Recently, I’ve been with enterprise clients that are looking to restrict their wireless and wired 802.1x sessions to valid domain devices that users log into. In terms of authenticating a Windows client, you can limit secure access to a Machine Authentication OR a User Authentication in Windows. These enterprise clients are looking for valid domain machines and providing elevated rights on a per-user level on non-BYOD devices.
Clearpass allows us to combine a Machine Authentication AND User Authentication to guarantee that the connecting device is a member of the domain while still providing per-user roles and ACLs.
The following was completed using Clearpass 6.4.1,a Windows 2012 backend, a 7005 running 6.4.2.2, and an AP-225.
From a high level, here's what I will be discussing:
1. We will create a Boolean Clearpass Endpoint Attribute
2. We will create an Enforcement Profile that sets the Endpoint Attribute
3. We will then apply that Enforcement Profile to a successful Machine Authentication in an Enforcement Policy
4. We will create a Clearpass Role to reference this Endpoint decision
5. We will adjust the existing Enforcement Policy and combine the Machine Authenticated Clearpass Role and the User Authentication
6. We will talk about how to roll this out in an enterprise environment
7. Troubleshooting and verification of this design
8. Caveats to this design
1. Creating a custom Clearpaass Endpoint Attribute
The first step is to create a custom Clearpass Endpoint Attribute. In Clearpass, go to the following:
i. Administration > Dictionaries > Attributes
ii. Click the "+Add" button in the top right-hand corner
iii. Fill in the attribute similar to the following screenshot:

Make sure the "Entity" is set to "EndPoint" and to select "No" for "Is Mandatory" and "Allow Multiple."
iv. Click the "Save" button
2. Creating an Enforcement Profile
Next, we are going to create an Enforcement Profile to set our newly created Endpoint Attribute.
i. Go to Configuration > Enforcement > Profiles
ii. Click the "+Add" button in the top right-hand corner
iii. Go to "Template" > "Clearpass Entity Update Enforcement"
iv. Click "Attributes" > "Type" > "Click to add..."
v. Type = "Endpoint" : Name = <Name that you provided in the previous example> : Value = Checked Box / "true"
A successful configuration of the Attributes section will look like the following:

Here's a summary of this Enforcement Profile:

3. Modifying the Enforcement Policy
The third step is to add the newly created Enforcement Profile to an Enforcement Policy. The easiest way to do this is to go to the wired or wireless service and select the Enforcement Policy. In this example, I will apply this to an 802.1X wireless service.
i. Go to Configuration > Services > "Your 802.1X wireless service"
ii. Click on the "Service" tab and select "Authorization" (if it's not already selected)
iii. Click on the "Authorization" tab
iv. Select "Endpoints Repository" from the "Additional authorization sources..." (if it's not already selected)
v. Click on the "Enforcement" tab
vi. Click on the "Modify" button to the right of the currently selected Enforcement Policy
vii. Click on the "Rules" tab
viii. Click on the "Add Rule" if you do not have a "Tips:Role EQUALS [Machine Authenticated]."
ix. If you do have a "[Machine Authenticated" rule, click the "Edit Rule" button. Type = "Tips:Role EQUALS : [Machine Authenticated]"
x. Enforcement Profiles > Profile Names > "Enforcement Profile from Step 2" + "An appropriate Aruba User Role"
(An aside)
The user role that is given in step x. can be a quarantined role that only allows access to DHCP, DNS, and AD. It will take a user authentication for a machine to be given the proper Aruba user role and credentials.
(Back to business)
xi. Click the "Save" button
xii. Click the next "Save" button
An example of a successful configuration will look like the following:

4. Creating a Clearpass Role for the Endpoint Attribute
The next step is to create a Clearpass Role that we will tie to the Endpoint Attribute in Step 5.
i. Go to Configuration > Identity > Roles
ii. Click the "+Add" button in the top right-hand corner
iii. Create a role similar to the following screenshot:

iv. Click the "Save" button
5a. Tying together the Clearpass Role, the EndPoint Attribute, and the Enforcement Policy
Let's begin by going to the Role Mapping that is being employed by the wireless 802.1X service.
i. Go to Configuration > Services > "Your 802.1X wireless service" > Roles
ii. Click on the "Modify" button to the right of the currently selected Role Mapping Policy
iii. Click on the "Mapping Rules" tab
iv. Click on the "Add Role" button
v. Click on "Type" > "Click to add..."
vi. Type = Endpoint : "Attribute from Step #2" : EQUALS : true
vii. Actions > Role Name > "The Clearpass Role created in Step 4"
The above steps will look similar to the following screenshot:

(Aside)
You may be wondering what's up on line #12 in the above graphic. A device will receive the default role from a role mapping policy if it does not match any of the conditions. Often, I create a "Deny All" role in Clearpass to anything that does not match. The problem is that a "[Machine Authentication]" is defined in the Enforcement Policy, not in the Role Mapping. By doing something similar to line #12, you'll guarantee that Access Tracker will not set the default role mapping to this connection, on-top of the "[Machine Authentication]"
(Back to business)
5b. The next step is to tie together everything we've done in the Enforcement Policy definitions.
i. Click on the "Enforcement" tab
ii. Click on the "Modify" button to the right of the currently selected Enforcement Policy
iii. Click on the "Rules" tab
iv. Click on the "Edit Rule" on your currently defined 802.1X wireless enforcement profiles.
v. Adding the following to these definitions, Type = Tips : Role EQUALS : "Clearpass Role defined in Step 4"
This will look similar to the following screenshot:

