Introduction
Aruba Instant can accommodate only one built-in management user account. If multiple management user accounts are required, then management authentication must be done against an external server. This configuration guide walks you through the configuration steps on Aruba Instant and the commonly deployed RADIUS server: Microsoft Windows Server 2003 Internet Authentication Service (IAS).
The document contains the following sections:
· Configuring Aruba Instant
o Enabling Dynamic Radius Proxy
o Adding a RADIUS Server
o Configuring Instant to Use a RADIUS Server for Management User Authentication
· Configuring Microsoft IAS Server
o Adding a Virtual Controller as a RADIUS Client
o Creating a New Remote Access Policy
· Verification
· Troubleshooting
· Advanced Troubleshooting
Feature Notes
· All external management users that have successfully authenticated will have root access to the system. The current release does not support configuring users with different management roles.
· The Internal authentication server cannot be used for management authentication.
· The "Fallback to Internal" option comes into effect only if the RADIUS Server is unreachable.
· Only the PAP-based authentication method is supported
· RADIUS Request for Management Authentication would use Calling-Station ID 5A0000000000.
Test Environment
The following software and hardware are used in this document to illustrate the concept and configuration steps.
| Hardware |
Aruba Instant AP 105 |
| Software |
Aruba Instant 6.1.3.1-3.0.0.0_33460 |
| RADIUS Server |
Microsoft Windows Server 2003 Internet Authentication Service (IAS) |
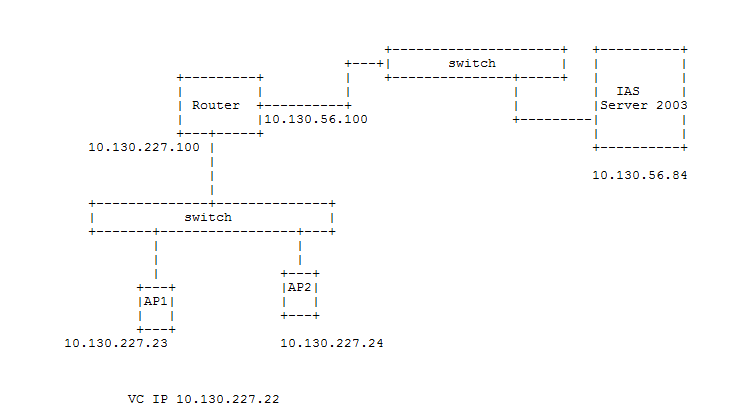
Network Topology
Configuring Aruba Instant
Enabling Dynamic RADIUS Proxy
The Dynamic RADIUS proxy configuration is optional. When this configuration option is enabled, the virtual controller communicates with the RADIUS server using the virtual IP address. You must assign the IP address of the virtual controller to the cluster when the Dynamic RADIUS Proxy option is enabled. On the RADIUS server, only the IP address of the virtual controller needs to be added into the RADIUS client list. Without this option, the IP address for every Aruba Instant AP (IAP) must be added as a RADIUS client.
To enable the Dynamic RADIUS Proxy configuration option:
- Click Settings > General.
- Enter the IP address of the virtual controller.
- Enable the Dynamic RADIUS proxy option.
- Click OK.
Adding a RADIUS Server
To add a RADIUS server:
- Click PEF.
- Click the Authentication Servers tab and click New.
- Make sure that RADIUS is selected.
- Enter the Name, IP address, and shared secret.
- Edit the Auth port and Accounting port, if needed.
- Optionally, configure the virtual controller IP address as the NAS IP address. This option is sent to the RADIUS server as part of the RADIUS Request (Attribute Value Pair Type # 4). If the option is not configured, the virtual controller IP address would be used by default when Dynamic RADIUS Proxy is enabled.
- Optionally, configure a friendly name under NAS identifier. This option is sent to the RADIUS server as part of the RADIUS Request (Attribute Value Pair Type # 32). The name helps in identifying the virtual controller on the RADIUS end.
- Click OK.

Configuring Instant to Use a RADIUS Server for Management User Authentication
To map the server for management authentication:
- Click Settings and click the Admin tab.
- For Authentication, select RADIUS server or RADIUS server w/fallback to Internal.
- Click OK.
When the "RADIUS server w/fallback to Internal" option is selected, the internal username / password can be used if the server is unreachable.

