This post is actually a checklist to keep in mind, in order to get the RADIUS Dynamic Authorization in Clustering working.
To understand "How it works”,
Read "Change of Authorization" under "Clustering" in “ArubaOS 8 Fundamentals" guide.
To Configure Clustering and Dynamic Authorization,
Please refer https://ase.arubanetworks.com/
My Setup: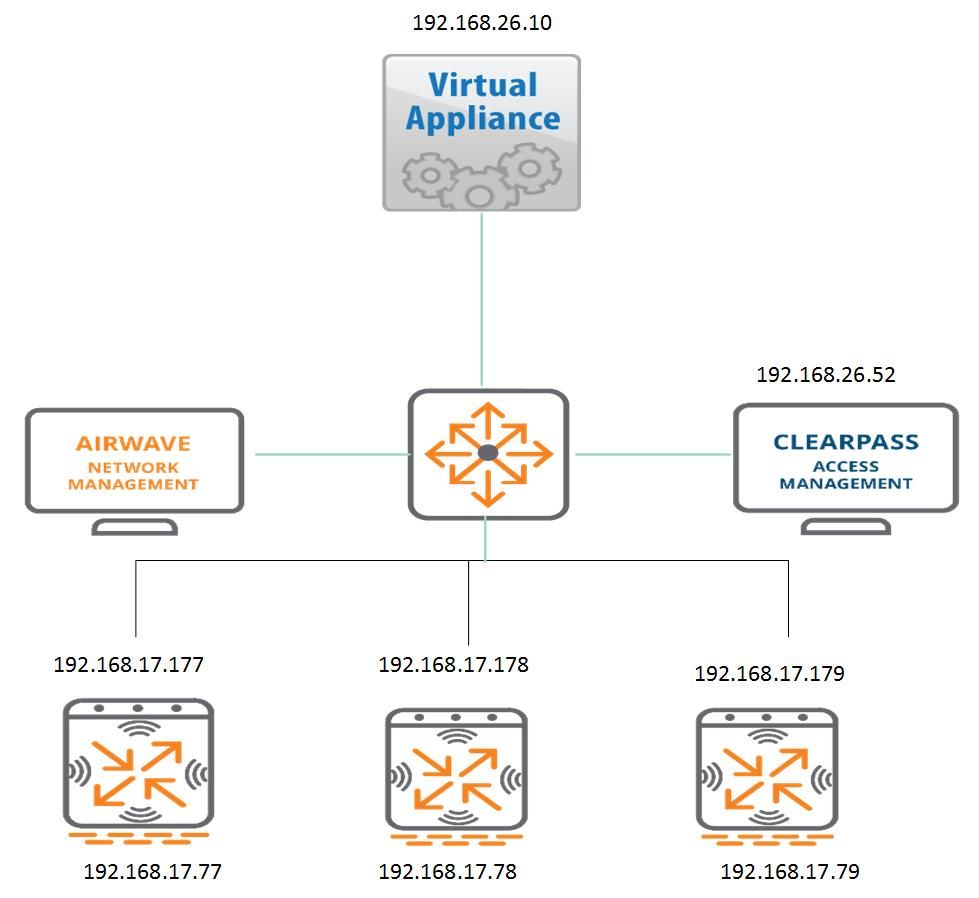
Cluster Dynamic Authorization Support:
The above setup shows a 3-nodes cluster where 3 VRRP instance will be dynamically created with 3 VIPs.
The VRRP IDs will be 220, 221 and 222.
The priorities are dynamically assigned where the master of an instance (MC1) with ID 220 gets 255, the first backup within that instance gets 255-20=235 and the second backup gets 235-20=215
The same is true for the second vrrp instance (MC2) with ID-221 where MC2 gets the highest priority 255 followed by MC1 as backup1 with 235 and MC3 as backup2 with 215.
