Hi,
Short update.
I replaced the:
(Authorization:[Time Source]:Now DT LESS_THAN %{Endpoint:MAC-Auth Expiry})
with this one:
(Date:Date-Time LESS_THAN %{Endpoint:MAC-Auth Expiry})
So now this is working as expected, but now a new problem arises.
What I want is use a click through portal, and then you have to use Anonymous Authentication for that. It is in combination with Cisco Wireless, Got that working as well. We want the Guests to go through authentication (click through) once a day. So that is why I wanted to use the Endpoint:MAC-Auth Expiry feature. This is working now, but now after the MAC expiry, I am getting a deny access for that MAC address because when I take a look at access tracker, the authentication source stays empty -> none. Why is this? Because the WEB Auth taking place first?
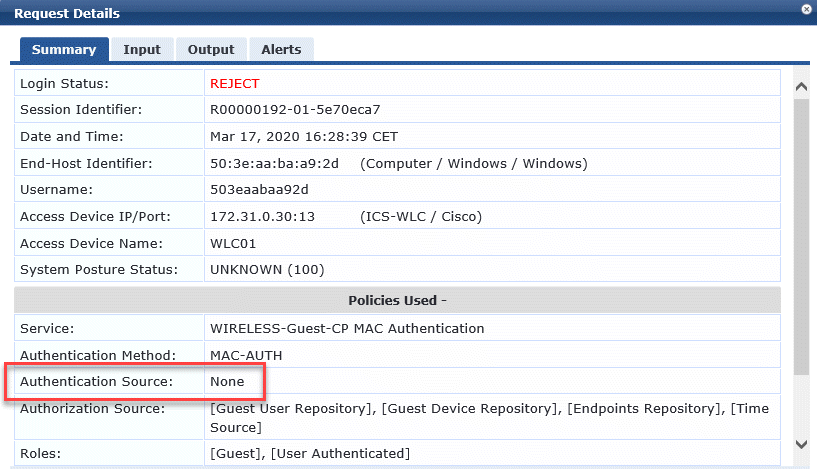
At the alerts TAB however, this is shown:

The endpoint is still in the database,unknown, but I am using:
Authentication Methods: [Allow All MAC AUTH]
So that cannot be the reason. So, it must be the empty Authentication source?
I am puzzled here. Anyone a suggestion?
Thx. Best regards, Martin