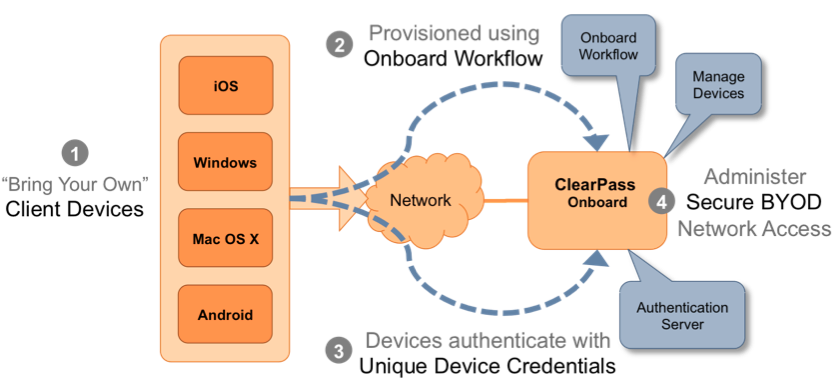
Summary
This solution configures an 802.1X SSID on a Cisco Wireless LAN Controller (WLC) designed for integration with ClearPass Onboard under the Single SSID model. With this single SSID model, the clients first join the SSID by specifying their username and password, which is usually their corporate username/password stored on an Active Directory. If the client's initial username/password authentication is successful, that client will get a captive portal to provision their device using ClearPass Onboard. After the provisioning process, the device can then automatically reconnect back to the same SSID and get elevated access privileges by authenticating with their newly provisioned Onboard credentials. The credentials can be in the form of a unique username/password for EAP-PEAP authentication or can be a client certificate for EAP-TLS authentication. Therefore, one benefit of ClearPass Onboard is that each device has unique device credentials that can be revoked at any time (if a device is lost, employment terminated, etc.). For more details on ClearPass Onboard including configuration help, see the ClearPass Guest Deployment Guide [1] and the ClearPass Policy Manager User Guide [2].
The 802.1X SSID that this solution creates has many small configuration options hard coded that are not normally configured in a generic 802.1X SSID. Each hard coded configuration option helps prevents common issues with Onboard integration. Read over both the configuration notes and the inline comments to understand what gets configured and why.
Onboard Network Architecture
Platform Tested
Cisco WLC 2500 running 7.5.102.0 and ClearPass Policy Manager running 6.2.2.56621. This solution documents configuration for ClearPass 6.2 which should be applicable to ClearPass 6.0 and 6.1. Although the 802.1X SSID can be used for Onboard in CPG 3.9, the notes in this solution may not directly apply.
There have been reports that Cisco 7.3.x version and below didn't work properly with the automatic reconnect feature in Onboard due to a bug in Cisco CoA support. 7.4.x and above have been reported to be working.
The configuration generated will not support Cisco's newest WLC operating system, IOS XE. The configuration is designed based on CLI in the Airespace operating system.
List of client test devices successfully provisioned using the controller configuration generated by this solution:
- Windows 7 64-bit
- iPad 2 w/ 6.1.3
- Samsung Galaxy Tab (GT-P7510) w/ Android 4.0.4
Apple iOS devices running 7.x software will not currently function due to the new way iOS devices check for internet connectivity (CNA). The CNA bypass feature Cisco offers does not currently function properly for iOS 7. There is no current workaround offered by Cisco besides opening multiple Akami /16 addresses. Cisco documents the issue at https://supportforums.cisco.com/docs/DOC-36523 and code fixes will follow.
Configuration Notes
ClearPass Guest and ClearPass Policy Manager will need to be configured before Onboard provisioning will work. See ClearPass Guest Deployment Guide [1] and ClearPass Policy Manager User Guide [2] for more details. The Instructions to Apply section in this solution will go over some of the very basics that need to be configured.
Cisco WLC uses numeric indexes for profile instances. This makes it difficult to provide a set of configurations to apply without first knowing what profile indexes are already in use. To work around this problem, this solution will ask for various profile indexes to use. Commands are given to confirm which indexes are in use for various profiles.
Android devices will need to download the QuickConnect app from the Google Play store as part of the Onboard provisioning process. The play store uses a combination of ports 80 (HTTP) and 443 (HTTPS) to download and display content. In order for the clients to access the Play store over both ports, an ACL was created which allows HTTP/HTTPS access to Google's entire address range. Cisco WLC does not offer hostname based ACL rules such as Aruba so it is not possible to restrict access to only Google Play's hostnames, "android.clients.google.com" and "ggpht.com". The effect of allowing Google's entire address range is that users in the pre-onboard ACL will not redirect to the captive portal page if they request any Google-owned web addresses such as google.com and gmail.com. These requests will go straight through the firewall as allowed.
Similarly, iOS devices need access to apple.com during its network connectivity test. If this test fails, the Captive Network Assistant (CNA) will pop up on the iOS device immediately after connecting to the SSID. The CNA is not a full browser which makes Onboard provisioning inoperable. This CNA must be bypassed and to do so, this solution leverages Cisco's ability to bypass the CNA check. More information is available at http://www.cisco.com/en/US/docs/wireless/controller/7.4/configuration/guides/wlan/config_wlan_chapter_010001.html. After applying the configuration, the controller must be reset before the setting will take effect. Issue a "save config" followed by "reset system" after applying the configuration to enable the CNA bypass feature. iOS devices running 7.x are not supported by Cisco's CNA bypass feature as stated earlier.
The solution relies on the proper configuration of ClearPass Policy Manager and ClearPass Guest. The WLC does not define the captive portal redirect directly. Instead, it uses the WLC conditional redirect feature and relies on ClearPass to return a RADIUS attribute "url-redirect". More details on the ClearPass configuration is documented in the Instructions to Apply section.
Licensing
No special licenses are required.
References