Hi everyone,
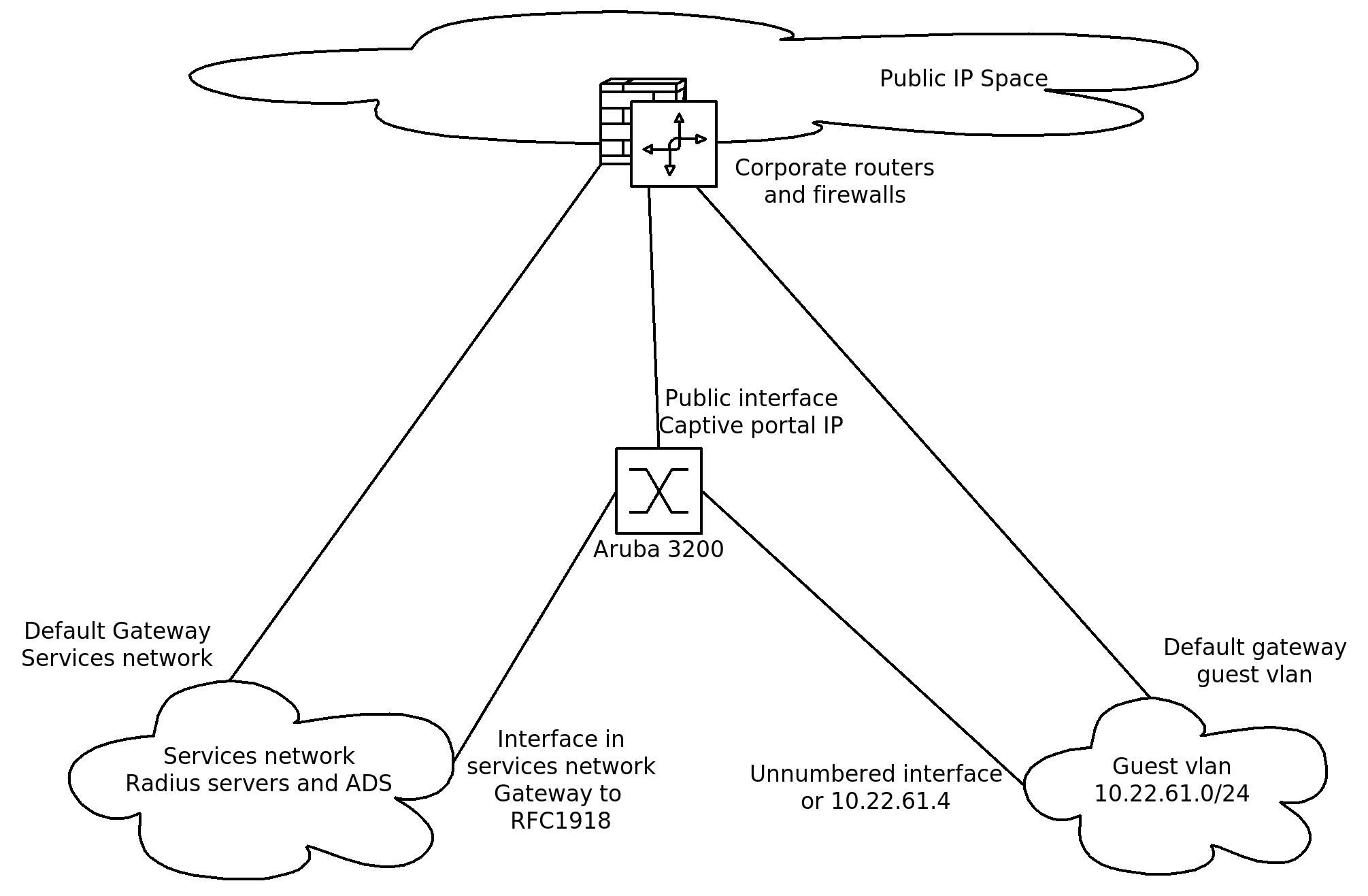
I have tried to create a little drawing of the setup as it is intended. Some explanation:
The guest vlan speaks for itself. The default gateway in the guest vlan is 10.22.61.1 and the Aruba is either unnumbered or it has IP 10.22.61.4. If the interface in the guest vlan is unnumbered the client doesn't receive the redirection to the Captive portal. If the interface is numbered the client does receive this redirection but most of the time it is not able to reach the portal. And if it is able to reach the portal, logging in on the portal results in a Access Denied message. This last access denied was caused by a NAT rule on the corporate firewalls, at least if I understand the following log correct.