Configuring Microsoft IAS Server
Adding a Virtual Controller as a RADIUS Client
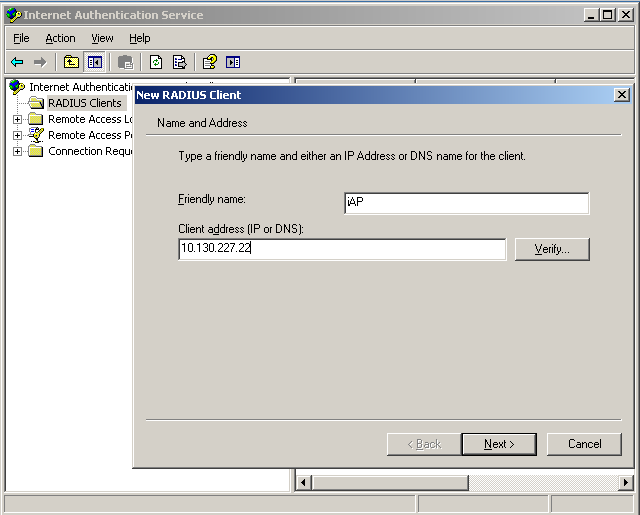
To add a virtual controller as a RADIUS client;
- Click Start > All Programs > Administrative Tools > Internet Authentication Service.
- Right-click RADIUS Clients and select the New RADIUS Client option.
- Provide a friendly name and give the IP address of the virtual controller as the client address. Click Next.
4. Use the same shared secret as was used on the Instant end. Ensure that Client-Vendor is set to RADIUS Standard (the default option).

5. Click Finish.
The virtual controller has been added as a RADIUS client.
Creating a New Remote Access Policy
Unlike wireless clients, management authentication uses NAS Port Type Virtual (VPN) and supports only PAP.
As a best practice, configure management users to be members of a different user group, and then limit access to that user group. In this example, management users are members of the Wireless Admin user group.
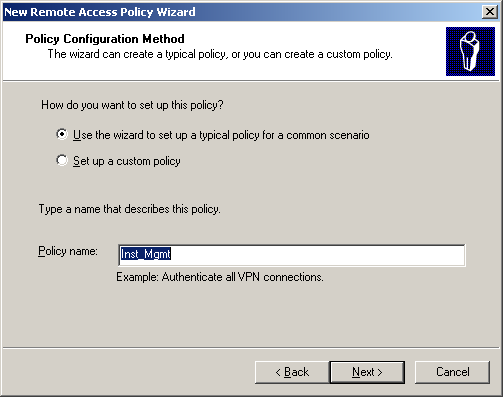
To create a new Remote Access Policy:
- Click Start > All Programs > Administrative Tools > Internet Authentication Service.
- Right-click Remote Access Policy and select New Remote Access Policy.
- Enter the Policy name.
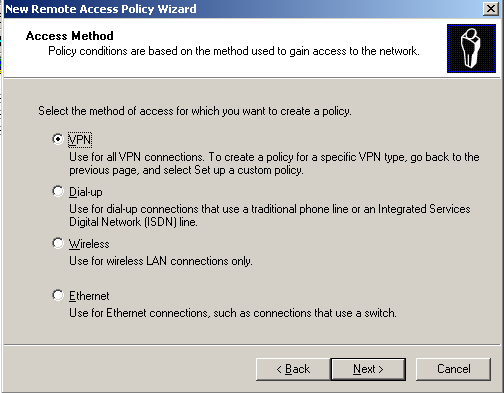
4. Select VPN as the method of access. Click Next.
5. Select the Group option and then click Add.
6. Enter the Active Directory User Group, which the management users are members of, and then click Check Name. If the Group name is valid; it is underlined after Check Name is clicked. Click OK.
7. Now that the Group is added, click Next.
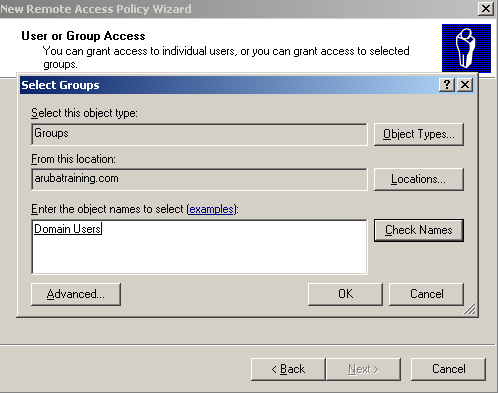
8. On the Authentication tab, the authentication method "Microsoft Encrypted Authentication version 2 (MS-CHAP v2)" is selected by default. However, this method is not supported by Aruba Instant for management user authentication. Click OK.

