Overview:
The following post will detail how to configure and integrate Aruba ClearPass with a Cisco wireless LAN controller, for role based access. The example will use both a staff and student type account.
Lab Setup:
ClearPass 6.6.10.x
Cisco vWLC 8.0.x
Cisco WLC Configuration:
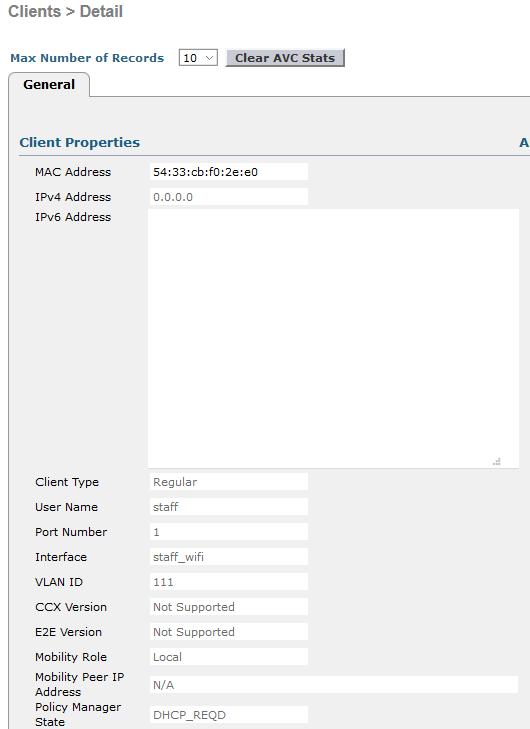
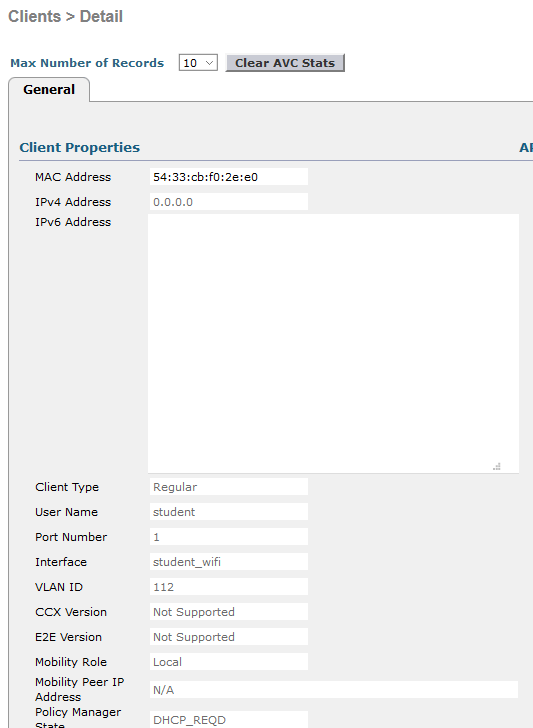
I have created two interfaces on the Cisco WLC, one for students, and one for staff. (note: i have not assigned IP addresses but this would be required for production).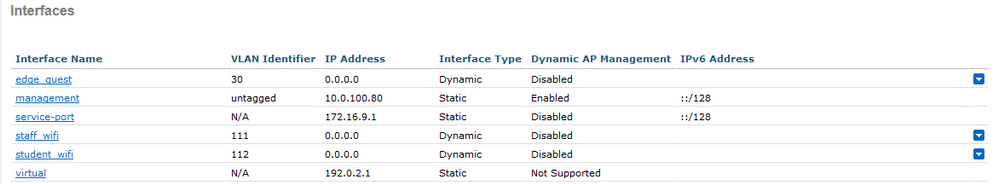
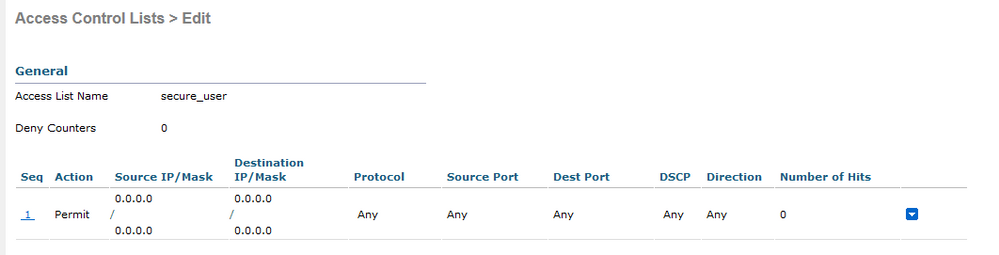
Next i am going to create an access list that will be used by both account types (student and staff). I could use any number of ACL's to restrict traffic based on use case, but for this example i am keeping it simple.