The above definition states that you need to have User credentials AND the device that you're authenticating with must have Machine Authenticated at some point. Make sure to select ALL in the rule definition, rather than ANY. The above should be an "AND", not an "OR."
6a. Windows wireless / wired networking settings
The first step in deploying this design is to make sure that your Windows clients are configured correctly. They must be setup for Machine (Computer) or User Authentication.
i. Either through GPO or a manual configuration, go to the properties of the wireless network:

ii. Click on the Advanced Settings > 802.1X settings > CHECK "Specify Authentication Mode" > "User or Computer Authentication"

6b. Rolling out this solution into an enterprise
i. The next step is probably the most important to remember about this design - the client MUST Machine Authenticate in order for this design to work. The best way to get this to happen is for a Windows client to reboot and attempt to authenticate to the network as the device itself. This will happen automatically if a Windows client is successfully configured with the above settings.
ii. The problem with "rolling this out on the weekend" is that not all of the devices will Machine Authenticate on Monday morning unless they're rebooted. The best thing to do is to give the users a week or two to reboot their machines and populate the Endpoints database.
iii. To verify the Endpoints database, go to Configuration > Identity > Endpoints > Filter on "Attribute" > contains > "The attribute from Step 2." You can then compare the hostnames in this section to the Computers OU in your AD directory. This will help you to be proactive with your users and remotely reboot the hostnames that are not in the Endpoints database.
iv. Finally, you will enable the Role as part of the decision process, as in step 4.x.
7. Troubleshooting and verifying this design
i. Here is a screenshot of the design successfully working:

ii. Let's look at a screenshot of entry #2 in Access Tracker:
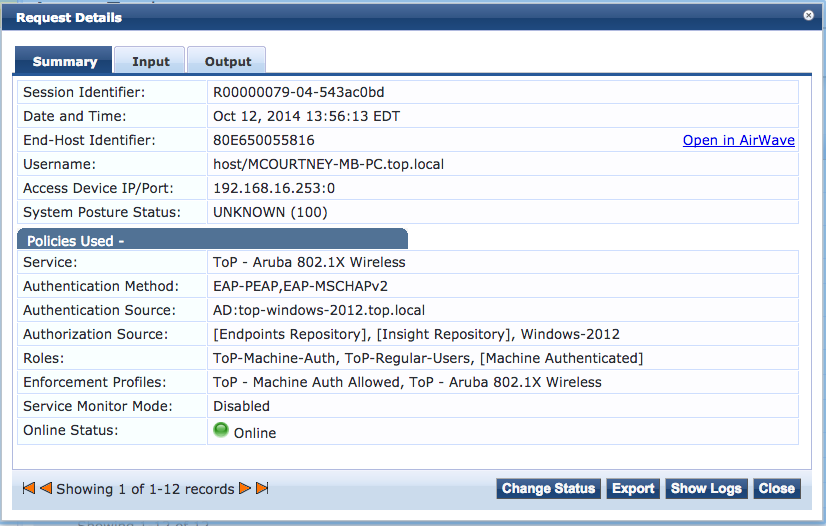
This device is doing [Machine Authentication] and using the "host\" format as the username.
The first "Enforcement Profiles" for this connection is the Profile that we created in Step 2.
iii. Let's look at a screenshot of the Output tab to see what that Enforcement Profile is doing:

Under the "RADIUS Response" we see that we are settings the "Endpoint:ToP-Machine-Auth-Device" to equal "true" - this is exactly what we're expecting!
iv. Next, let's examine Access Tracker #1 from step 7.1. This occurs when you hit "CTRL+ALT+DELETE" and log in with domain credentials. Let's take a look at this screenshot:

Here we see that I'm logging in with my AD username in the "DOMAIN\username" format. I'm also now categorized as a "ToP-Domain Device" that we defined in Step 4. The main thing to notice is that the "Enforcement Profiles" for this connection are much different than the last authentication. This allows us to log into this Machine Authenticated domain device AND provide granular user authentication.
v. Let's verify that the Endpoint Attribute has been set. Click on Input > Computed Attributes and scroll all the way to the bottom. You will see the Endpoint Attribute set, similar to the following screenshot:

vi. Finally, click on the Output > RADIUS Response:

Here we can see that I'm setting an Aruba user role that provides administrator access. This is different than the user role that was set on a Machine Authentication. We're now providing granular user access to this connection.
We've designed a solution that provides Machine Authentication AND User Authentication!
8. Caveats
i. The first caveat to this guide is that it leaves out Apple Mac devices. The enterprises that have wanted this type of configuration have not had large Mac deployments. They have gone into the Endpoint repository, find the specific wireless or wired MAC, and then manually select the Endpoint Attribute.
ii. The second caveat is that you may want to purge the Endpoints database every 6 months or so to make sure that all of the devices that are connecting to the network are still valid AD domain machines. One would work through the steps in section 6b., in reverse. First, you would remove the Endpoints Attribute from the decision process in the Enforcement Policy. Then, you would allow a week or so to pass; the domain machines will re-populate the Endpoints database in Clearpass. At that point, you could once again add the Endpoints Attribute to the wireless or wired decision process in the Enforcement Policy.
Thanks for taking the time to read through this "How-to." I hope that you were able to get something out of this advanced Clearpass configuration.
Let me know if there are any questions or follow-ups - I would love to hear them!
Thanks!
-Mike
#7005