equivalent CLI command
whitelist-db rap add mac-address "20:4c:03:21:85:2c" ap-group "raphome" ap-name "Kapil-RAP"
-group "raphome" ap-name "Kapil-RAP"
DHCP Server on the Controller:
This is to serve the clients on VLAN 30.
This can be done under "Configuration -> Services -> DHCP -> DHCP Server" in GUI
ip dhcp excluded-address 172.30.30.101 172.30.30.254
ip dhcp pool pool30
default-router 172.30.30.1
dns-server 8.8.8.8
network 172.30.30.0 255.255.255.0
authoritative
!
service dhcp
Provision the AP (Instant AP):
Here we are converting an Instant AP (IAP) into Remote AP (RAP).
I have got a brand new IAP. I need to Provision the Country Code and then convert to RAP.
Just go to Maintenance -> Convert ->
Select “Remote APs managed by a Mobility Controller”
Enter the IP Address of the Mobility Controller
Click “Convert Now”
Verification Commands:
AP database: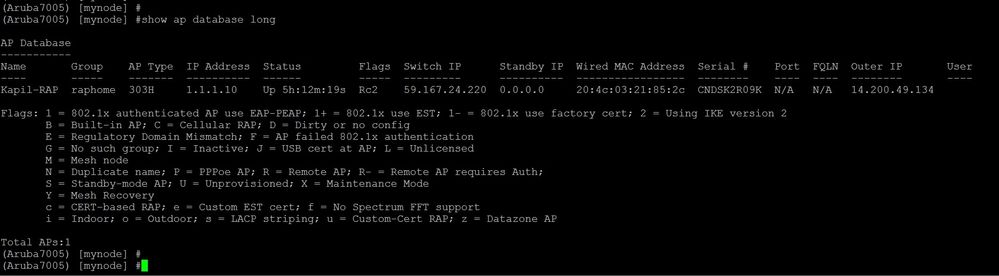
AP bss-table:
Users:
Interfaces on the RAP:
Different ways RAPs can be terminated on the Controller:
Staged: Any CAP APs can be staged to become a RAP
Zero Touch: RAPs have a GUI where the user can enter the IP address or URL of the controller.
Activate: RAPs can also automatically communicate with Aruba cloud based Activate. If an entry exists in Activate it will direct these RAPS to the controller.
Conversion: Instant AP can also be converted to RAPs by pointing to IP address of the Mobility Controller
Hope you find this useful. Please post your feedback !
Regards,
Kapildev Erampu