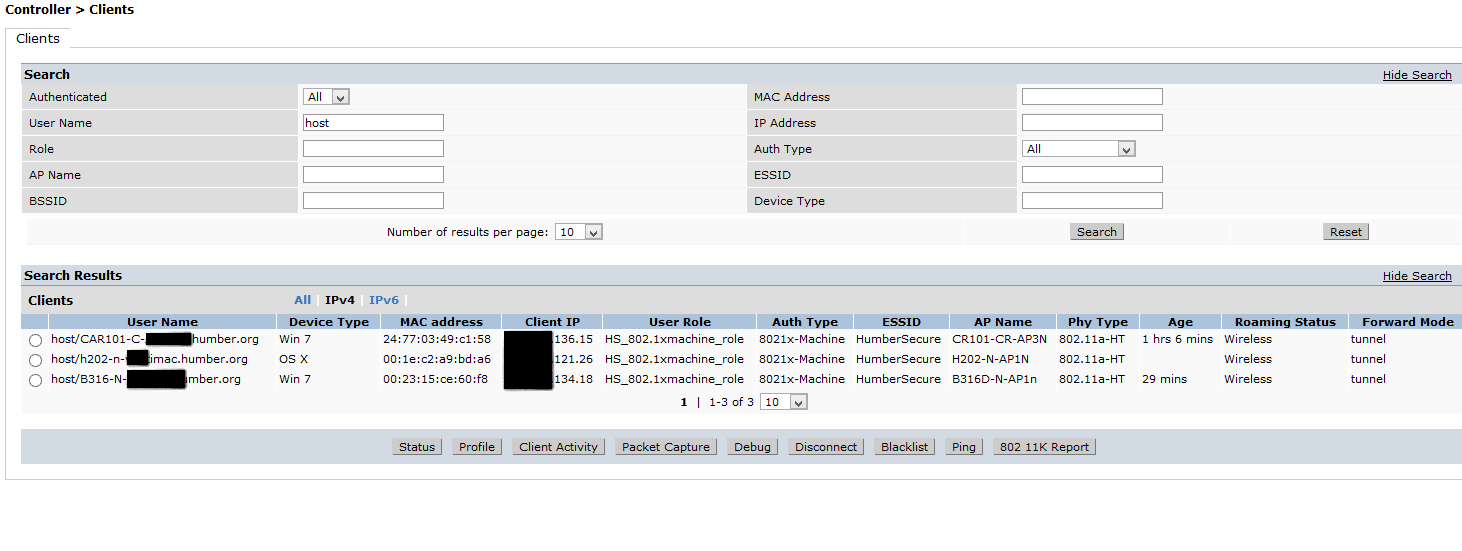
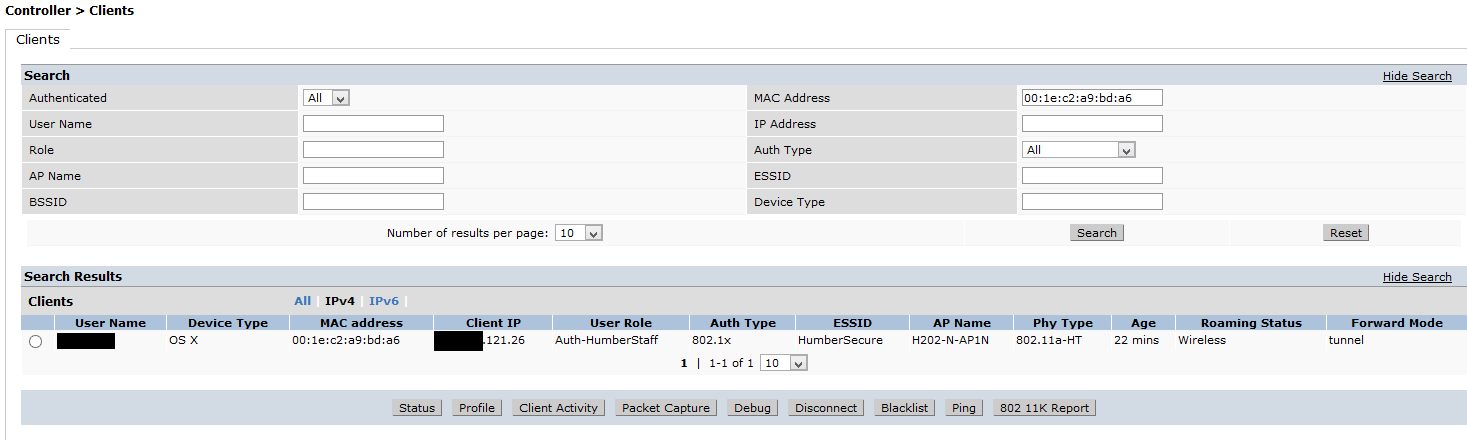
We created 2 profiles with Profile manager one for joining to the domain ( and other stuff our Mac administrator wants to have on the Mac) and a second one for WIFI. We also have a small Bash script that is needed to fix Macs bad formatting of the machine user name and password.
Once the DeployStudio is done imaging the Computer, the script is run.
- First the Domain .mobileconfig is installed.
- Get the machine creds from the Keychain ( under the Active Directory section )
- Put the machine creds into the second WIFI .mobileconfig
- install the WIFI .mobileconfig
Delete the profiles form the computer ( security reason on this one)
Done!