I’ve seen little information about this issue on this site or elsewhere, so I thought I would post about this solution we found at a client site. If you’re having difficulty getting Windows clients to connect to an EAP-TLS network using TLS 1.2, read on…
(All the usual disclaimers apply: modifying the Windows registry can be hazardous to your health. Don’t proceed without the knowledge of what you’re doing and a good backup.)
Wireless clients were connecting to an EAP-TLS network using TLS 1.0, even though ClearPass 6.6.7 was in use (TLS 1.2 support was added to ClearPass several versions prior). Packet captures confirmed that clients were connecting to the network using TLS 1.0. The security department was requiring a move to TLS 1.2.
To disable TLS 1.0 and 1.1, modifications were made to the Windows registry according to this document:
https://technet.microsoft.com/en-us/library/dn786418(v=ws.11).aspx#BKMK_SchannelTR_TLS10
By adding the appropriate DWORD values to this key:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols
We can disable TLS 1.0 and 1.1, leaving only 1.2 available.
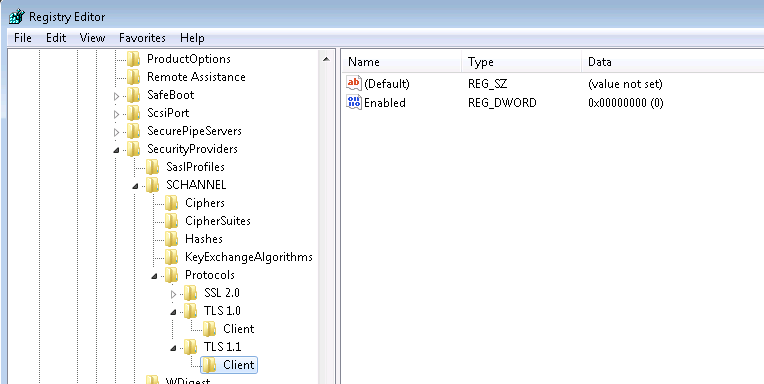
After making this change, Windows 10 clients could connect using TLS 1.2. However, Windows 7 clients would no longer connect at all.
Much searching unearthed this article, which says that Win 7 needs additional registry values set:
https://support.microsoft.com/en-us/help/2977292/microsoft-security-advisory-update-for-microsoft-eap-implementation-th
(This article references a Windows patch that came out in 2014. We assumed that it had long since been downloaded to the computer, but if this process doesn't work, you might want to make sure you’ve got the patch.)
Per the article, we added the ‘TlsVersion’ DWORD with a value of 0xC00 to this branch:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\RasMan\PPP\EAP\13
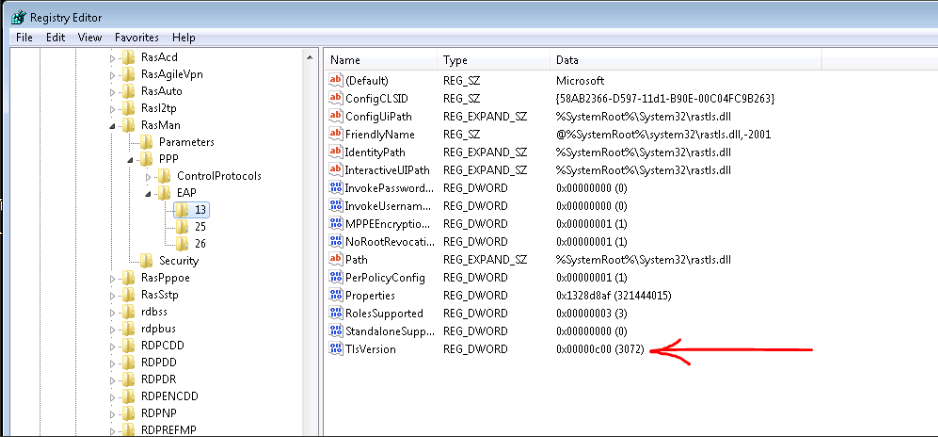
With these two registry changes and a reboot, Windows 7 computers connected happily using TLS 1.2, as shown by this packet capture:
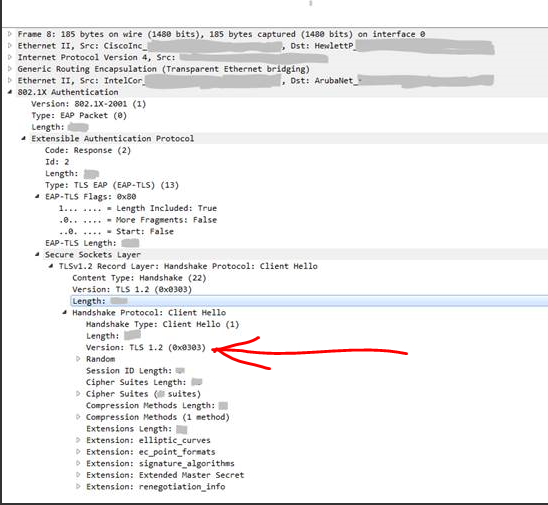
Also, if you don’t want to do packet captures, you can be fairly certain that EAP-TLS 1.2 is in use by disabling TLS 1.0, 1.1, AND 1.2 using the first article mentioned above. Verify that the computer will not connect. Then re-enable only TLS 1.2, and test again. At that point, you’re likely connecting with TLS 1.2
Note: reboots are usually required between these changes.
Enjoy!