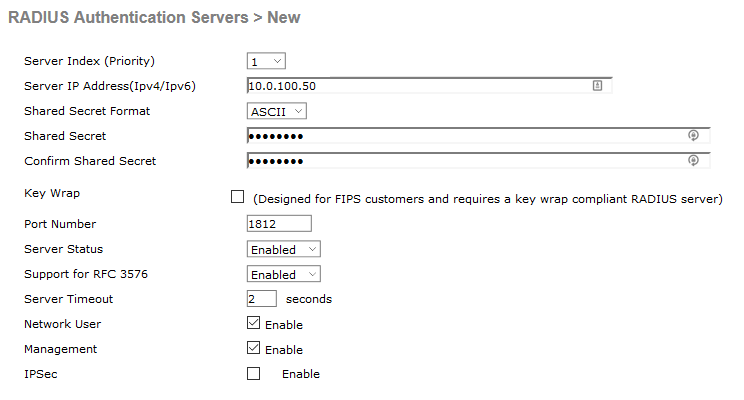
You will need to ensure that "Support for RFC 3576" is enabled, otherwise role based policy from ClearPass won't work.
Finally i am going to configure "Allow AAA Override" on the "Secure" SSID. Without this configuration i wont be able to provide role based access to this SSID.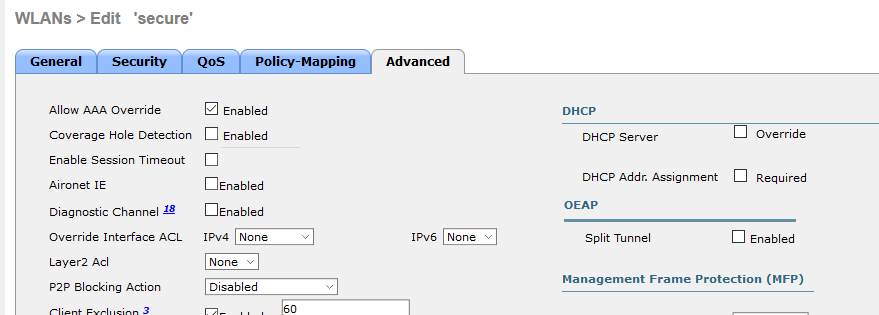
ClearPass Configuration:
First up i am going to add the Cisco WLC as a network device on ClearPass, making sure to set the "Vendor Name" as "Cisco".
To make policy creation a little easier i am going to use device groups to determine what is a Cisco device and what is an Aruba device.
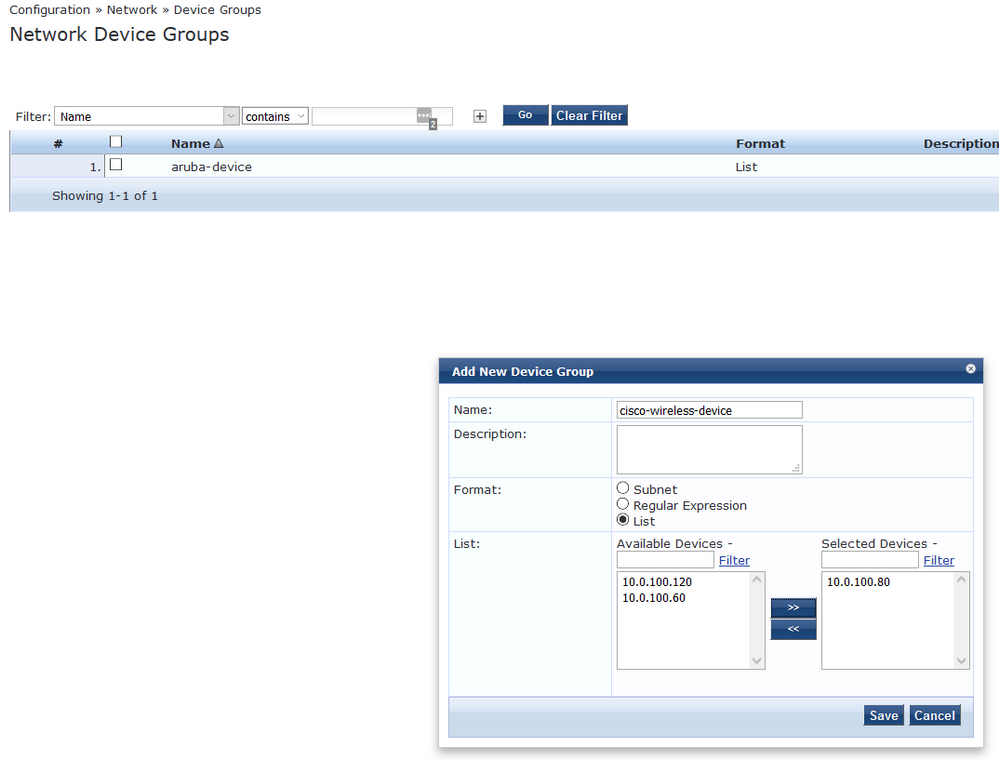
