Hi Dannyjump,
Thanks for the quick response.
I read your document, it's a great guide and helped me with the integration, thanks.
In the document you explain exactly the problem I'm facing, and I understand that the solution is simple, and has two key points,
1. “Force the NAS device to send a username not a MAC address in the Interim Accounting Updates.” Radius:IETF:Username = %{Endpoint:Username}
2. “The second is to use a new Session–Check attribute, as part of the PANW UserID XMLAPI update enforcement profile.” Session--‐Check::Username = %{Endpoint:Username}
Obs. One detail I noticed was the attribute Session--‐Check::IP--‐Addresss--‐Change--‐Notify, in version 6.8.5 this value no longer exists,

So I added the two attributes below,

_______________
Below are my Enforcement Profiles sent in the User Authentication and MAC-Authetication.
USER AUTH W/ MAC CACHING SERVICE
I send three key Enforcement Profiles, the first sends the Aruba-User-Role to the Aruba controller, the second updates the device attributes in the Endpoint Repository and finally sends updates to Palo Alto.
1. “Aruba-User-Role”
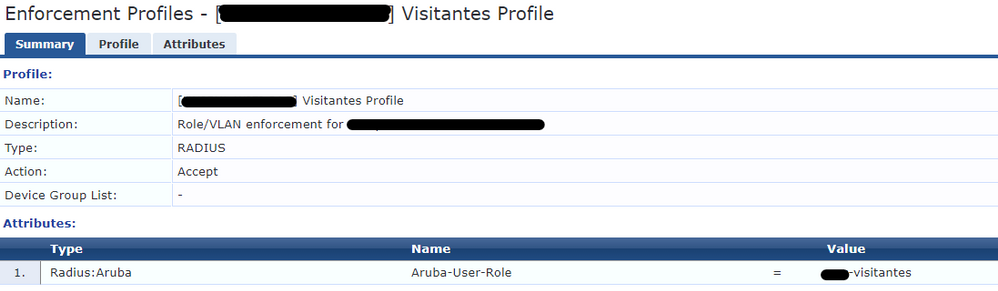
2. “Update Endpoint Repository”
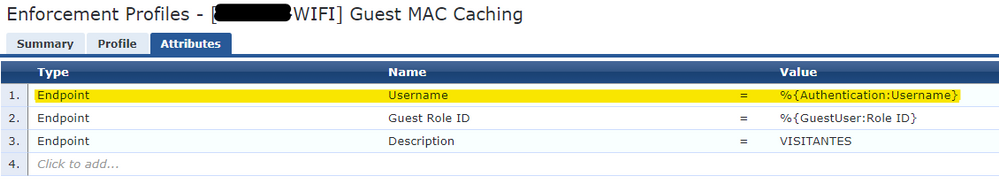
3. “Send Palo Alto Update”
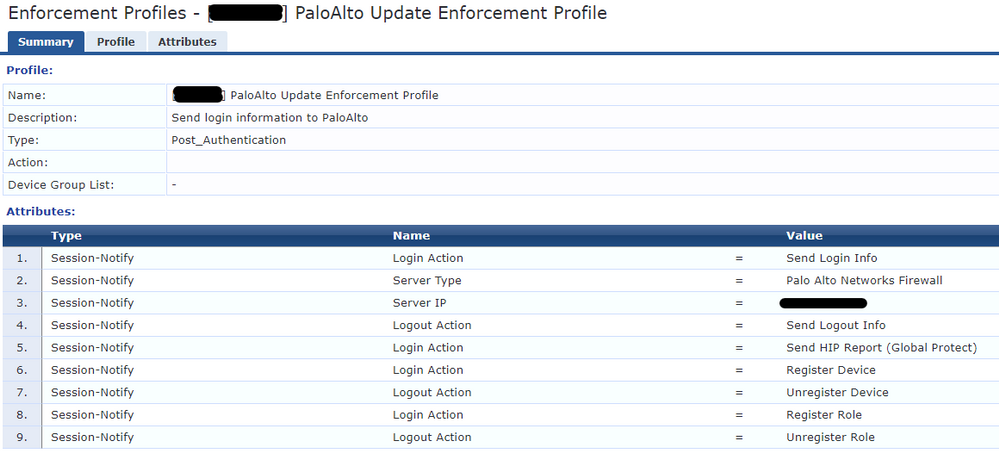
As I mentioned earlier, so far everything works fine, the user is sent to Palo Alto perfectly. Below is the information for the Mac Authentication service,
MAC-AUTH SERVICE
For the Mac-Authentication Service I send only two Enforcement Profiles, the first sends Aruba-User-Role to the Aruba controller and replace the default RADIUS-IETF Username (mac-address) with the Endpoint Username that was entered by the previous service, and last sends updates to Palo Alto.
