NOTE: Using TACACS+ for management AAA is always recommended.
Working recently on a customer deployment I realized that there is little up-to-date content on the integration of ArubaOS with Microsoft NPS as a RADIUS Server. This is not meant as a full step-by-step guide, but should provide some of the most important details of the configuration.
While there are a ton of benefits of leveraging Aruba ClearPass for authentication including admin access for network devices, many customers rely on NPS for their admin access control as it is included with Windows Server and already integrated with Active Directory.
The example in this post shows some of the basic settings required when configuring admin authentication of ArubaOS with NPS.
Variations of the examples provided should allow you to create more detailed NPS policies according to your needs. This setup has been created with ArubaOS 8 but the underlying procedure applies to earlier versions of ArubaOS as well.
The NPS configurations could also be adapted to provided user authentication for 802.1x.
In this example we will be creating two NPS policies to apply two different admin privileges (root and read-only) based on the AD group memberships of a user.
Helpful Reading
Use Regular Expressions in NPS
NPS Step-by-Step Installation by mizitechinfo
ArubaOS 8.2 Web Manual - Management Access
NPS Configuration
The configuration steps below have been executed on a Windows Server 2012 R2. The steps should be fairly similar on other versions of Windows. The server has the NAP role already installed. If you need help installing NAP, check out the post linked above.
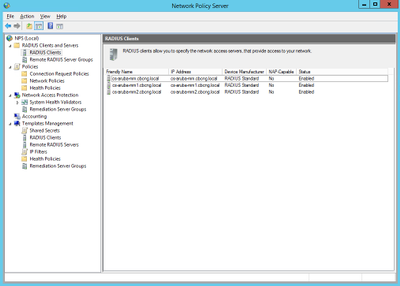
As in ClearPass, I always create the allowed Network Access Devices (NAD) first.
1) Right-click on Network Policy Server > RADIUS Clients > New
2) Add your NAD (an ArubaOS 8 Mobility Master in my case) either by IP or Hostname. If you are using the FQDN, make sure your server is able to resolve it. You can test this by clicking on 'Verify'.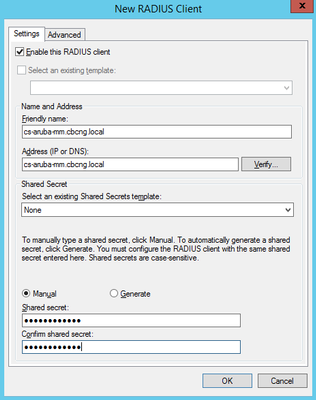
Make sure your new Radius Client is configured as 'RADIUS Standard' under 'Advanced'
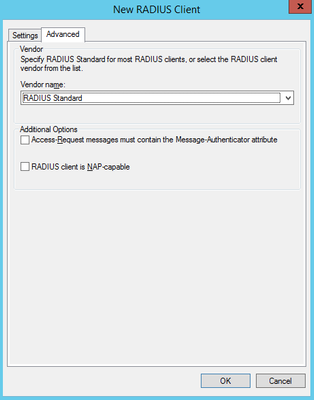
3) Once you added all your RADIUS Clients (and remembered their Shared Secret) we will now create a new Network Policy by right clicking on Policies > Network Policies > New
Give the policy a name and click 'Next'. The first Policy we are going to create is to grant 'read-only' privileges for users logging into the Mobility Master.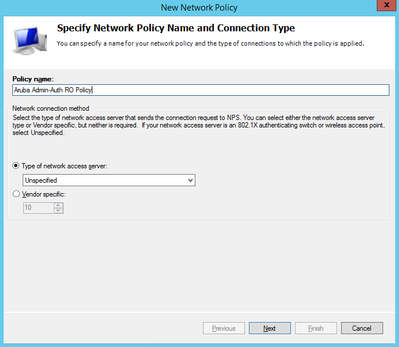
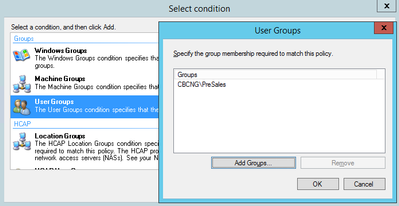
4) In the next step you will be asked to define 'Conditions' under which this policy is applied. If you have worked with ClearPass before, this is similar to the Service Categorization rules. Click on 'Add' and you will see many conditions that you can use to apply to this policy. In my example I will restrict the conditions to the following three:
- Authentication Method
- AD User Group
- NAS IPv4 Address
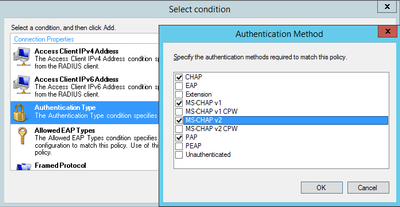
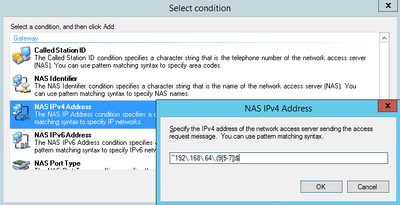
For the NAS IPv4 Address, NPS supports Regex syntax. If you are not too knowledgable on the subject, check out the link I posted above. In addition here is one example of an online regex validator: https://regex101.com/
There are many others out there, just Google your favorite.