Don't forget to enable the "Airespace" RADIUS attributes on ClearPass, as we will be using these later.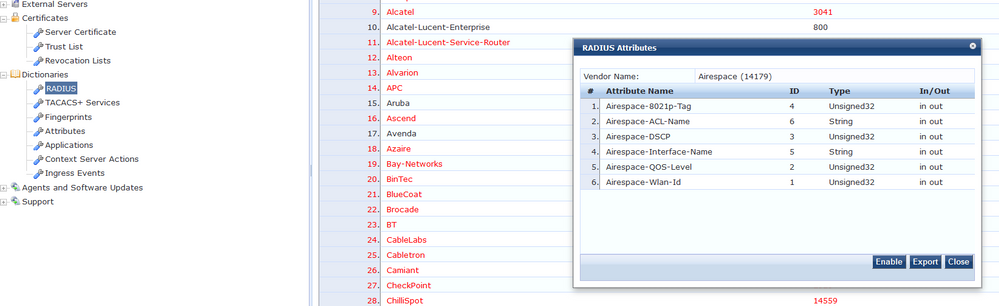
Now i am going to create a couple of roles to be used for applying policy to the Cisco WLC.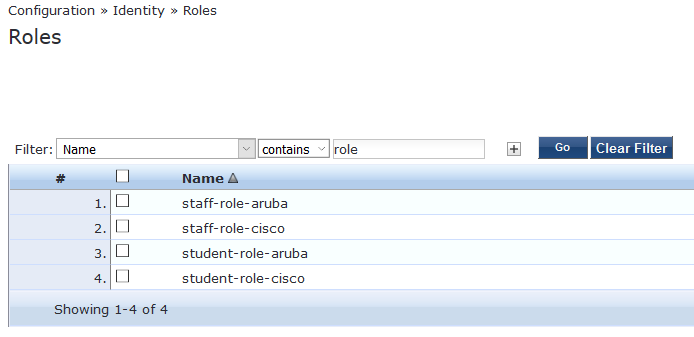
Next up i am going to create a role mapping policy to determine who is a staff user and who is a student user; and from what type of network device they are connecting. (i.e. if the user authenticating is a member of the "StaffGroup" in Active Directory and the network device they are authenticating from is a Cisco device, then i will assign the role "staff-role-cisco".
