Profiling? What profiling methods are you doing? What are your Role mappings actually looking for?
Original Message:
Sent: Oct 06, 2022 05:40 AM
From: Martin Reher
Subject: Network access control with Aruba ClearPass and Siemens Switch
Hi,
i am currently trying to get 802.1X (not MAC-Auth) on Siemens XC208G against ClearPass up and running.
So far the "Guide" provided is very helpfull. I am currently stuck at NOT receiving an "End-Host Identifier" in the Radius request. This is leading to ClearPass not beeing able to properly assign Roles based on the Endpoints repository. I Have checked all information i could get on thte Scalance XC208G Switches but it does not mention anything related.
ClearPass is on 6.10.7.187596
Siemens Scalance XC208G is on V04.03.01
Any help would be highly appreciated
------------------------------
Martin
Original Message:
Sent: Jul 07, 2020 09:24 AM
From: Isabel Staaden
Subject: Network access control with Aruba ClearPass and Siemens Switch
As a result of digitization, IT (Information Technology) and OT (Operational Technology) are growing closer and closer together, leading to an increasing number of IT-based systems in OT. These systems are potentially not under the control of IT operations and represent a possible security gap, so the use of network access control systems in OT is becoming increasingly important. Aruba and Siemens formed a strategic partnership to bridge the gap between IT and OT.

