We have a PSK based SSID. All the client connect fine except a few. They show both the following errors"
1. "mic failures" in auth tracebuf.
2. "Reason Ptk Challenge Failed" in user debug.
What could be the reason behind this.
Environment : This article applies to all Aruba controllers and os versions.
we can create a preshared key based SSID on Aruba controller. This SSID will encrypt all the user traffic to the AP however it doesn't require a back-end authentication server.
Requirements:
1. A dummy dot1x profile is mapped in the aaa profile:
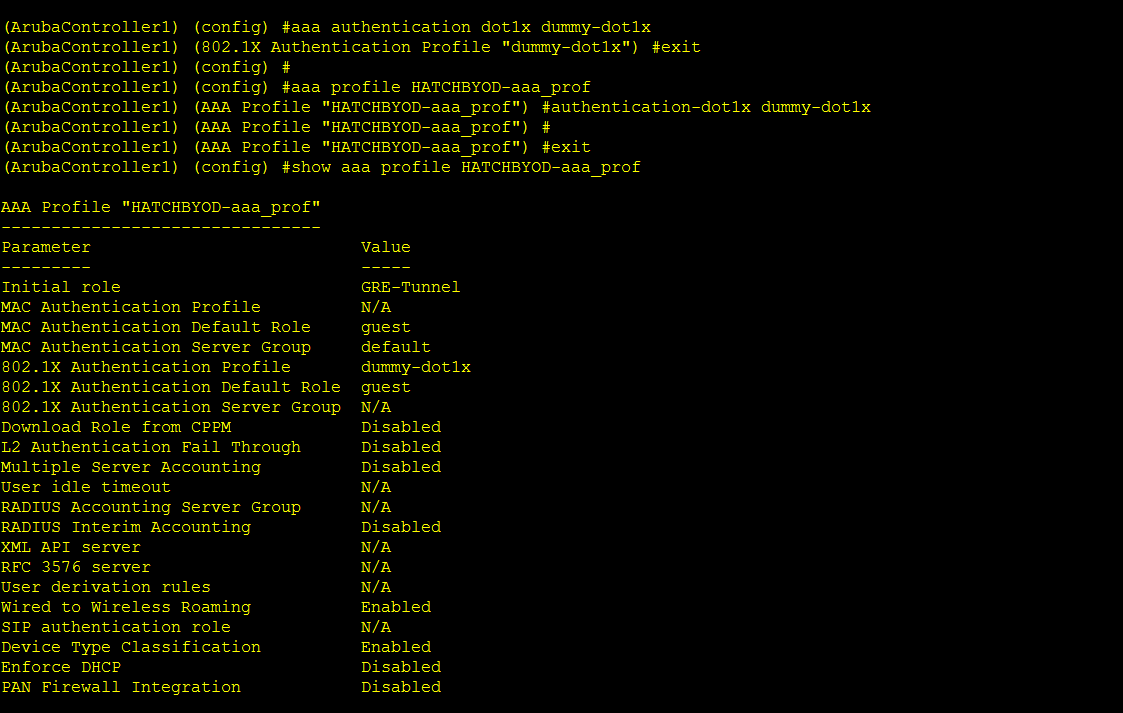
2. Then we need to give passphrase and opmode on the SSID profile:
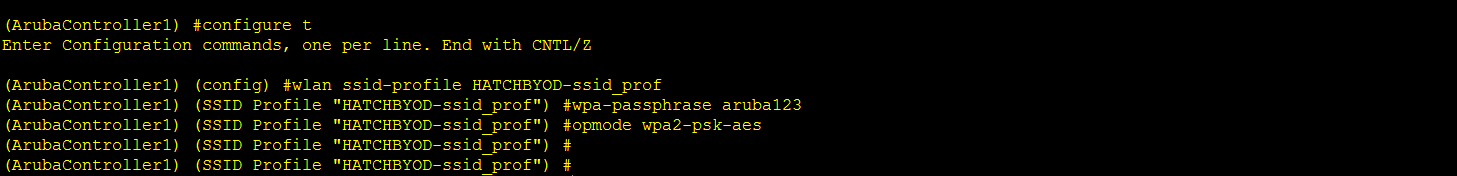
3. After this, we can see that the SSID is now PSK based:
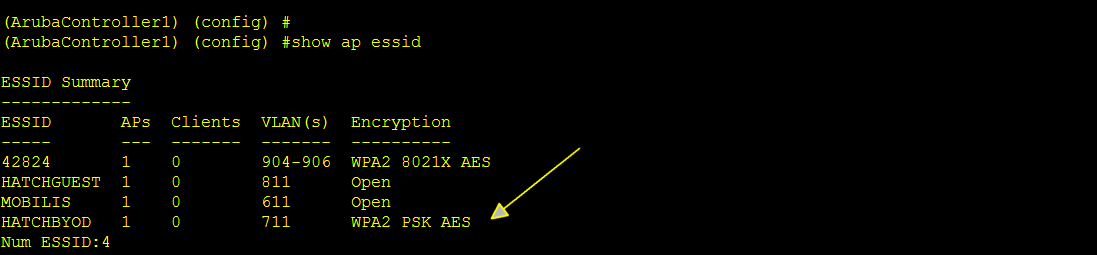
4. The same passphrase must be given in the client machine.
5. When all the parameters are correct, we see the following:
(ArubaController1) (config) #show auth-tracebuf mac a4:4e:31:75:0b:fc count 30
Auth Trace Buffer
-----------------
Jan 5 05:35:18 wpa2-key1 <- a4:4e:31:75:0b:fc 9c:1c:12:b9:76:13 - 117
Jan 5 05:35:18 wpa2-key2 -> a4:4e:31:75:0b:fc 9c:1c:12:b9:76:13 - 119
Jan 5 05:35:18 wpa2-key3 <- a4:4e:31:75:0b:fc 9c:1c:12:b9:76:13 - 151
Jan 5 05:35:18 wpa2-key4 -> a4:4e:31:75:0b:fc 9c:1c:12:b9:76:13 - 95
6. However, if we have a PSK mismatch on the controller and the client machines, we will see the MIC failure on key2 transaction:
(ArubaController1) #show auth-tracebuf mac a4:4e:31:75:0b:fc count 30
Auth Trace Buffer
-----------------
Jan 5 05:38:42 station-down * a4:4e:31:75:0b:fc 9c:1c:12:b9:76:13 - -
Jan 5 05:38:42 station-up * a4:4e:31:75:0b:fc 9c:1c:12:b9:76:13 - - wpa2 psk aes
Jan 5 05:38:42 wpa2-key1 <- a4:4e:31:75:0b:fc 9c:1c:12:b9:76:13 - 117
Jan 5 05:38:43 wpa2-key1 <- a4:4e:31:75:0b:fc 9c:1c:12:b9:76:13 - 117
Jan 5 05:38:43 wpa2-key2 -> a4:4e:31:75:0b:fc 9c:1c:12:b9:76:13 - 119 mic failure
Jan 5 05:38:44 wpa2-key1 <- a4:4e:31:75:0b:fc 9c:1c:12:b9:76:13 - 117
Jan 5 05:38:44 wpa2-key2 -> a4:4e:31:75:0b:fc 9c:1c:12:b9:76:13 - 119 mic failure
Jan 5 05:38:45 wpa2-key1 <- a4:4e:31:75:0b:fc 9c:1c:12:b9:76:13 - 117
Jan 5 05:38:45 wpa2-key2 -> a4:4e:31:75:0b:fc 9c:1c:12:b9:76:13 - 119 mic failure
7. In the user debug we see the following:
show log all | include a4:4e:31:75:0b:fc
Jan 5 05:39:25 stm[1136]: <501000> <DBUG> |AP 9c:1c:12:c3:97:60@192.168.30.3 stm| Station a4:4e:31:75:0b:fc: Clearing state
Jan 5 05:39:25 stm[1136]: <501105> <NOTI> |AP 9c:1c:12:c3:97:60@192.168.30.3 stm| Deauth from sta: a4:4e:31:75:0b:fc: AP 192.168.30.3-9c:1c:12:b9:76:13-9c:1c:12:c3:97:60 Reason Ptk Challenge Failed
Jan 5 05:39:25 stm[2131]: <501000> <DBUG> |stm| Station a4:4e:31:75:0b:fc: Clearing state
Jan 5 05:39:25 stm[2131]: <501080> <NOTI> |stm| Deauth to sta: a4:4e:31:75:0b:fc: Ageout AP 192.168.30.3-9c:1c:12:b9:76:13-9c:1c:12:c3:97:60 Ptk Challenge Failed
Jan 5 05:39:25 stm[2131]: <501106> <NOTI> |stm| Deauth to sta: a4:4e:31:75:0b:fc: Ageout AP 192.168.30.3-9c:1c:12:b9:76:13-9c:1c:12:c3:97:60 wifi_deauth_sta
Jan 5 05:39:34 stm[1136]: <501044> <NOTI> |AP 9c:1c:12:c3:97:60@192.168.30.3 stm| Station a4:4e:31:75:0b:fc: No authentication found trying to de-authenticate to BSSID 9c:1c:12:b9:76:13 on AP 9c:1c:12:c3:97:60
Jan 5 05:39:34 stm[1136]: <501105> <NOTI> |AP 9c:1c:12:c3:97:60@192.168.30.3 stm| Deauth from sta: a4:4e:31:75:0b:fc: AP 192.168.30.3-9c:1c:12:b9:76:13-9c:1c:12:c3:97:60 Reason Denied: AP Ageout
Jan 5 05:39:34 stm[1638]: <501080> <NOTI> |stm| Deauth to sta: a4:4e:31:75:0b:fc: Ageout AP 192.168.30.3-9c:1c:12:b9:76:13-9c:1c:12:c3:97:60 Denied: AP Ageout
8. Most new client supplicants will ask for new PSK if it is mismatched but some client wont. To resolve this, we need to make sure that the preshared-keys are same on both the controller and the client.
ON a PSK SSID, if we see the following for the same client:
1. "mic failures" in auth tracebuf.
2. "Reason Ptk Challenge Failed" in user debug.
It usually means that there is a passphrase mismatch and we need to fix the same.