Ayman,
I have tried that in the past, but using the default allow any/any rule. This morning in the default role (RSU1-Auth) I removed the allow any/any and added the below entries:
When I run show datapath acl 140 for the default role (RSU1-Auth) I see that in theory I should have access to the comodo, sectigo and usertrust sites, but I do not see any hits on these sites.
and when the captive portal pops up it is untrusted.
If I disable MAC authentication and use the pre-authentication role (Unregistered) it works:
When I run show datapath acl 109 for the Pre-authentication role I see hits on sectigo
and I get no security errors on the captive portal:
If I leave both MAC authentication and the pre-authentication role enabled, the device stays in the default role and is never placed in the pre-authentication role. Even though there are additional rules after the enforce captive portal rule, they don't seem to take effect when MAC authentication is enabled.
What I'd like to know is if this is even possible to have both of these features active at the same time. I've found no documentation saying that it can't be done, and vague information on a forum saying that you can use both.
------------------------------
Scott Bodeen
Network Admin
Regional School Unit 1
------------------------------
Original Message:
Sent: Oct 13, 2021 07:54 AM
From: Ayman Mukaddam
Subject: External Captive Portal with both MAC Authentication and Pre-Authentication
Hi,
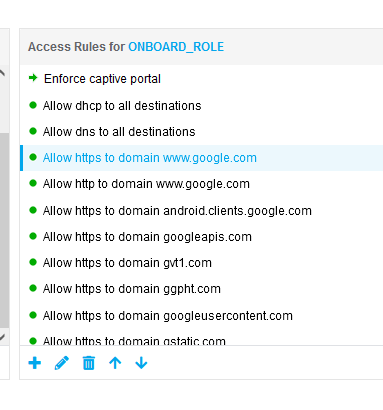
I think your issue is that you are looking at the policy and you are assuming that the enforce captive portal will happen first as it is listed as the first entry (something like the below) ... However, if you add rules to enable http / https to particular destinations that you need in your role, they will be whitelisted. For example, in the below role, users will be able to access www.google.com even though you have enforce captive portal showing as first entry.
------------------------------
Ayman Mukaddam
Original Message:
Sent: Oct 13, 2021 06:19 AM
From: Scott Bodeen
Subject: External Captive Portal with both MAC Authentication and Pre-Authentication
Ayman,
I have tried using RADIUS to respond with the Pre-authentication role and that works as far as putting the device into the Pre-authentication role on the IAP. The problem with that is, that the default role on the IAP is where the external captive portal is enforced. If I move the enforce captive portal rule to the Pre-authentication role I have the problem of our certificates not being trusted because the client device can't verify them. The enforce captive portal rule is always first and I have not found a way to allow other rules to be applied before the captive portal rule creating a 'walled garden' effect. Using pre-authentication with the default role is the only way I've been able to get a 'walled garden' to work with our external captive portal, but only if MAC authentication is disabled.
------------------------------
Scott Bodeen
Network Admin
Regional School Unit 1
Original Message:
Sent: Oct 13, 2021 02:44 AM
From: Ayman Mukaddam
Subject: External Captive Portal with both MAC Authentication and Pre-Authentication
Hi,
I am not 100% sure I get the logic behind your setup but
- If you don't have mac auth, the device will connect and will be placed in initial pre-auth role.
- If you have mac auth, the device will connect and depending on your radius server config, you can return any role that you want. It seems in your case, you want to return pre-auth role as well which will have the captive portal. So why don't you do mac authentication and in your radius server policy return the pre-auth role?
- The device will need to authenticate again against captive portal to change its pre-auth role
------------------------------
Ayman Mukaddam
Original Message:
Sent: Oct 12, 2021 10:40 AM
From: Scott Bodeen
Subject: External Captive Portal with both MAC Authentication and Pre-Authentication
Fellow Airheads,
I'm hoping one of you can shed some light on the problem I'm experiencing. What I am trying to do is: in an IAP environment use an external captive portal with both MAC authentication and the pre-authentication role. It seems I can only do one or the other, but not both at the same time. If I have MAC authentication enabled, devices never get the pre-authentication role. If I disable MAC authentication, then devices get the pre-authentication role.
The reason I need both to work is: MAC authentication allows my network access controller (PacketFence) to know where the device is connected and where to send the RADIUS message upon a successful login via the captive portal. The Pre-authentication role allows my 'walled-garden' to work correctly so our SSL certificates can be validated.
After almost a month of searching, this article (about 6 years old) is the closest I can find to what I'm trying to do: Airheads Community| Airheads Community | remove preview |
 | | Airheads Community | | Question - 1. What is pre-auth role in aruba instant? 2. When should we use the pre-auth role? 3. How can we configure | | View this on Airheads Community > |
|
|
What the article isn't clear on is whether MAC authentication and Pre-authentication can be used simultaneously. I'm currently on Aruba Instant v6.5.4.x and I have not tried downgrading the firmware yet to version 6.4.2.3 to see if both will work.
Any help would be greatly appreciated.
------------------------------
Scott Bodeen
Network Admin
Regional School Unit 1
------------------------------