9. For the Policy Encryption Level, also click Next without editing the options.
10. Click Finish.
11. If other remote access policies are defined, order the policies appropriately to ensure that the server selects this policy for servicing management authentication requests from Aruba Instant. One of the options could be to move it to top.
12. Right-click the policy and select properties and Edit Profile.
13. Click the Authentication tab and ensure that the Unencrypted Authentication (PAP, SPAP) option is checked and the Microsoft Encrypted Authentication version 2 (MS-CHAP v2) option is unchecked.
14. Click OK twice to save the configuration.
At this point, the IAS Server and the Aruba Instant AP are configured to support management user authentication.
Verification
Before testing, confirm that the external management user account in Active Directory is configured correctly.
Open Active Directory, navigate to the management user account, right-click and select Properties.
Ensure the management user belongs to the Group that was specified in the RADIUS policy (that is, Wireless Admin).
Ensure the management user has Dial-in enabled, that is, the Allow access option is selected on the Dial-in tab.

After you have logged in to the Aruba Instant AP, use the external management user account:
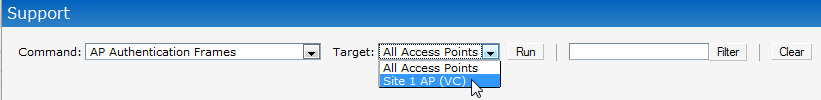
- Navigate to Support. For Command select AP Authentication Frames and for Target, select VC. A successful management authentication should be displayed at the end.
Jan 1 07:56:08 mgmt-auth-request -> 5a:00:00:00:00:00 00:00:00:00:00:00/IAS - - vijay
Jan 1 07:56:08 mgmt-auth-success <- 5a:00:00:00:00:00 00:00:00:00:00:00/IAS - - success
- Select Command show log all. A corresponding entry for the login is displayed.
Jan 1 07:56:10 syslog: User vijay IP 10.130.56.60 login by web UI successfully
- The Windows Server 2003 Event Viewer should show an informational log entry with Source IAS. Ensure the right policy is getting hit.
Sample Event Viewer Entry:
Event Type: Information
Event Source: IAS
Event Category: None
Event ID: 1
Date: 4/30/2012
Time: 10:29:19 PM
User: N/A
Computer: SERVER2003
Description:
User vijay was granted access.
Fully-Qualified-User-Name = arubatraining.com/Users/Vijay TR
NAS-IP-Address = 10.130.227.22
NAS-Identifier = <not present>
Client-Friendly-Name = iAP
Client-IP-Address = 10.130.227.22
Calling-Station-Identifier = 5A0000000000
NAS-Port-Type = Virtual
NAS-Port = 0
Proxy-Policy-Name = Use Windows authentication for all users
Authentication-Provider = Windows
Authentication-Server = <undetermined>
Policy-Name = Inst_Mgmt
Authentication-Type = PAP
EAP-Type = <undetermined>
- Sometimes the RADIUS server is not reachable. If the authentication mode in the Aruba Instant AP is set to "RADIUS server w/fallback to Internal", the following should be seen in the output of Command "AP Authentication Frames". In such a scenario, the "Auth Trace Buffer" shows a server timeout followed by a successful login:
Jan 1 07:27:00 mgmt-auth-request -> 5a:00:00:00:00:00 00:00:00:00:00:00/IAS - - admin
Jan 1 07:27:20 server out-of-service * 5a:00:00:00:00:00 00:00:00:00:00:00/IAS - - server timeout
Jan 1 07:27:21 syslog: User admin IP 10.130.56.60 login by web UI successfully
Troubleshooting
The issues with management user authentication are usually associated with the configuration and the network communication between the Aruba Instant APs and the RADIUS servers.
To identify the authentication status, navigate to Support. For Command, select AP Authentication Frames, and for Target, select VC. Then click Run.
Jan 1 07:27:00 mgmt-auth-request -> 5a:00:00:00