Hello.
We have a problem at our company that we can't get our head around.
We have Windows 10 machines with an Active Directory domain. The clients is connecting through cable, so no wireless in this thread. Tunneled-node is enabled and the Win10 clients authenticate via a device certificate that is pushed to every machine. When the authentication comes in, the certificate is compared using CPPM with AD connector and is assigned the appropriate VLAN and role for connectivity. This works perfectly.
The computers also sends its own MAC-adress and this complicates things. In the authentication flow in CPPM we now see double authentication queries, one with the MAC only and one with the correct certificate. Usually, the MAC query is denied since this is not the way we want to authenticate the clients but now to the problem.
We want to enable a Quarantine network that devices connect to when the certificate is not renewed a.k.a expired because clients have been on vacation with the computer turned off.
The things we have done is that as soon as a client authenticate using its certificate, we save the endpoint in the CPPM database with the tag "Owner: OurCompany" and mark the client as "Known". We can then use these tags as a policy match to authenticate client using only their MAC-adress when the devices have an invalid och non-existing certificate. We then place these "zombie"-devices in the quarantine network that enabled strict access only to the AD and PKI infrastructure to renew their certificate. This also works as it should when a certificate is invalid.
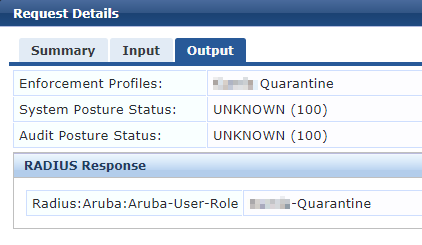
The problem with this is when a device have a working certificate. Now we get double successful authentications that puts the MAC-request in the quarantine VLAN (since the MAC is marked as our device and marked as "known") AND in their correct VLAN (since the device is prompting a correct certificate).
We have seen that the request for the MAC can reach the CPPM before the certificate request and vice versa, so it seems like a random outcome. Some client get the right VLAN and some clients is in quarantine.
Do you folks have a solution to this in any way?
Both authentications is showed in the picture below: 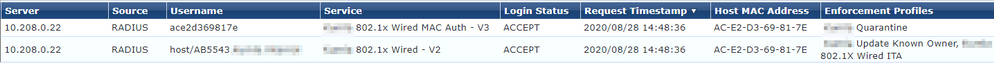
The authentication result for the "802.1x Wired - V2" authentication is showed here:
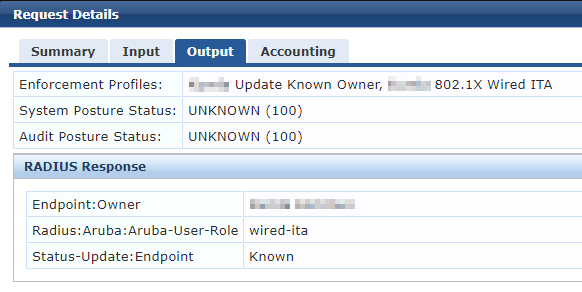
The authentication result for the "802.1x Wired MAC Auth - V3" authentication is showed here: