We recently came across this issue when we decided to offer eduroam as our primary secure network. Eduroam works by using the fully qualified username to route authentication requests to the correct home institution. We wanted to maintain machine authentication so users could do an initial login with AD credentials and also for group policy and updates.
An example of a normal eduroam user authentication would be: cappalli@brandeis.edu.
An example of a machine authentication would be: host/cappalli-xps13.brandeis.edu.
There are two issues with machine authentication with eduroam. The first being that the machine username is not formatted correctly for eduroam. The second issue is that when the computer switches to user authentication after logon, Windows sends credentials in the REALM\username format (USERS\cappalli). This is not valid for eduroam.
The fix below solves two things:
1) It allows you to maintain machine authentication locally on campus. When users are visiting another university, machine authentication will fail and user authentication will be attempted (and should pass).
2) After logging in for the first time, prompt the user to enter valid eduroam credentials (username@domain.edu). These credentials will then be saved with the profile and only need to be entered again if their password changes.
CLEARPASS SERVICE CONFIGURATION
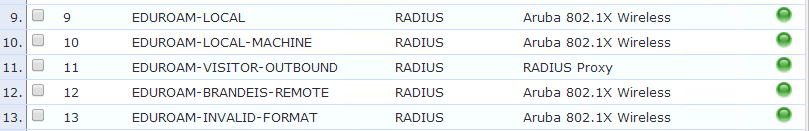
- Duplicate your existing eduroam local user service. Place the new service below your local authentication and above your visitor services.
- Add two new service rules that check for host/ and .domain.edu
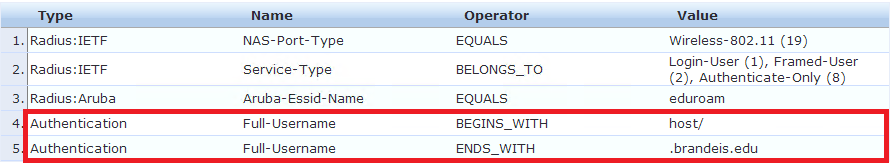
- Configure any role mapping policies if needed.
- Create an enforcement profile that checks for TIPS Role [Machine Authenticated] and map the appropriate enforcement profiles. In this case, we have a machine authentication role that is restricted to talking to domain controllers, DNS, DHCP and WSUS.
WINDOWS CLIENT CONFIGURATION
The client can be configured 3 different ways:
- Group policy profile
- QuickConnect
- Manually
GROUP POLICY
1) In your group policy object, navigate to:
Computer Configuration > Policies > Windows Settings > Security Settings > Wireless Network (IEEE 802.11) Policies
2) Right click and select Create a new wireless network policy.
3) Assign the policy a name such as "Brandeis eduroam"
4) Click the Add button and select Infrastructure
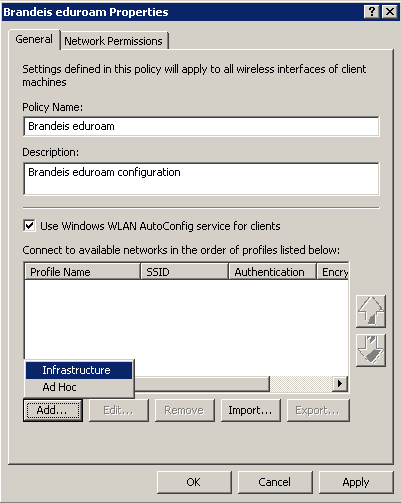
5) Assign the name eduroam to the profile and add eduroam to the SSID list. You might want to also uncheck "Connect to a more preferred network if available"
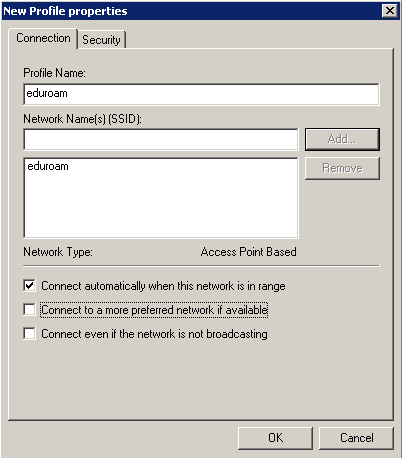
6) Next head over to the Security tab. This should look identical to the client-side supplicant configuration in Windows.
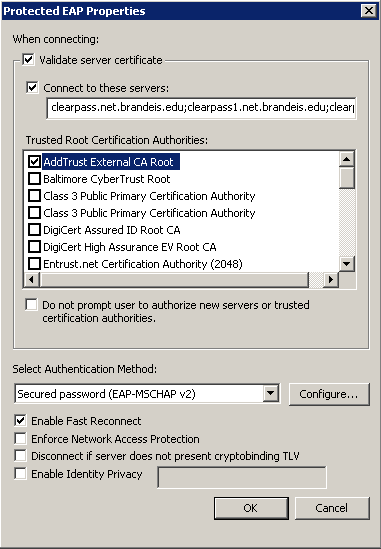
7) First, make sure the Authentication Mode is set to User or Computer authentication. Then click the Properties button next to the network authentication method drop-down.
8) Select the Certificate Authority that signed your RADIUS server certificates and add in your server names to the "Connect to these servers" box. (Use AddTrust if you use InCommon). Next click Configure next to "Select Authentication Method".
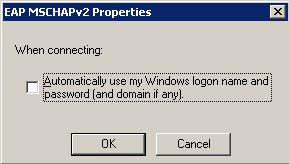
9) Uncheck "Automatically use my Windows logon name and password (and domain if any)". This will force Windows to prompt the user for credentials after the first logon.
10) Link your GPO to the appropriate OU's or security groups.
QUICK CONNECT
Use the settings starting from step 7 to create your profile in the QuickConnect wizard (quickconnect.arubanetworks.com)
MANUAL
Use the same settings starting from step 7 of the group policy config to manually configure a client.