Hello cwickline14,
@cwickline14 wrote:
Do you have a TACACS service configured in Clearpass? If you add the NAD, and it properly sends a request, you should see something in a access tracker
I've just tested but only when I use PAP in stead of CHAP you see someting in the access tracker. With CHAP I almost never get someting in the access tracker.
Can you run a show tacacs-server detail?
also run a show aaa authentication?
8320# show aaa authentication
AAA Authentication:
Fail-through : Enabled
Limit Login Attempts : Not set
Lockout Time : 300
Minimum Password Length : Not set
Default Authentication for All Channels:
----------------------------------------------------------------------------------------------------------------------------------
GROUP NAME | GROUP PRIORITY
----------------------------------------------------------------------------------------------------------------------------------
clearpass | 0
----------------------------------------------------------------------------------------------------------------------------------
8320# show tacacs-server detail
******* Global TACACS+ Configuration *******
Shared-Secret: AQBapeZNldLuxrMvpYdzUXZrR4sZ95R9PjZRHNpSp8QcCG/oDAAAAPdrx0iq4S50CpjxWw==
Timeout: 5
Auth-Type: chap
Number of Servers: 1
****** TACACS+ Server Information ******
Server-Name : 10.13.111.19
Auth-Port : 49
VRF : default
Shared-Secret (default) : AQBapeZNldLuxrMvpYdzUXZrR4sZ95R9PjZRHNpSp8QcCG/oDAAAAPdrx0iq4S50CpjxWw==
Timeout (default) : 5
Auth-Type : pap
Server-Group : clearpass
Group-Priority : 1
Also, why do you have failthrough enabled? You only have one server in the server group, so it shouldn't be neccessary (unless my understanding of failthrough is wrong, and different then the WLCs)
If the clearpass servers aren't reachable I would like to have the ability to login to the switch with the local admin account. That's why I enabled failthrough.
Now I've enabled PAP it's sort of working
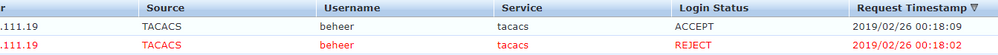
But I get two access requests. The first one fails with
Tacacs server Invalid Sequence number
Second one works.