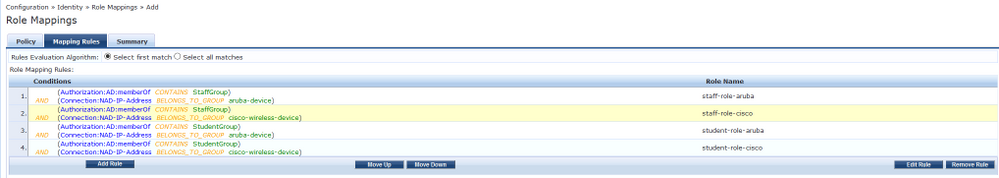
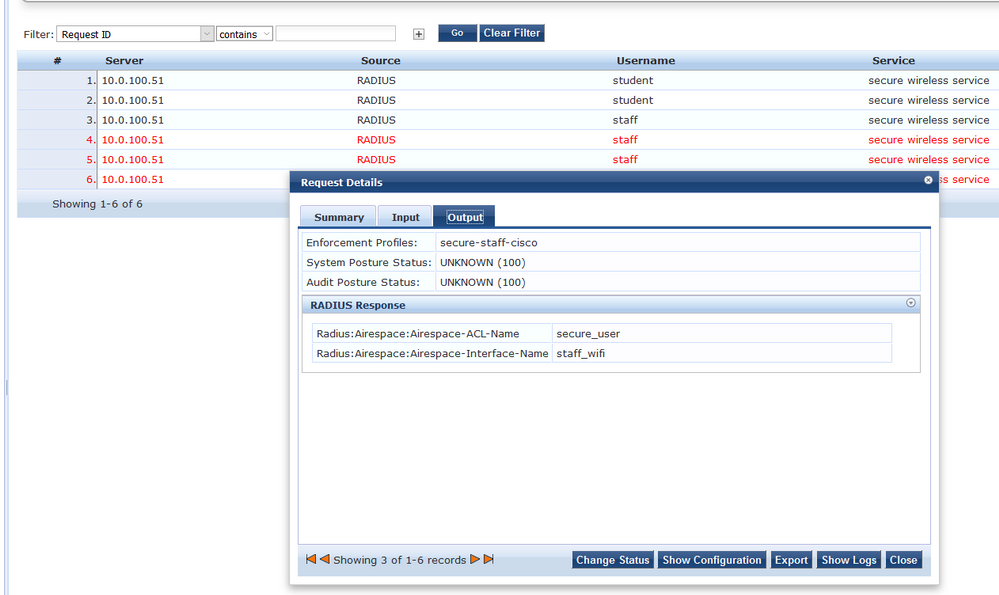
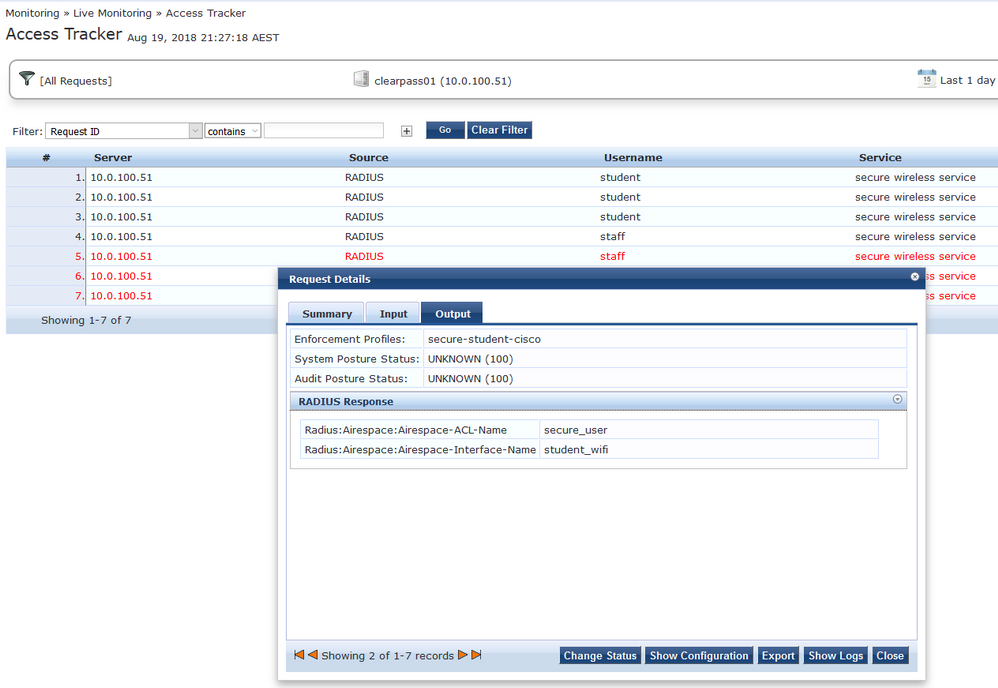
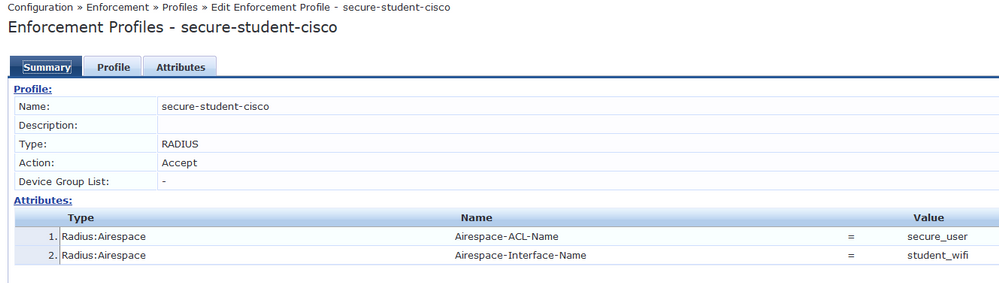
The next step is to create the enforcement profiles that will be sent to the Cisco WLC. These profiles will set the ACL and VLAN that the user will be put on.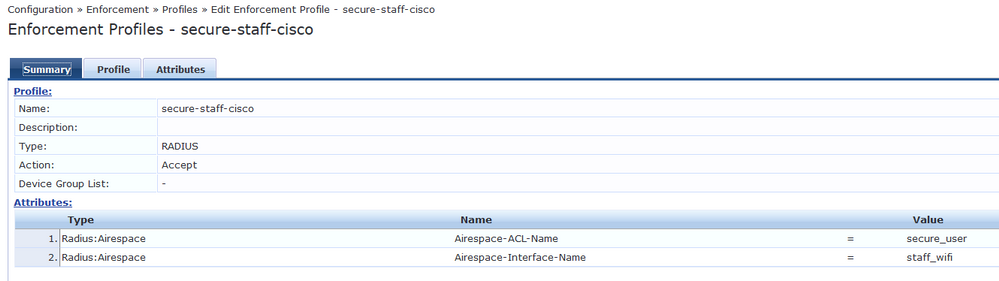
