Hi Guys,
I'm having difficulty settings up ClearPass to be used as the Radius Server for my evaluation of Always on VPN. The NPS is set to forward all requests to ClearPass and hopefully receive an allow or deny message back.
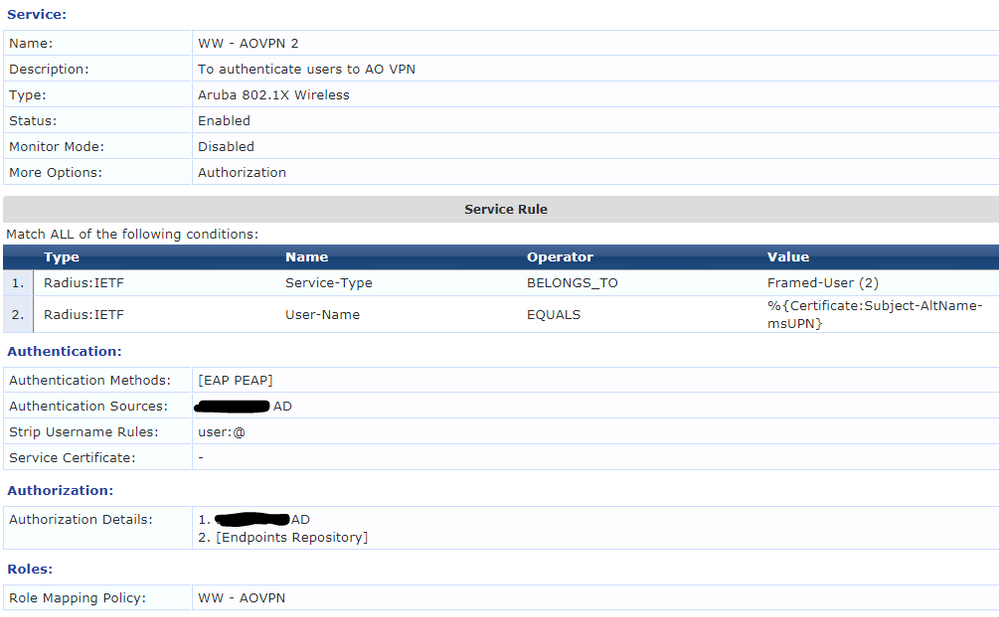
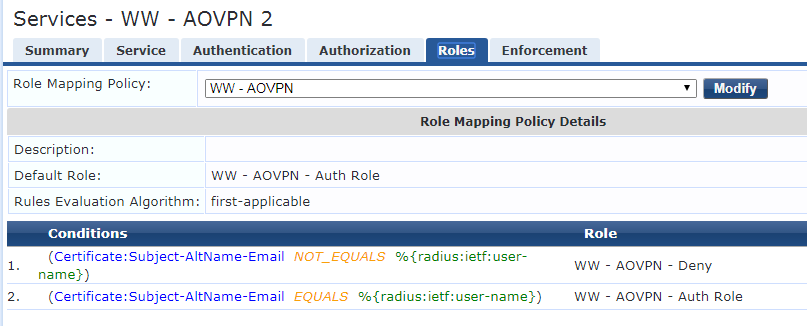
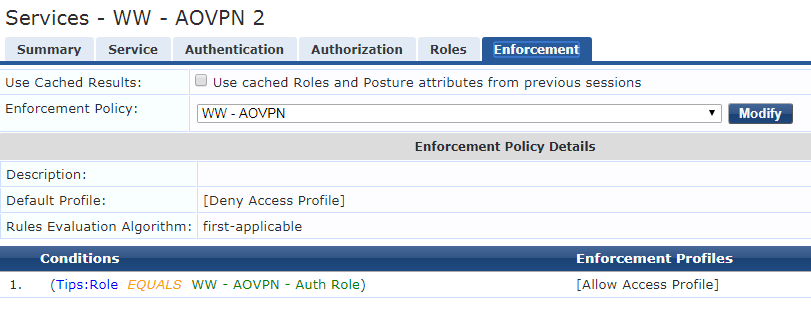
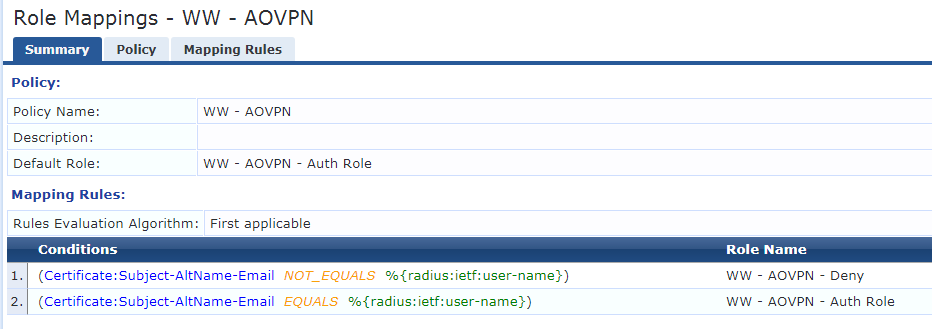
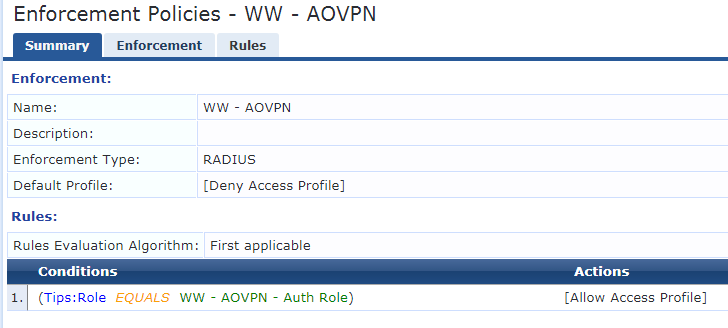
I have set up a service, policy, roles and role mappings (see attachments) however it's not able to classify the login as one thing or another.
Could anyone suggest how I go about this instead?
Wes