May 29 17:42:13 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> RX (sock) message of type 33, len 4672
May 29 17:42:13 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> Received Captive Portal/WISPr config request for 10.22.61.211
May 29 17:42:13 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> Received CP/WISPr cfg request from 10.22.61.211 0.0.0.0
May 29 17:42:13 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> cp_dns_ip = 95.130.233.47
May 29 17:42:13 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> Opened CP customization file /flash/upload/custom/TC3-Guest-cp_prof/cpformat.txt
May 29 17:42:13 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> theme=1, logo=/auth/default1/logo.gif, logintext=/flash/upload/custom/TC3-Guest-cp_prof/logintext.html, policytext=/upload/custom/TC3-Guest-cp_prof/acceptableusepolicy.html
May 29 17:42:13 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> custom color=, background= login_page=/upload/custom/TC3-Guest-cp_prof/index.html welcome_page=/auth/welcome.html
May 29 17:42:13 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> ip=10.22.61.211, prof=TC3-Guest-cp_prof, essid=TC3GUEST, login=/upload/custom/TC3-Guest-cp_prof/index.html, wispr_enable=0
May 29 17:42:20 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> RX (sock) message of type 33, len 4672
May 29 17:42:20 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> Received Captive Portal/WISPr config request for 95.130.233.161
May 29 17:42:20 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> Received CP/WISPr cfg request from 95.130.233.161 95.130.233.47
May 29 17:42:20 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> Tx message to Sibyte. Opcode = 17, msglen = 188
May 29 17:42:20 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> RX (sock) message of type 33, len 4672
May 29 17:42:20 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> Received Captive Portal/WISPr config request for 95.130.233.161
May 29 17:42:20 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> Received CP/WISPr cfg request from 95.130.233.161 0.0.0.0
May 29 17:42:20 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> Tx message to Sibyte. Opcode = 17, msglen = 188
May 29 17:42:41 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> Rx message 0/67108864, length 247 from 127.0.0.1:8345
May 29 17:42:41 aruba01 authmgr[1564]: <124004> <DBUG> <aruba01 172.30.27.1> stm_message_handler : msg_type 3007
The Aruba is not routing between netwerks.
The default gateway of the aruba is the public interface.
The gateway to RFC1918 networks is the default gateway of the services network.
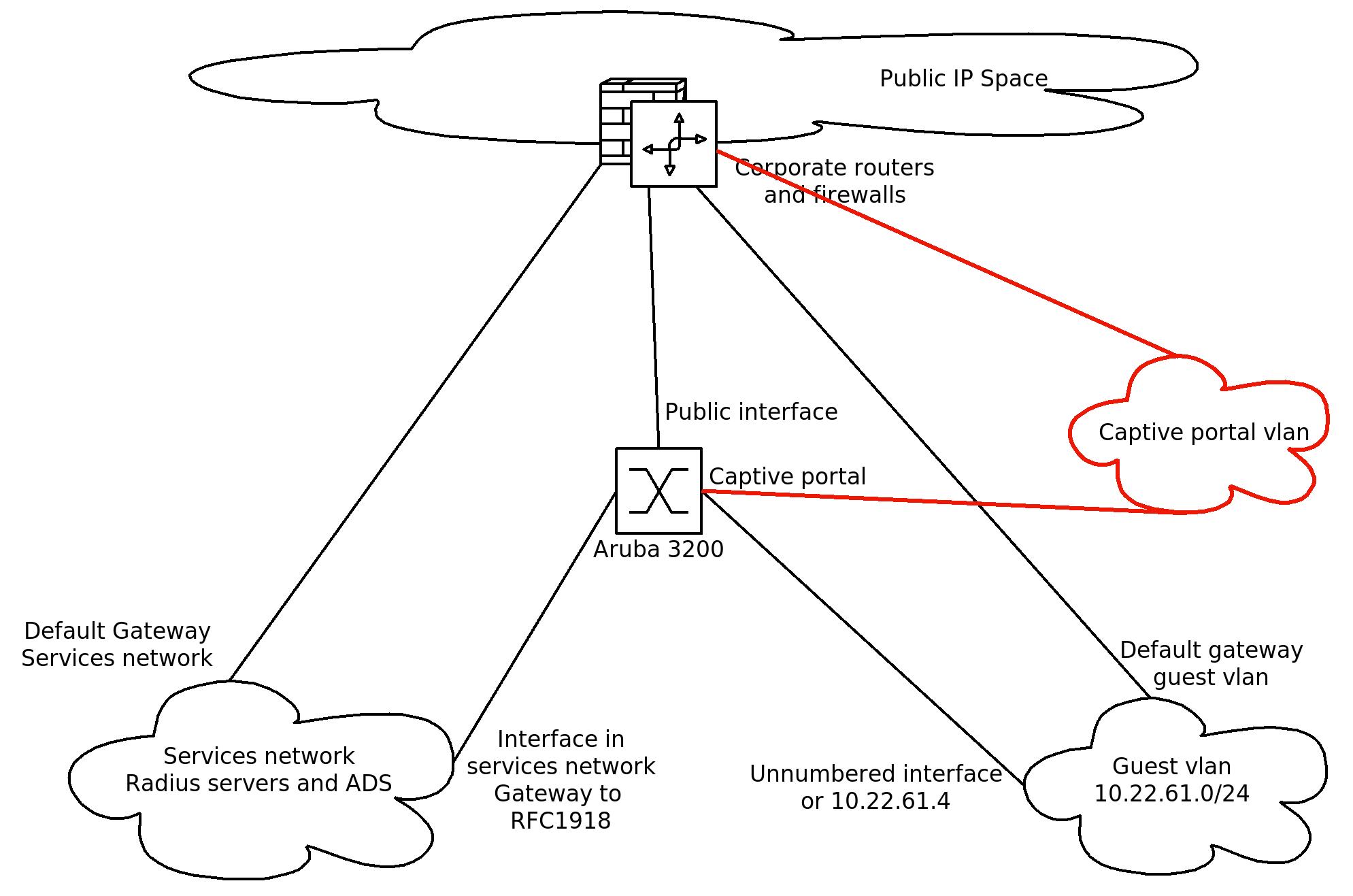
I'm currently thinking about changing this a little bit to a setup where the captive portal IP is in a seperate vlan which has full routing without any access list to the guest vlans. This routing will then still be done through the central firewalls but I can set this up in such a way that their will never be any access list between those vlans.
This would then be the next setup:
Jan Hugo Prins