This post is about how the network access of a Siemens Switch (Scalance XC216-4C G, Version 04.01.00) can be controlled with Aruba ClearPass (6.8.0). For this purpose, MAC authentication is used. This means, based on the identity of the end systems maintained in ClearPass, these devices are authenticated on the Switch port. If the authentication is successful, the communication on the Switch port is allowed. If the device is not authorized, no communication is allowed.
How to use MAC Authentication:
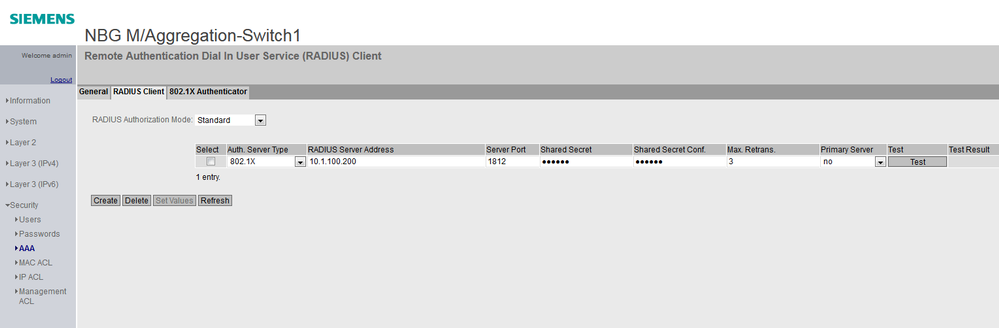
Add ClearPass as RADIUS server on Switch Interface:
On Switch Interface go to Security -> AAA -> RADIUS Client -> Create
Add ClearPass with following information: Auth. Server Type, Server Address, Server Port, Shared Secret
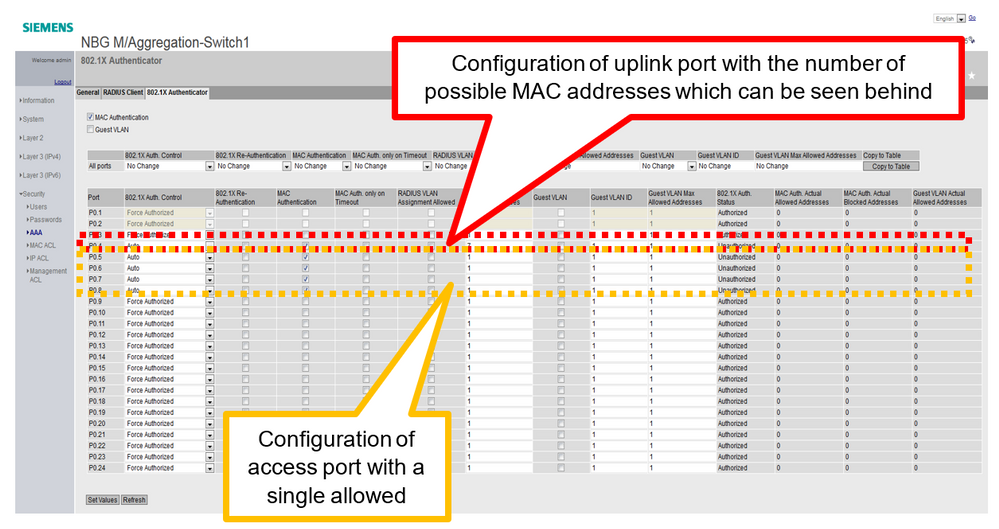
Configure ports to be used by ClearPass:
On Switch Interface go to Security -> AAA -> 802.1X Authenticator
Select Ports, which should be used by ClearPass
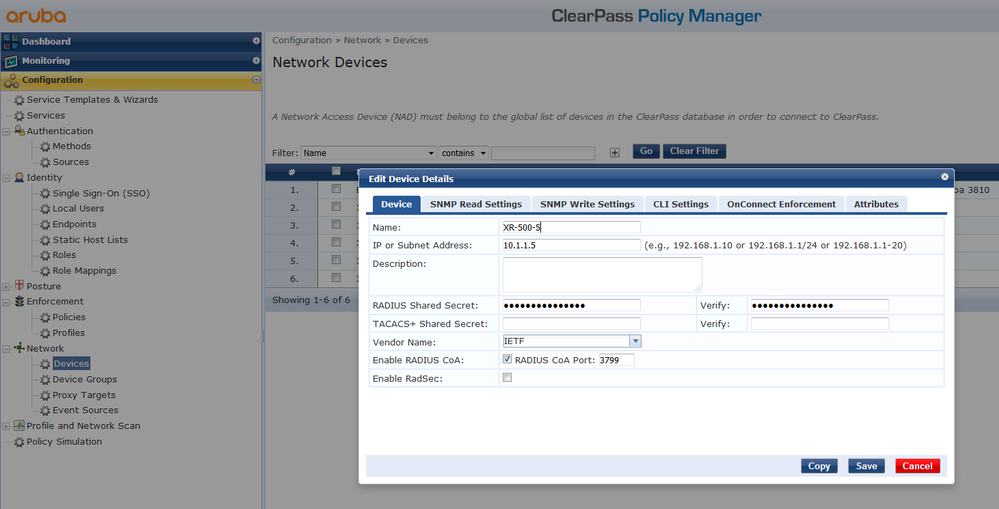
Add Switch in ClearPass:
In ClearPass go to Configuration -> Network -> Devices -> Add Switch
With Name, IP Address and Shared Secret
