@thecompnerd wrote:
If the licensing client can continue to operate when the master licensing server is down, does that just mean it will maintain the current set of licenses it has checked out, but will be unable to check out additional licenses until the master license server is back up? If so, I think I can deal with that.
If I were to go with an all masters configuration, how does one master get its licensing information from another master designated as the primary license server? The 6.3UG isn't too clear on the configuration. It just says all the masters need connectivity to the same Airwave server.
Thecompnerd,
You need to break this down into multiple problems and prioritize based on importance.
1. You need to have a remote AP controller across DMZs
2. You need to have guest controllers across DMZs
3. You need to leverage centralized licensing
All three issues are complicated by themselves. You should not combine them.
1. Having remote APs across two different DMZs is not difficult in itself unless you are relying on seamless failover when one controller fails. You could point your RAPs DNS with multiple a-records so that it will try one ip address then another. The gotcha is that wired devices behind the RAP will probably not re-ip if the AP rebootstraps quickly, because they might not see the ethernet go down. Ensuring that devices that are wired re-ip is an advanced topic that might require something like OSPF between controllers if you intend on maintaining ip addresses. That could be really involved based on your infrastructure and your comfort with advertising OSPF to your internal network to provide reachability to your RAP clients
2. Having guest controllers across two different DMZs is really involved due to state issues because guests will not know that the network routing their traffic has shifted to another controller and another DMZ. This would require a combination of OSPF to shift the default gateway to another controller and the GRE tunnel group feature in 6.3 http://www.arubanetworks.com/techdocs/ArubaOS_63_Web_Help/Web_Help_Index.htm#ArubaFrameStyles/Network_Parameters/Configuring_GRE_Tunnel_Group.htm to provide redundancy for a GRE tunnel between two different controllers.
3. With regards to licensing, you can have the topologies pictured below. You can have every controller as a master pointing back to the centralized master, however. You can also have locals of the centralized master involved in the scheme. About the only topology not supported with centralized licensing is the locals of multiple masters:
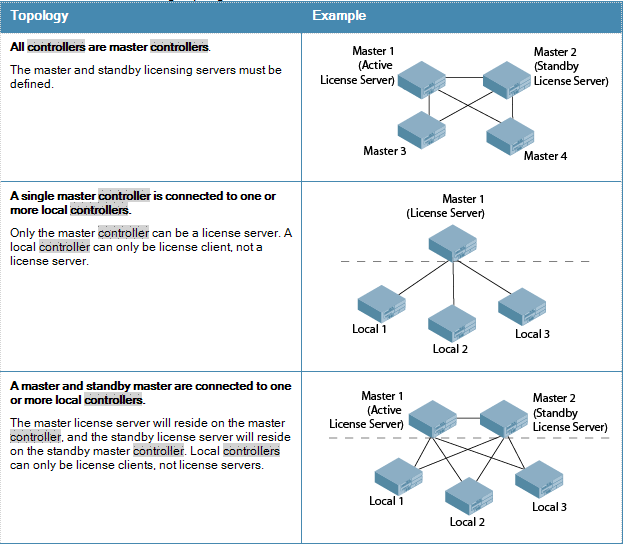
Long story short, you should probably get professional advice to put a complicated solution like this into play, because they will have detailed information about your network that would result in a dealbreaker otherwise. There is no reason why you have to reuse the same controllers for DMZ and RAP: that will certainly complicate things more.