Hello everyone i though in making a guide in which will tell you how to configure EAP TLS authentication for your WLAN... i just see manuals but with EAP PEAP but non with EAP TLS(The NPS Part)
Anyways
This manual assumes that:
1-You already got an Active directory working
2-You already installed NPS role on a server
3-You already got PKI infraestructure
First open your NPS and click on NPS local and on the right side pick radius server for 802.1x and then click on configure 802.1x
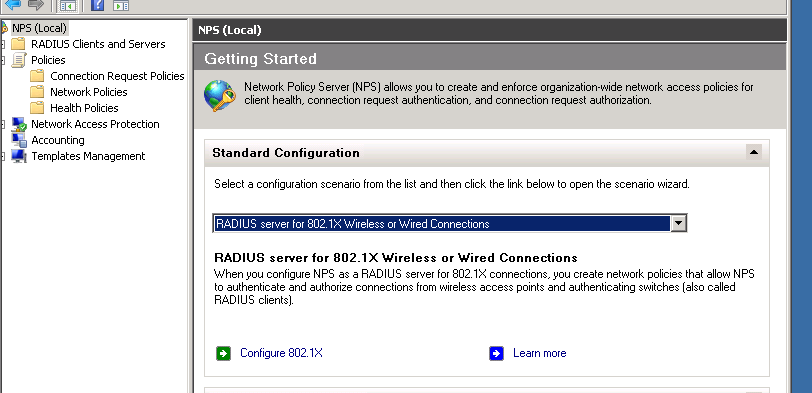
After that click on secure wireless connection
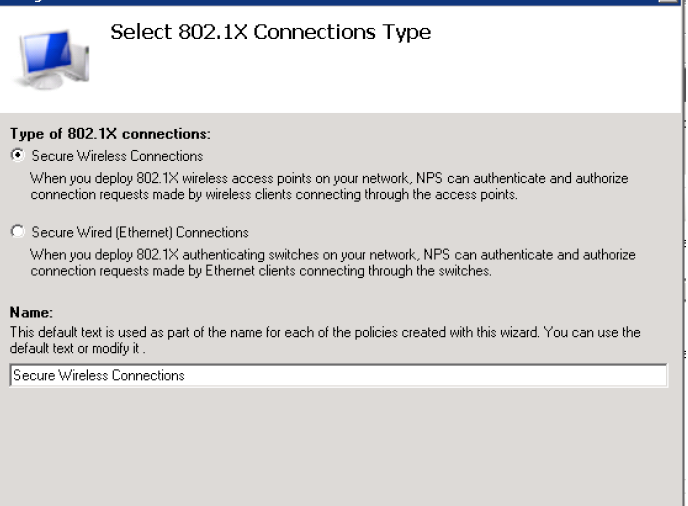
Enter the new radius client which will be the ip address of your controller, and put a preshare key that it will be used to communicate between the NPS and the radius client(your controller
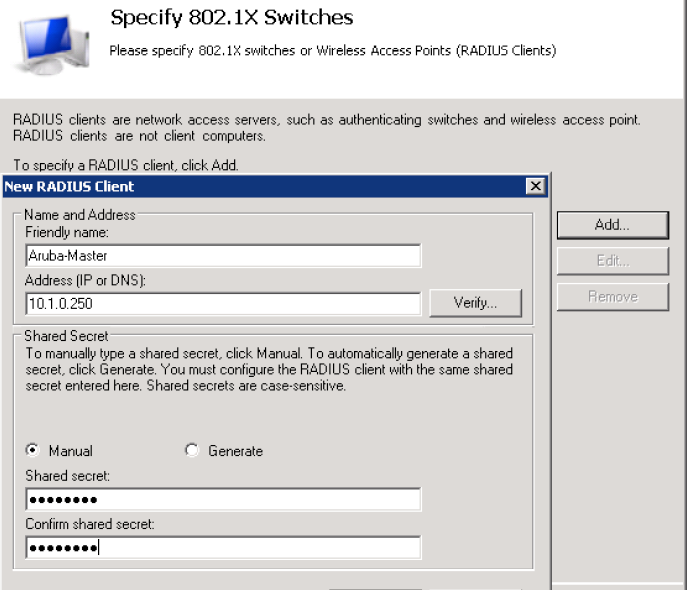
Select microsoft smart card or certificate and click on configure... and inside of it put the certificate that you created for the server(in this case you should have request a certificate from this server using the mmc)
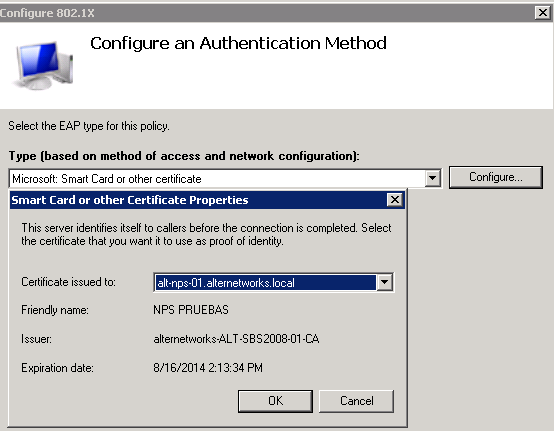
Click next next finish
Now here comes the tricky part...
You need to open the Network policy that you just created and go to settings in inside there click add and add a value for framed MTU and put this value in it 1344 like this
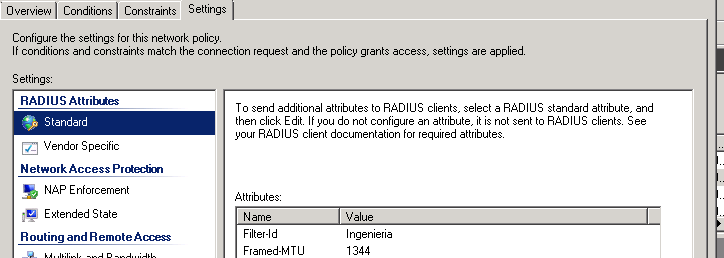
And well click OK
And now you are done the server part.... after this you should be able to use EAP TLS
The last part of the Framed MTU is something you need because in some cases, switches, routers or firewalls drop packets because they are configured to discard packets that require fragmentation. And if you dont configure this it will drop it and you will see it will not work... so just configure it! so that way the EAP payloads maximum size is reduced.
If there something that was not clear let me know and ill modify this tutorial.
If you want me to add something else maybe how to configure the Clients? how to configure the controller part let me know and i ll add it. I just considered to show you guys how to configure the NPS part because actually that last part of the framed MTU is the tricky part... people just dont know and they will think it just doesnt work but well you missing that.
Hope it help you all
Cheers
Carlos
[Mod note: edited subject line for readability]