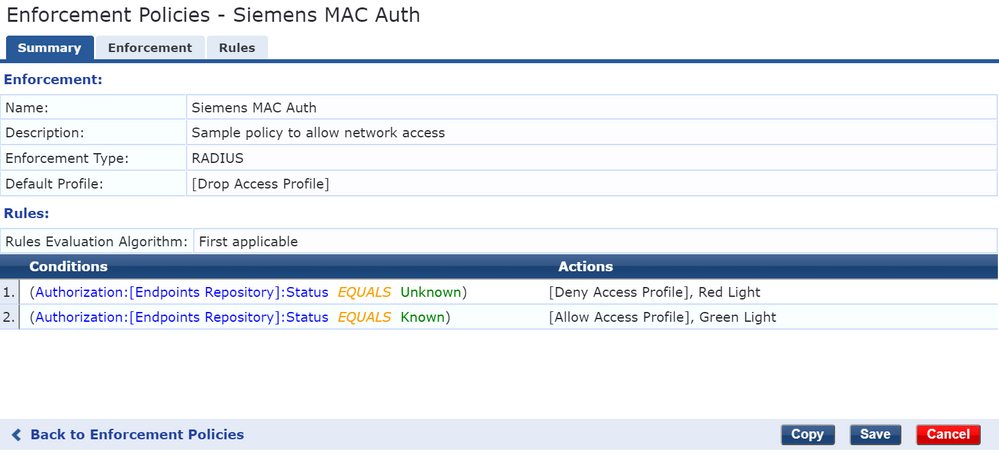
Create new Enforcement Policy:
Configuration -> Enforcement Policies -> Add
Add following parameters:
Enforcement Type = RADIUS
Default Profile = Drop Access Profile
Add 2 rules:
Authorization failed -> Deny Access Profile
Authorization successed -> Allow Access Profile
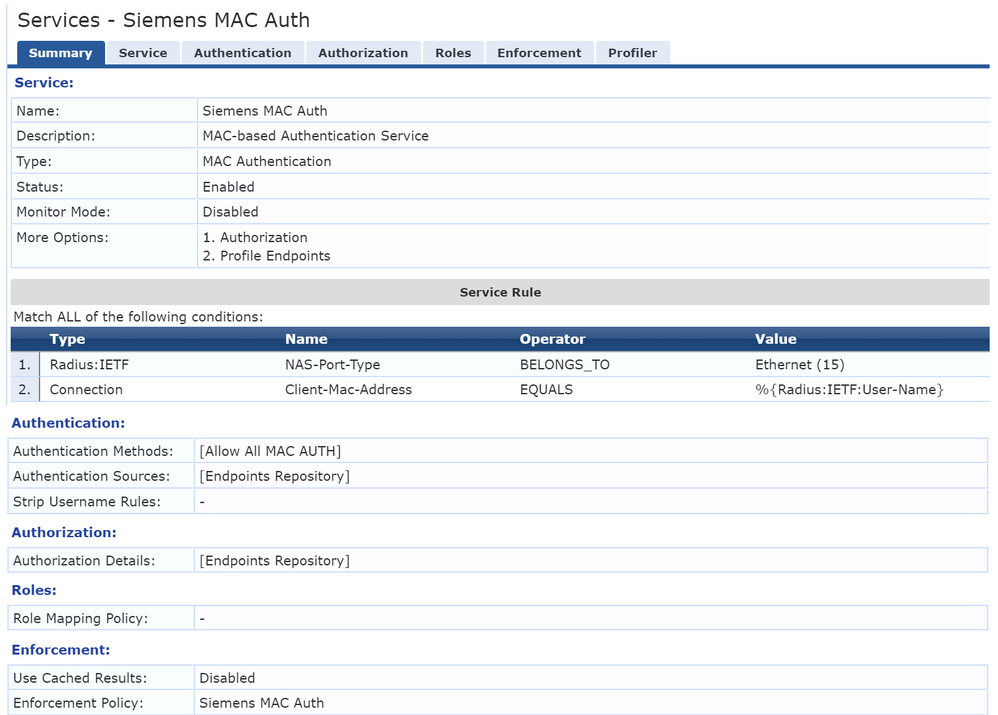
Create new Service:
Configuration -> Services -> Add
Add following parameters:
Type = MAC Authentication
Conditions = NAS-Port-Type belongs to Ethernet & Client-MAC-Address equals Radius Username
Authentication = Method Allow All MAC Auth, Source Endpoints Repository
Authorization = Endpoints Repository
Enforcement = Above created Enforcement Policy
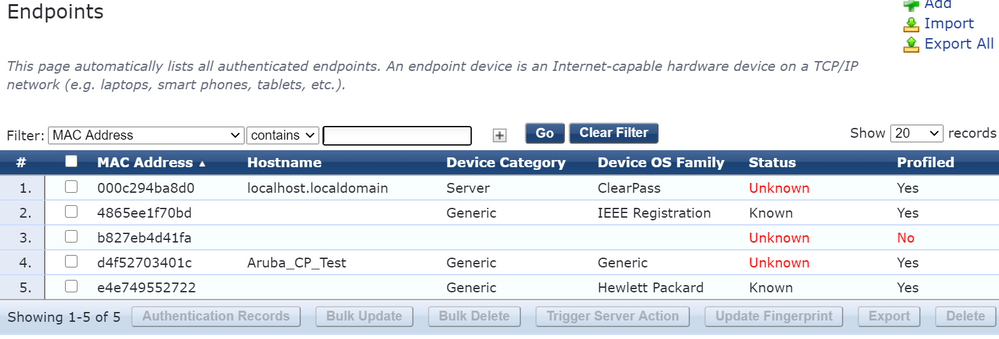
See authorized and unauthorized devices:
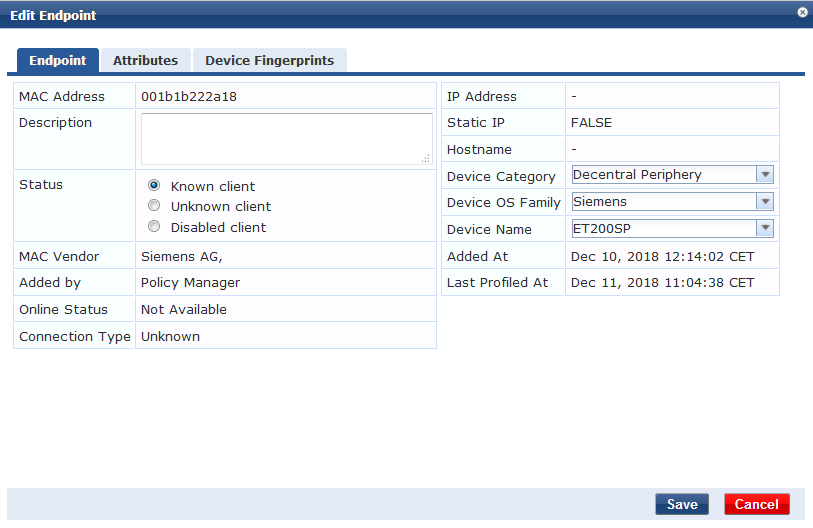
Configuration -> Identity -> Endpoints
Set Status to Known if a device should be authorized or add new devices
MAC Authentication with Aruba ClearPass is the basis for various use cases. It is possible to further process the result of the authentication with another enforcement profile which is used in the enforcement policy. For example, the enforcement profile could trigger a lamp with different colors to give a visual representation of the authentication result.
