Hi alexsuoy,
Its probably not the right thread, but I didn't have any issues with having a $ in the end of the username.
I could also only find permitted characters for user/pass when binding clearpass to AD. I was not able to find anything obvious that involved LDAP authorizaiton with AD.
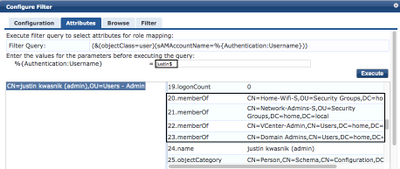
I was able to perform a manual ldap query in the AD server, this worked as expected. I could also see the memberOf info.
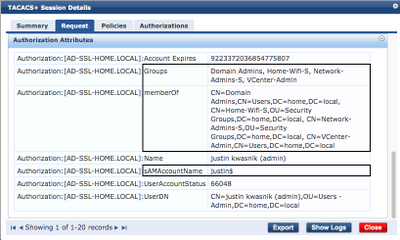
I have also included TACACS Policy Manager authorization info for the same user account.
You may want to check the LDAP servers to ensure they have the correct data and are syncing. Not sure if you are defining them as FQDN / IP / or domain in the address section for the LDAP server.
I would also recommend try a manual query.
Auth Server => Attributes => "Select" Authentication => "Select" Attributes "tab" => Enter Username.