The third instance follows the same pattern.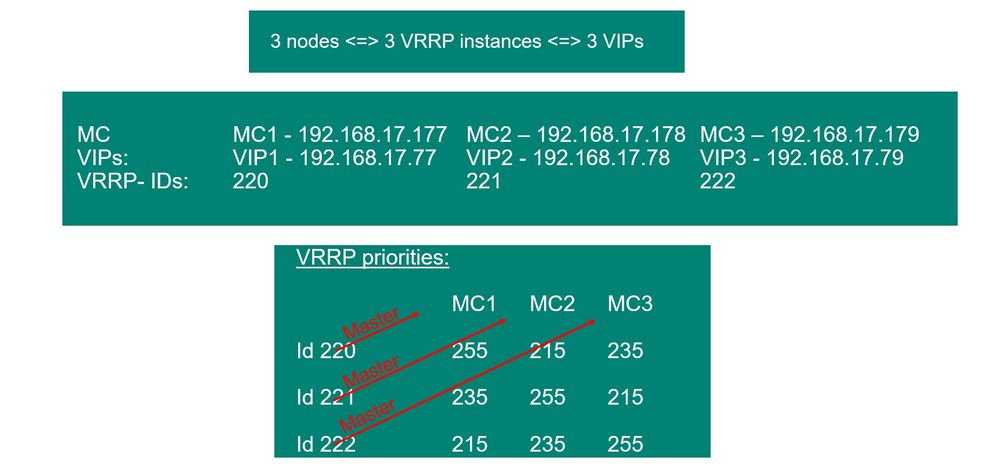
CHECKLIST:
1) Verify that you have linked the "RFC 3576 server" to the aaa profile.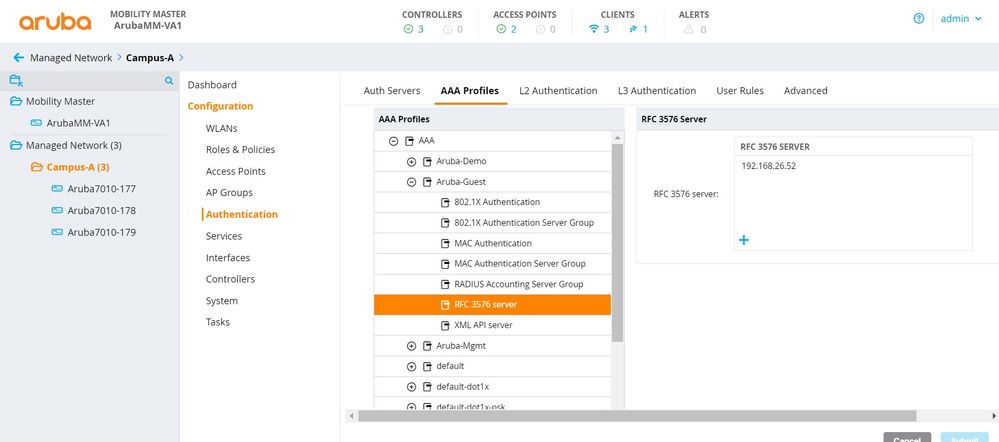
2) Ensure that you have configured the VRRP-IP and VRRP-VLAN in the cluster group-profile.
Command: show lc-cluster group-profile Campus-A-Cluster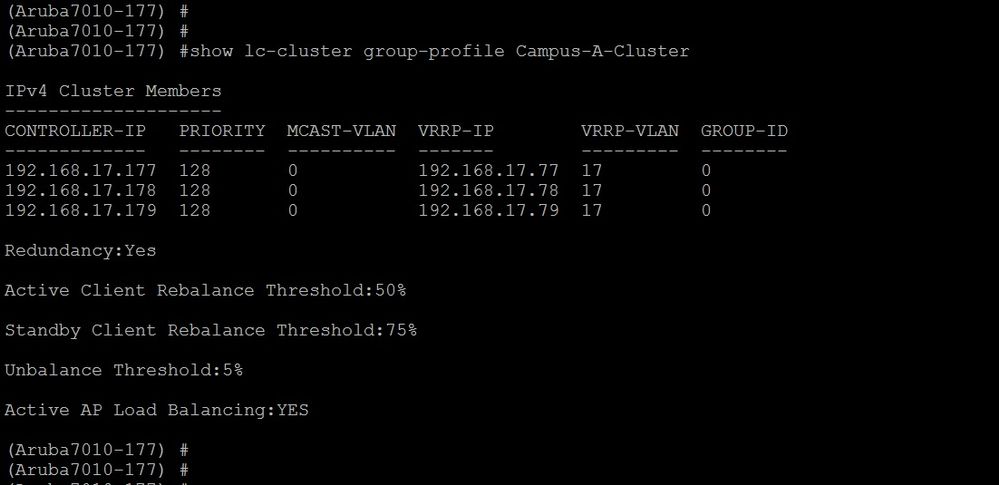
3) Check whether the cluster is L2 Connected.
Command: show lc-cluster group-membership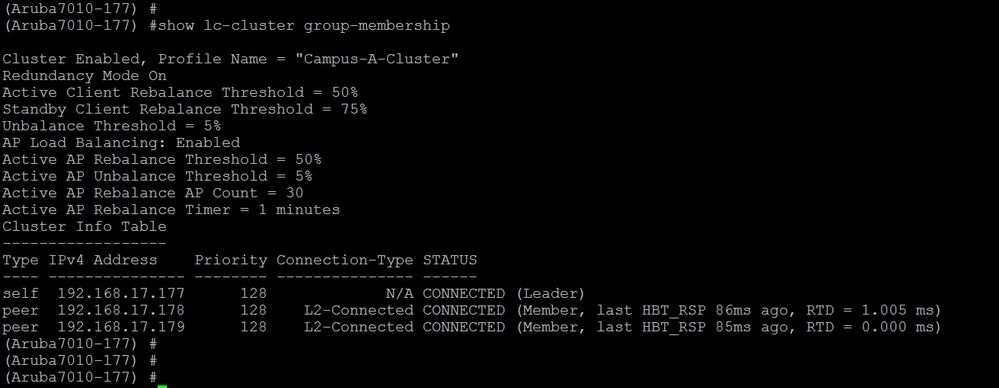
4) Verify the System created VRRP instance
Command: show vrrp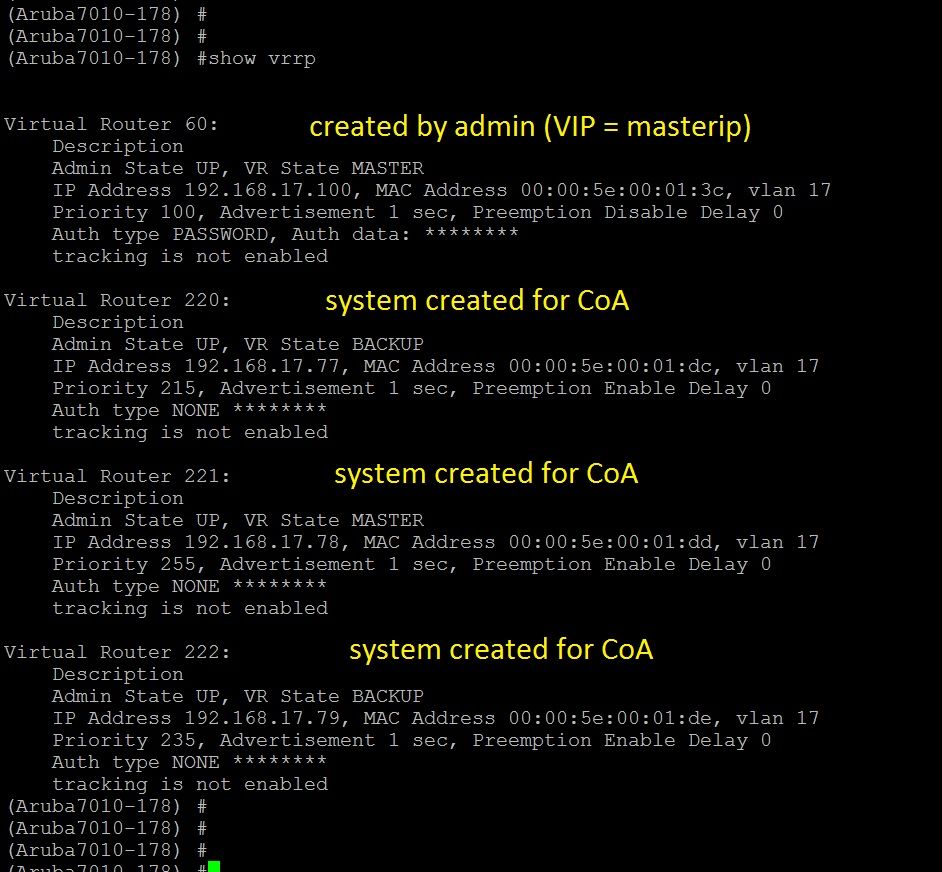
5) Dynamic Authorization request messages are usually sent by a RADIUS server to a network access server (NAS) device.
If the NAS device is able to successfully implement the requested authorization changes for the user session, it will respond with a DM-ACK or CoA-ACK, otherwise a DM-NAK or CoA-NAK is sent.
Since the DA request is initiated from the Server to Client, be careful about NAT in the Gateway or Controller.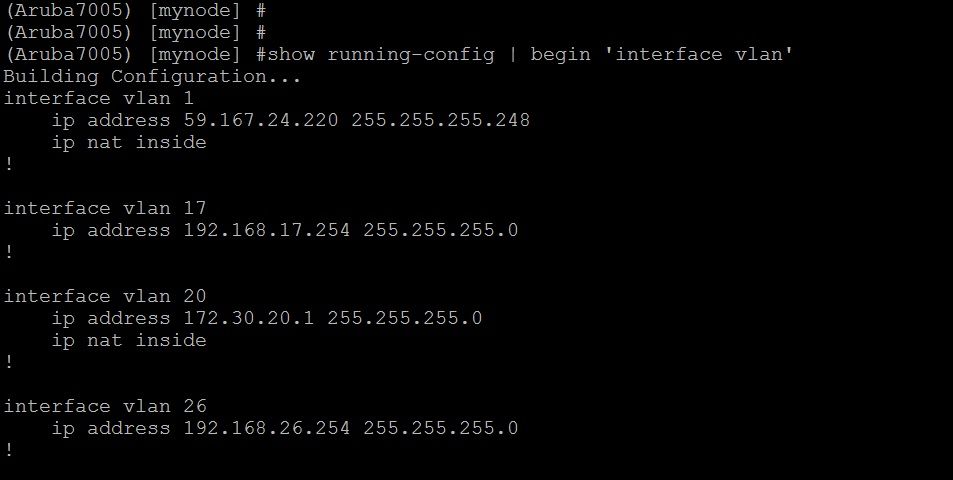
6) Verify in Clearpass Access Tracker record, NAD-IP-Address is the Cluster VRRP IP address (In this Eg: VIP2) and Src-IP-Address is the controller IP / Managed Device IP (In this Eg: MC2)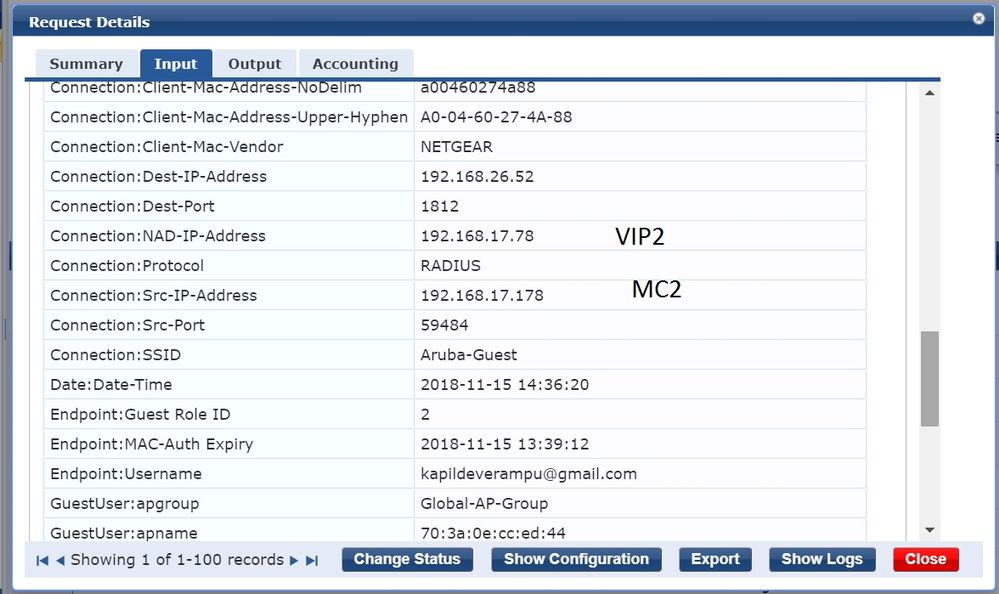
7) In Clearpass, under “Configuration » Network » Devices”, add
Cluster VRRP IPs as NAD.
Controller IPs as NAD.
Don’t forget to check “Enable RADIUS CoA”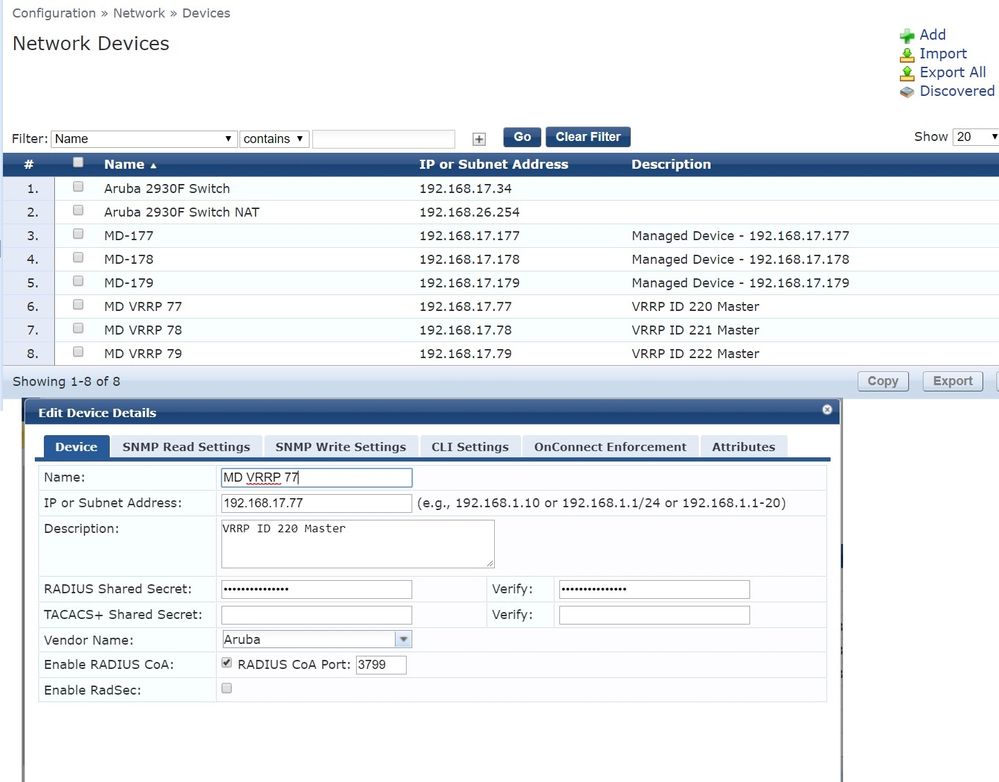
Successful Disconnect.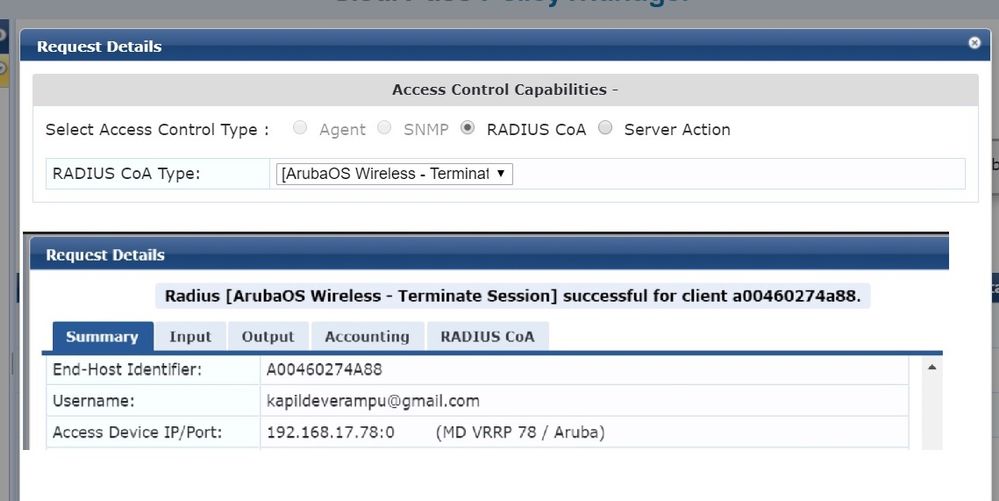
User Table: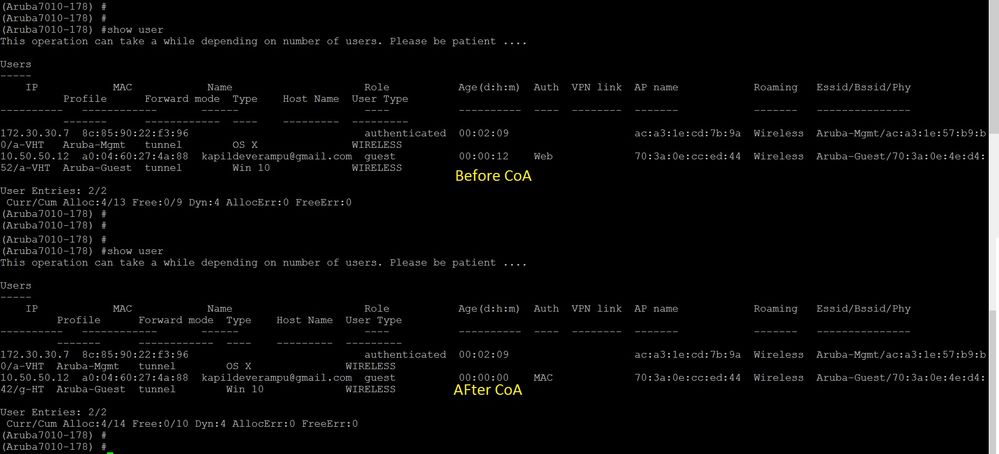
If there are any other points that needs to be added to this checklist, please post your comments here. This will help others who are troubleshooting this issue.
Hope you find this post useful. Please let me know your feedback!
Regards,
Kapil