Addition: MAC Authentication with VLAN assignment:
VLAN Configuration on Switch Interface:
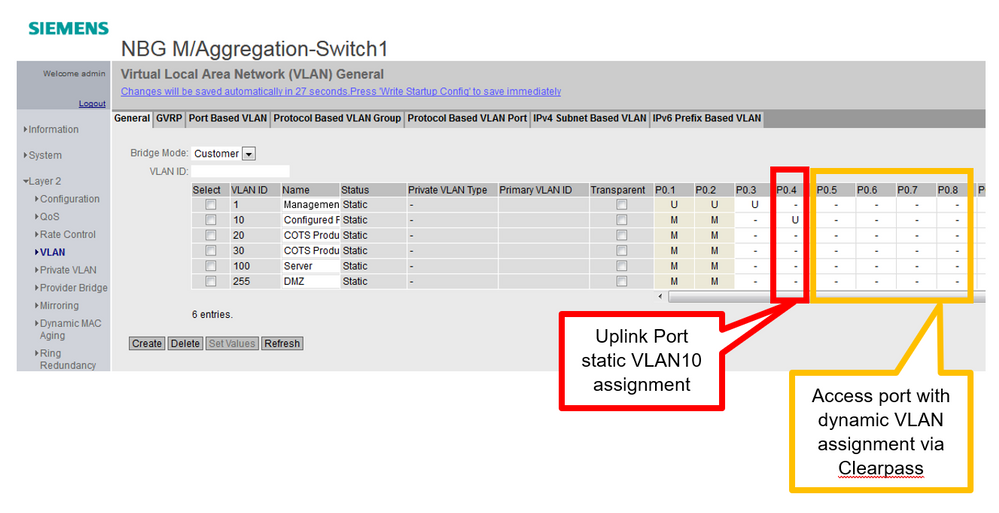
On Switch Interface go to Layer 2 -> VLAN
Assign Uplink Port statically to a VLAN (VLAN10)
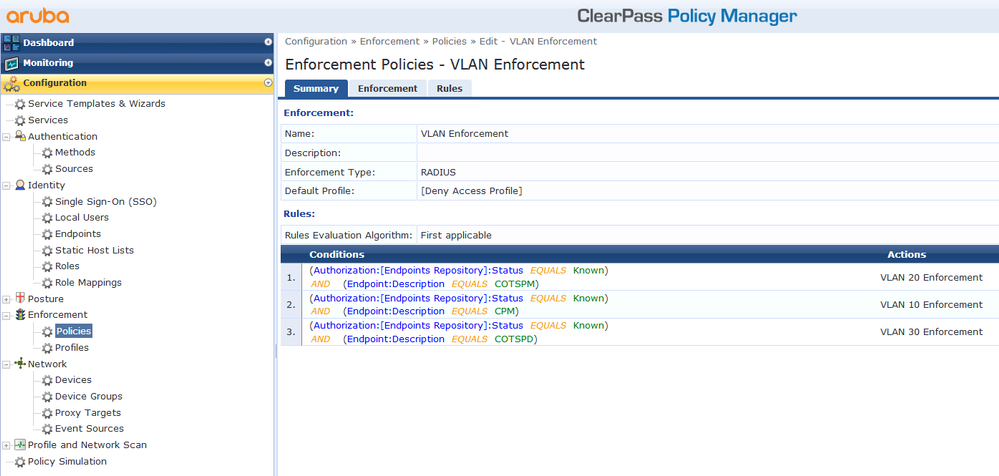
Create new Enforcement Policy:
Configuration -> Enforcement Policies -> Add
Add following parameters:
Name = VLAN Enforcement
Enforcement Type = RADIUS
Default Profile = Deny Access Profile
Add rules for VLAN assignment, for example:
Authorization successed & Description = COTSPD -> VLAN 30 Enforcement
Exchange this Enforcement Policy with the old one in the Service:
Configuration -> Service -> Edit Service (Siemens MAC Auth) -> Enforcement Tab
Select VLAN Enforcement
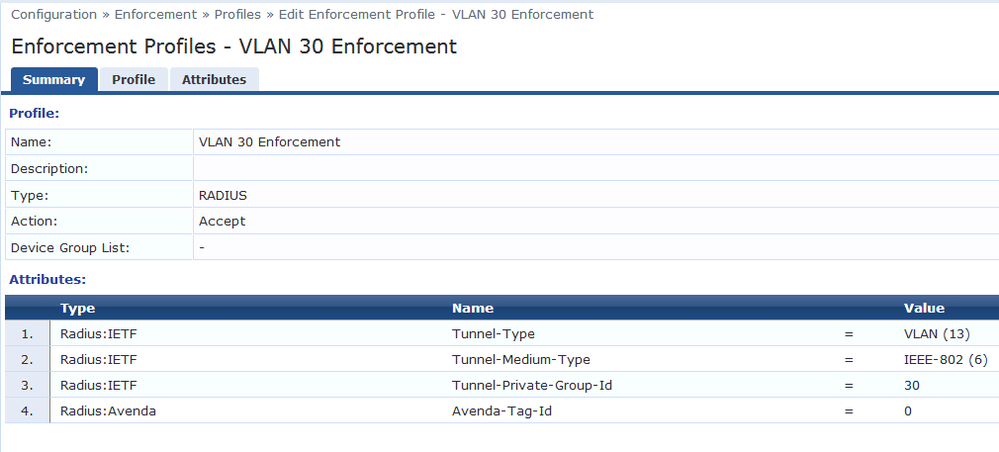
Create Enforcement Profiles based on the Actions in the Rule of Enforcement Policy:
Configuration -> Enforcement -> Profiles -> Add
Add following parameters:
Name (VLAN 30 Enforcement)
Type = RADIUS
Action = Accept
Attributes:
Important to add: Type Radius: Avenda, Name Avenda-Tag-Id, Value 0
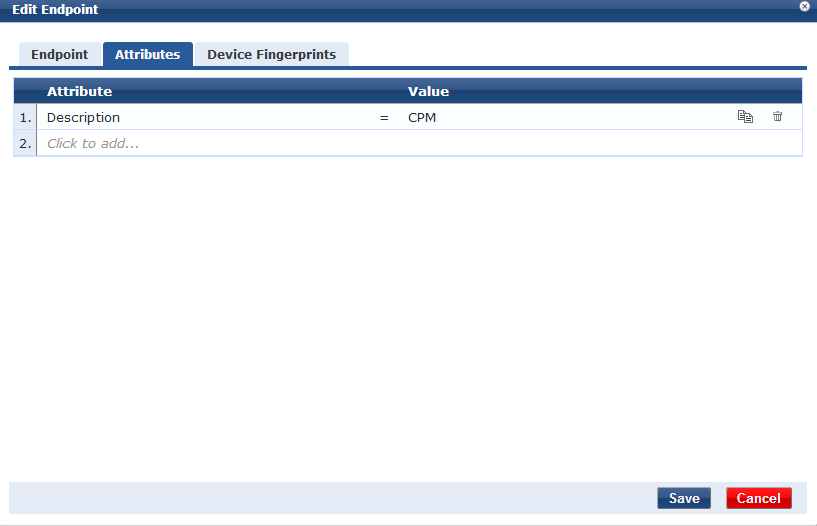
Devices are associated to VLAN based on attributes:
See in Endpoints Repository (Configuration -> Identity -> Endpoints -> Edit)