Hi,
If you don't terminate on the controller, you don't need to configure any thing on the controller because traffic is not visible to the controller (it will pass trough the controller ) that is the primary objective of creating secure tunnel between Client and the controller.
Coming to the config at client and the server side,
Client :
Step 1 :
Open the WL client connection profile and select "Security " tab and select the EAP type as shown in the pic.
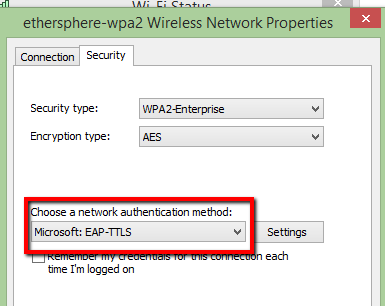
Step 2 :
Click on settings and select "user Authentication Methods" as "EAP-MSCHAP V2" as shown in the pic

In the server, I have snapshots for IAS, should be same for NPS as well.
Select remote access policy-->edit profile-->Authentication-->EAP methods as shown in the pic.

Try and let me know if you need any further help on this.