Let me try to explain this further:
Configuring a Captive portal in a layer2 deployment
Captive portal is a layer3 authenticaton method. In order to make it work in a layer 2 deployment environment, we need to make sure the controller has layer3 reachability to the client. This can be archieved in 2 ways:
1. Configure an IP address on the client vlan(this is not a layer2 deployment. However, since this IP is not the client default gateway, the packet is still pass through the controller. It still layer2 from datapath perspective) When the controller sends out the syn-ack, it knows that the client is reachable locally and will do ARP and sent out the packet.
2. Enable ‘firewall allow-tri-session’ command. Please check the example below:
Topology:
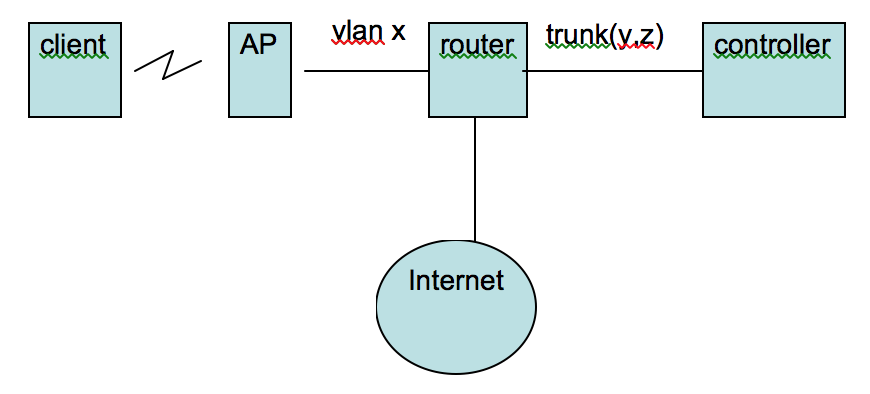
The client is on vlan y. The controller doesn’t have an IP address for vlan y interface. The controller has an IP address on vlan z and it’s the vlan that will do routing between controller and router.
Without the ‘firewall allow-tri-session’ command:
1. Client does a DNS lookup and resolves the IP.
2. The client send out the SYN packet to the resolved IP. The packet reaches the controller through GRE tunnel. The controller will reply with ‘SYN-ACK’ on behalf of the real destination. Since the controller doesn’t have an IP on the client vlan, the controller will do route lookup and send out the packet to the router on vlan z.
3. On the router, it has both the client vlan y and controller vlan z, so the router will do a route lookup, find the client is on it’s local vlan y, then it will ARP. The ARP reaches the controller, the controller sends it to the client (since it’s a bcast). Then, the client replies and the controller sends it back to the router. The router will know in order to reach the client, the packet should be sent to the controller but on vlan y.
4. The controller receives the packet. Since the controller doesn’t allow the tri-session (because the controller will only allow session to be initiated by the user not from the internet), it will drop the packet.
Here’s the example of the ‘show datapath session table ‘ output:
10.168.121.207 is the client IP address. 4.2.2.2 is the dns server IP. 10.168.15.20 is the switchip
(c1-10) #show datapath session table 10.168.121.207
Datapath Session Table Entries
------------------------------
Flags: F - fast age, S - src NAT, N - dest NAT
D - deny, R - redirect, Y - no syn
H - high prio, P - set prio, T - set ToS
C - client, M - mirror, V - VOIP
Source IP Destination IP Prot SPort DPort Cntr Prio ToS Age Destination Flags
-------------- -------------- ---- ----- ----- ---- ---- --- --- ----------- -----
10.168.121.207 4.2.2.2 17 1096 53 0 0 0 1 tunnel 9 FC
66.199.187.182 10.168.121.207 6 80 2168 0 0 0 0 3/0 FDC
4.2.2.2 10.168.121.207 17 53 1096 0 0 0 1 tunnel 9 F
10.168.15.20 10.168.121.207 6 8080 2168 0 0 0 1 tunnel 9 S
10.168.121.207 66.199.187.182 6 2168 80 0 0 0 0 tunnel 9 NYC
With the ‘firewall allow-tri-session’ command enabled
The difference is once the controller receives the packet from the router, it will allow the packet to be sent to the client.
Here’s the show datapath session table’ output:
(c1-10) (config) #show datapath session table 10.168.121.207
Datapath Session Table Entries
------------------------------
Flags: F - fast age, S - src NAT, N - dest NAT
D - deny, R - redirect, Y - no syn
H - high prio, P - set prio, T - set ToS
C - client, M - mirror, V - VOIP
Source IP Destination IP Prot SPort DPort Cntr Prio ToS Age Destination Flags
-------------- -------------- ---- ----- ----- ---- ---- --- --- ----------- -----
207.17.137.229 10.168.121.207 6 80 2177 0 0 0 1 local F
10.168.121.207 10.168.15.20 6 2177 8080 0 0 0 1 local FY
10.168.121.207 10.168.15.20 6 2178 443 0 0 0 1 tunnel 9 FNC
10.168.121.207 4.2.2.2 17 1096 53 0 0 0 1 tunnel 9 FC
4.2.2.2 10.168.121.207 17 53 1096 0 0 0 1 tunnel 9 F
10.168.15.20 10.168.121.207 6 443 2178 0 0 0 1 tunnel 9 FS
10.168.15.20 10.168.121.207 6 8080 2171 0 0 0 0 local FDYC
10.168.15.20 10.168.121.207 6 8080 2177 0 0 0 1 tunnel 9 FS
10.168.121.207 207.17.137.229 6 2177 80 0 0 0 1 tunnel 9 FNC