If you want to do MAC authentication on an AP that carries tagged VLANs, you will need to return the following attributes to switch to port-mode (don't authenticate the clients that reach the switch in the VLANs from the AP:
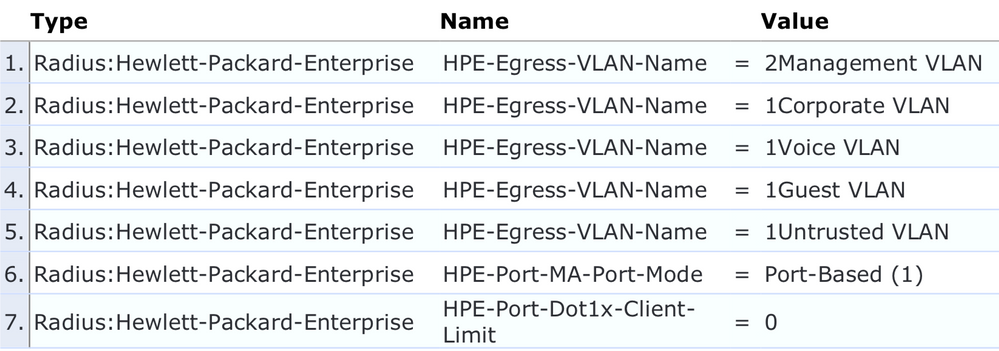
This example uses VLAN names, and the number in front of the VLAN name means 2 for untagged or 1 for tagged. So the VLAN 'Management VLAN' is applied untagged, where 'Corporate VLAN', 'Voice VLAN', etc are applied tagged.
You will need to run on your switch 16.02.0012 or newer for these attributes to be recognized.
In case you authenticate your AP with 802.1X instead of MAC Authentication, the attributes are slightly different:
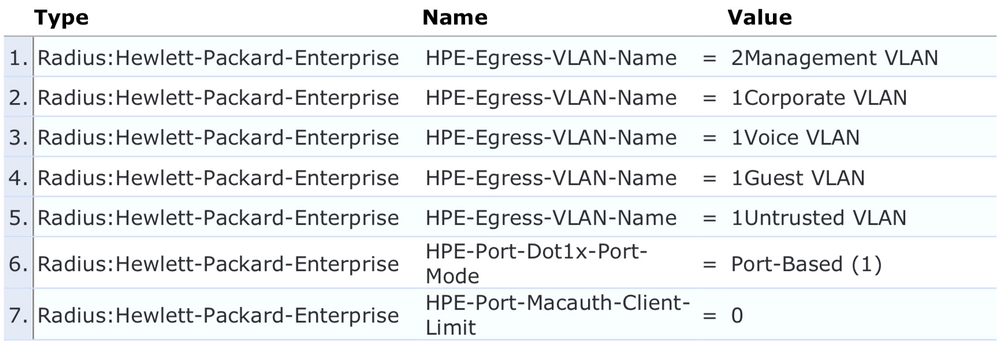 Note that both line 6 and 7 are different for MAC Auth vs 802.1X, but in the end, they do similar things: Authenticate the AP (or other devices), Return native and tagged VLANs, and change to port mode to prevent clients behind the AP from being authenticated on the switch.
Note that both line 6 and 7 are different for MAC Auth vs 802.1X, but in the end, they do similar things: Authenticate the AP (or other devices), Return native and tagged VLANs, and change to port mode to prevent clients behind the AP from being authenticated on the switch.
I can't find the version where the HPE-Port-Dot1x-Port-Mode attribute was introduced, but if you run 16.06 or newer it should be present. If the attributes are not accepted, check the documentation for the version of firmware that you run to see if it is supported, or just upgrade to the latest version.