Now that we have created the profiles, it's time to create the policy. The policy will map the roles created earlier to the enforcement profiles.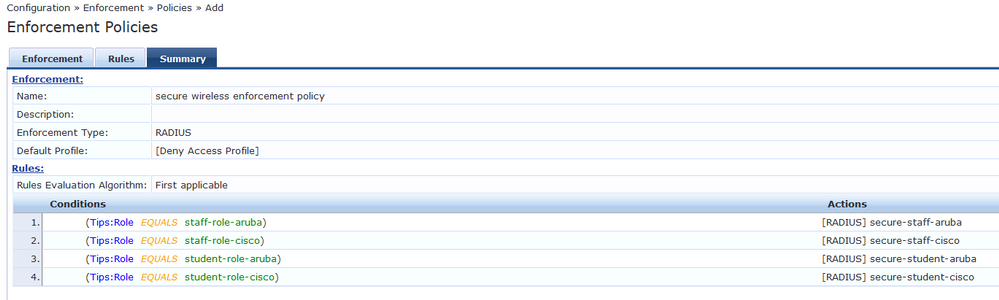
Finally we can create the servive for the secure SSID. This service will match on the "secure" SSID for wireless authentications.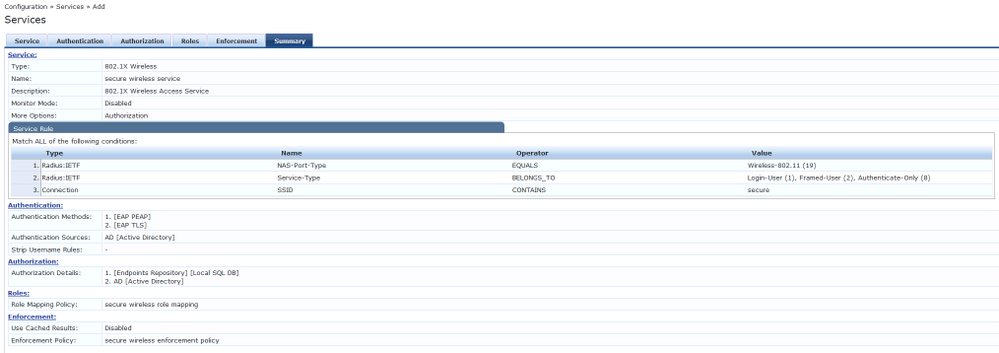
Testing: