The requirement from the customer was a single ssid for onboarding BYOD, onboarded BYOD and non-BYOD corporate laptops, so i can't do multiple SSIDs for these features. To connect to that SSID, users are using 802.1X authentication.
I had created the following service
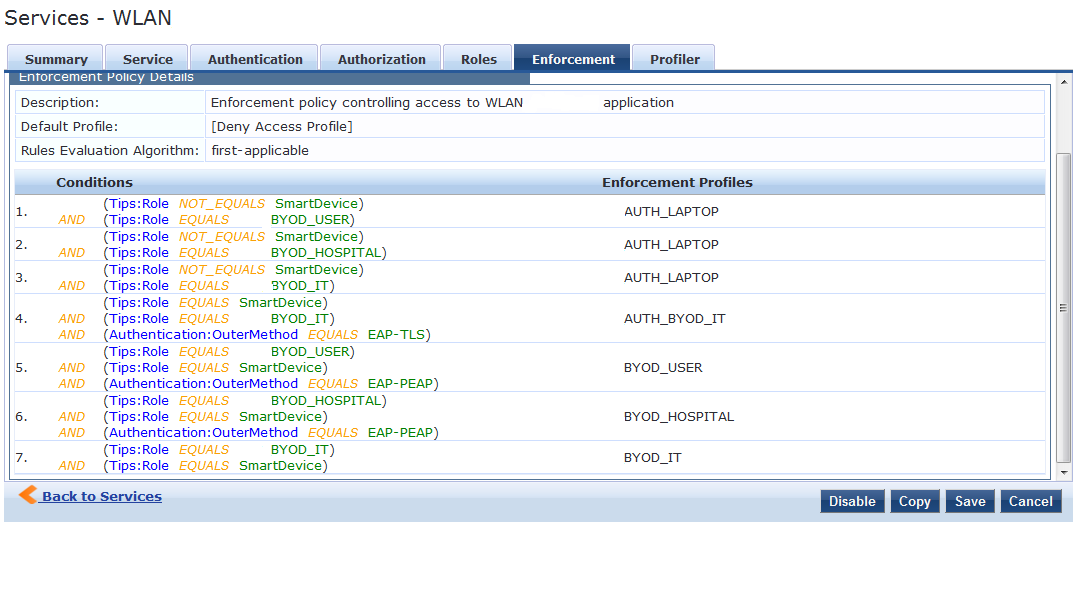
I will have users in 3 separate security groups(User, Hospital, IT). The first 3 conditions will provide user with a non-onboarded role for full access to the network. It am testing on the IT roles at the moment. If user is using a smart device, belongs to the BYOD_IT grouping and is not using EAP-TLS, the will be assigned to a pre-provisioned role (BYOD_IT).
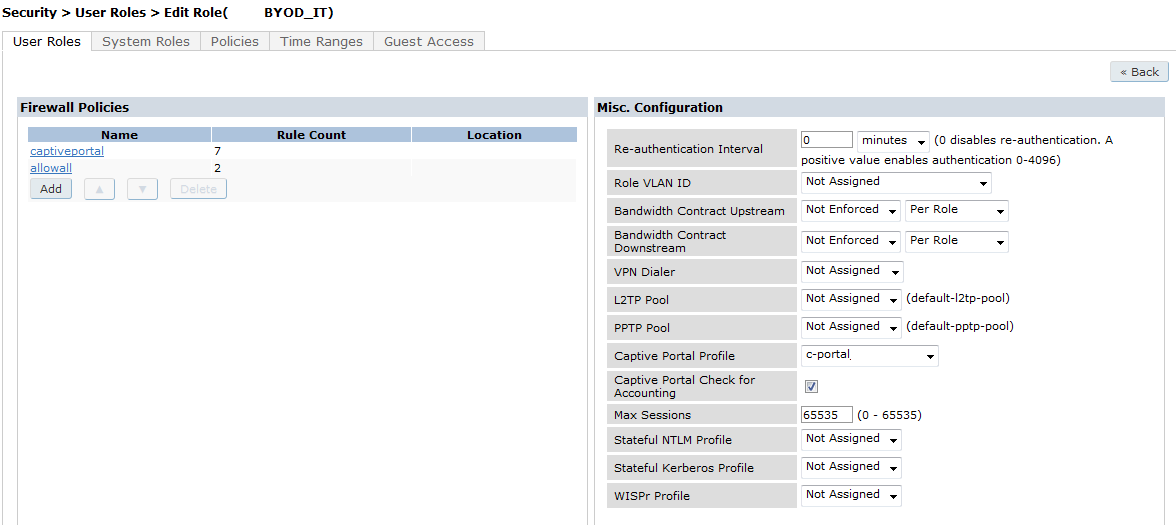
Now in captive portal, I will create a matching role.
Captive portal profile is as below.
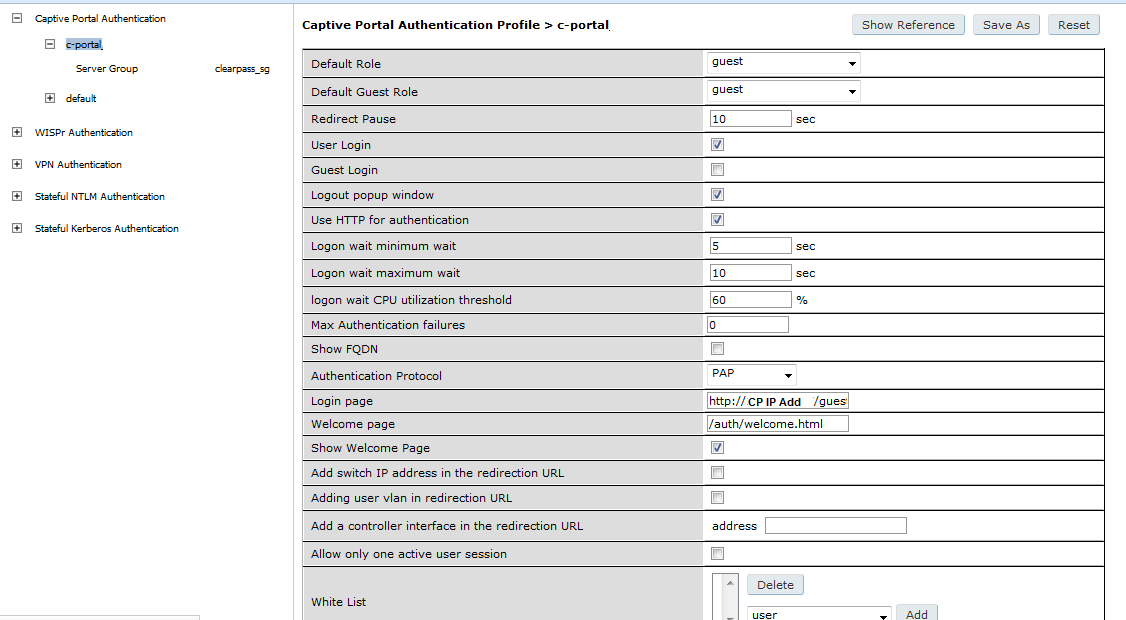
When users attempt access any webpage thru their non-onboarded BYOD on iPAD, they are directed to the clearpass URL provisioning URL but the page shows "Safari cannot open the page because too many redirects occured". the ipad was assigned the preprovisioned role of BYOD_IT correctly. Why am I not able to see the provisioning page?
I had tried removing the captive portal profile and for the BYOD_IT role and provided a allowall policy without the captive-portal policy, I am able to see the provisioning page. However I will a a profile installation failed when I attempted to install the device profile, I am in the midst of downloading the latest cumulative patch to see if it resolves the profile installation problem.