Hi,
Let's start give u some details | and try to assist you. :smileyhappy:
*Splittunnel mode - it's a good option when deploying an RAP in order to give the clients the ability to go out locally for different services = src-nat in the fw rules.
*bridge mode - it's a good option when deploying a RAP and you would like to give clients access to local resources in the branch location without passing the traffic trough the controller at all . (if it's for guest network...you will not be able to do captive portal on bridge mode - because it's l3 auth..And in bridge mode all client traffic doesn't arriving to the tunnel or the controller itself at all)
*use just the PEFNG you don't need PEFV installed also in order to enable RAP support* (if using AOS 5.X or above)
The rap whitelist is only for RAP units (RAP2/3/5/108/109) - if you would like to use cert auth to the ap..u can > u need to enable control plane security ,and allow this AP-105 to connect to the controller.
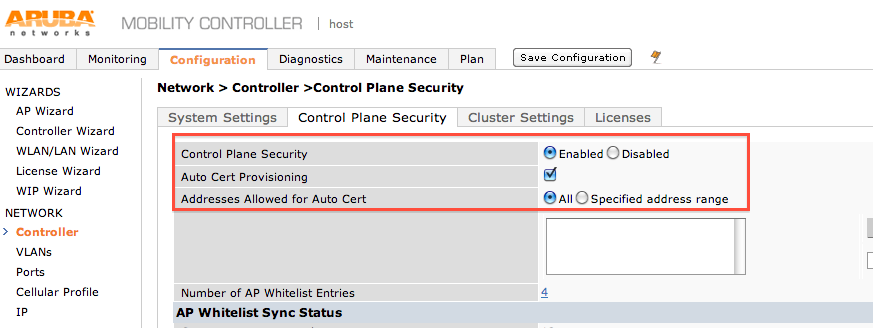
The other method is user+pass+secret. (all u need to know is screenshots and explained in rest of the post)
:smileyindifferent: Lets see if u configured everything right on your controller?
configuration>vpn services.
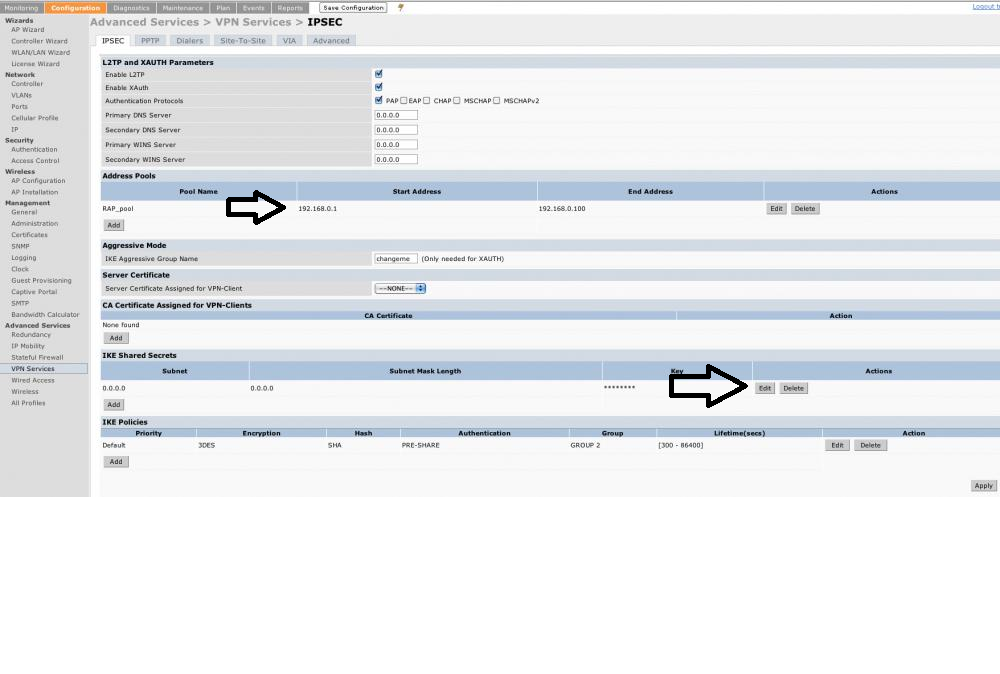
did u created an address pool for the raps?
Did u created a secret?
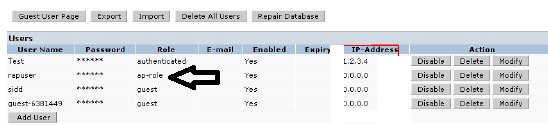
configuration>AAA>internal db
did u created a user for the rap unit with an ap-role?
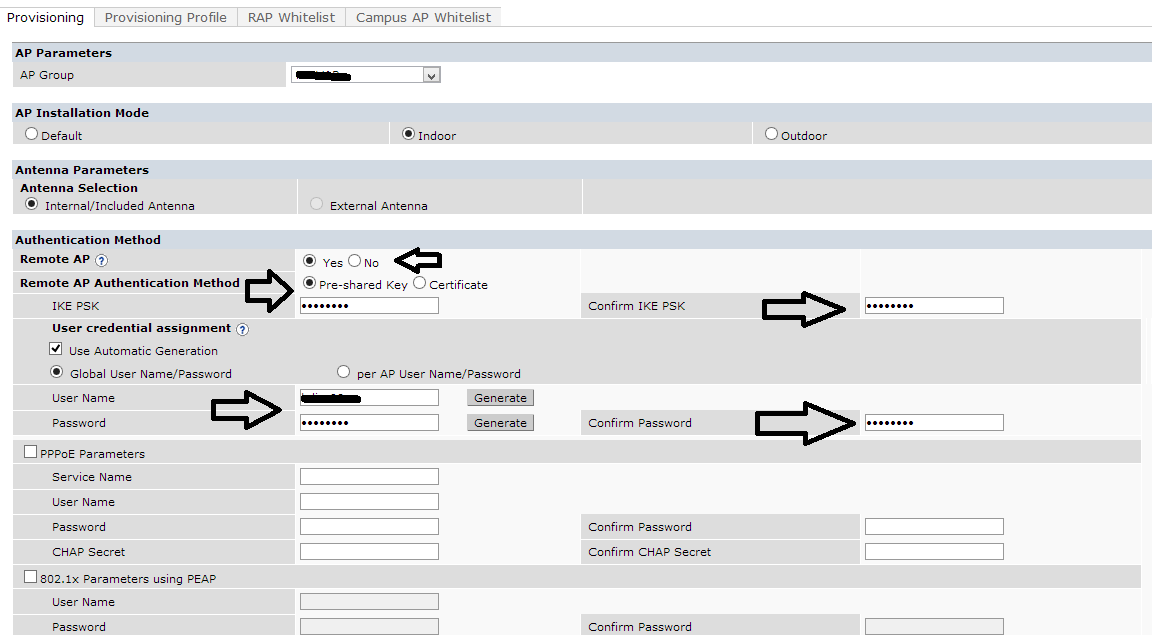
configuration>ap installation
when u provisioned the rap unit in front of the controller - did u entered the external IP of the controller (the vlan IP address of the controller)
did u mark the ap to be a Remote ap ,and also entered the secret + user + password?
please do print screens of your vpn services page | internal db page | ap providing page of the specific rap you are trying to connect.
*don't forget to press apply on any needed page on the GUI + save configuration in the end.
here is the two ports that should be open/forwarded:

update me if it's helped .