1. “Aruba-User-Role + Change Radius:IETF::Username”
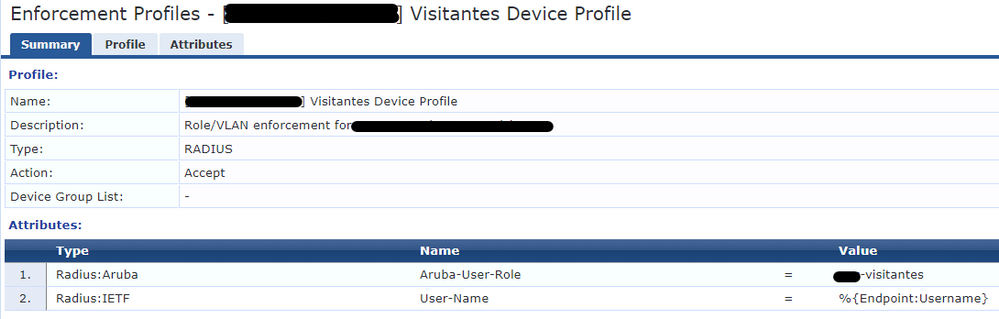
2. “Send Palo Alto Update”
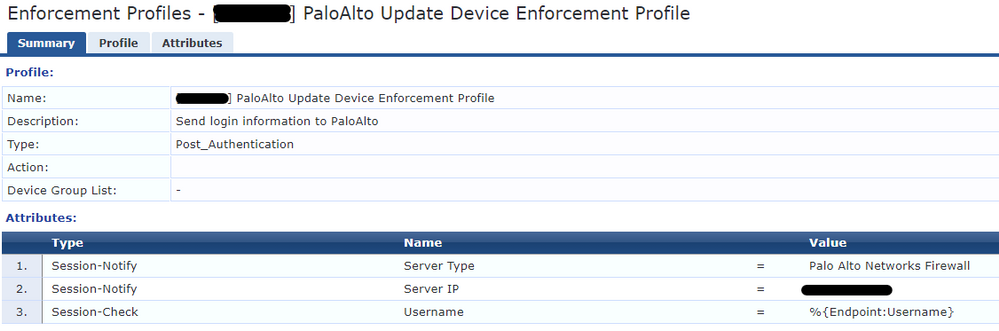
In the Access Tracker on the Output tab, the result of this Enforcement Profile is the image below,
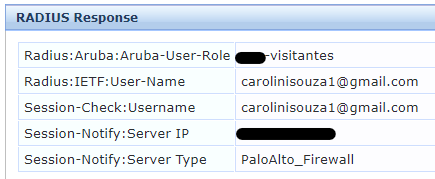
_____________________
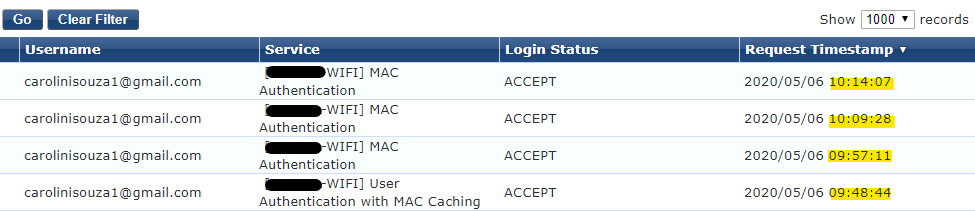
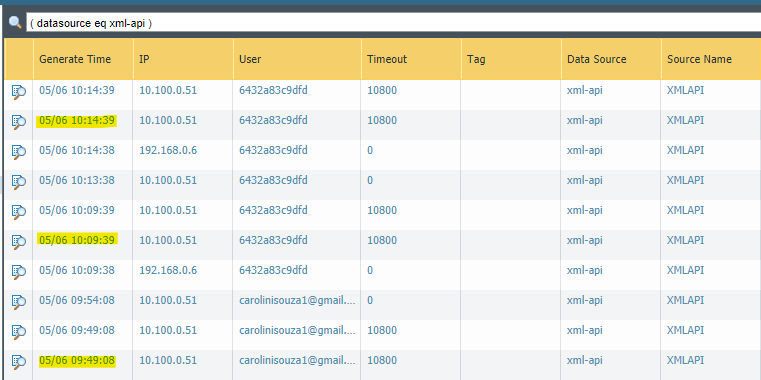
I ran some tests this morning and we can see the Access Tracker and Palo Alto User-ID logs match, they are correct, but in the last logs the username should be presented instead of the mac-address.
ACCESS TRACKER
PALO ALTO USER-ID
Thanks,