In the above example, I am restricting the policy to NAS IP Addresses 192.168.65.95 - 97.
5) On 'Specify Access Permission' select 'Access granted':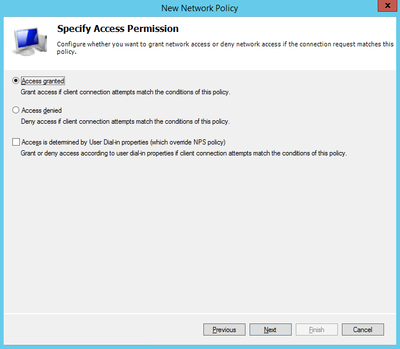
Select your desired authentication methods in the next screen and hit 'Next'. You can skip the Constraints unless you would like to configure any of them.
6) On the 'Configure Settings' screen select Radius Attributes > Vendor-specific > Add.
<Begin side-trip>
As any enterprise network vendor, Aruba has a broad range of vendor-specifc radius attributes (VSA). To get an overview of the available attributes, logon to your Aruba Mobility Master or Controller through console/SSH and issue the following command:
show aaa radius-attributes | include Aruba,Value
This will provide you with a list of supported attributes, their value, type and - probably most importantly - the Aruva VSA Id:
Attribute Value Type Vendor Id
Aruba-Mdps-Device-Version 21 String Aruba 14823
Aruba-Mdps-Max-Devices 18 Integer Aruba 14823
Aruba-Location-Id 6 String Aruba 14823
Aruba-Template-User 8 String Aruba 14823
Aruba-No-DHCP-Fingerprint 14 Integer Aruba 14823
Aruba-AirGroup-Device-Type 27 Integer Aruba 14823
Aruba-Mdps-Device-Profile 33 String Aruba 14823
Aruba-Port-Bounce-Host 40 Integer Aruba 14823
Aruba-Mdps-Device-Udid 15 String Aruba 14823
Aruba-AirGroup-Shared-User 25 String Aruba 14823
Aruba-Mdps-Device-Serial 22 String Aruba 14823
Aruba-AirGroup-Shared-Group 35 String Aruba 14823
Aruba-AP-IP-Address 34 IP Addr Aruba 14823
Aruba-Auth-Survivability 28 String Aruba 14823
Aruba-User-Role 1 String Aruba 14823
Aruba-Auth-SurvMethod 39 Integer Aruba 14823
Aruba-Admin-Path 42 String Aruba 14823
Aruba-Network-SSO-Token 37 String Aruba 14823
Aruba-Port-Id 7 String Aruba 14823
Aruba-Priv-Admin-User 3 Integer Aruba 14823
Aruba-Mdps-Device-Product 20 String Aruba 14823
Aruba-User-Group 36 String Aruba 14823
Aruba-WorkSpace-App-Name 31 String Aruba 14823
Aruba-AS-Credential-Hash 30 String Aruba 14823
Aruba-User-Vlan 2 Integer Aruba 14823
Aruba-AirGroup-Version 38 Integer Aruba 14823
Aruba-AirGroup-Shared-Role 26 String Aruba 14823
Aruba-Device-Type 12 String Aruba 14823
Aruba-Mdps-Device-Imei 16 String Aruba 14823
Aruba-Essid-Name 5 String Aruba 14823
Aruba-AP-Group 10 String Aruba 14823
Aruba-AS-User-Name 29 String Aruba 14823
Aruba-CPPM-Role 23 String Aruba 14823
Aruba-Mdps-Device-Name 19 String Aruba 14823
Aruba-Calea-Server-Ip 41 IP Addr Aruba 14823
Aruba-Mdps-Provisioning-Settings 32 String Aruba 14823
Aruba-AirGroup-User-Name 24 String Aruba 14823
Aruba-Mdps-Device-Iccid 17 String Aruba 14823
Aruba-Framed-IPv6-Address 11 String Aruba 14823
Aruba-Named-User-Vlan 9 String Aruba 14823
Aruba-Admin-Role 4 String Aruba 14823
We are interested in the last attribute in that list, which is the Aruba-Admin-Role. This attribute allows you to set the admin roles like 'root', 'read-only', 'network-operations' etc. directly.
<end side-trip>
On the 'Add Vendor Specific Attribute' screen, double-click the last entry under Attributes:
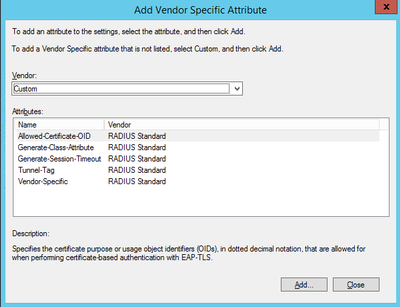
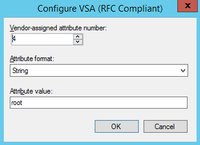
7) Add the VSA attribute information we fetched from ArubaOS:
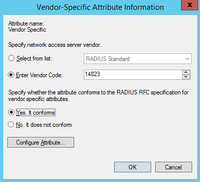
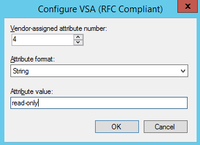
Make sure you checked the spelling. The last screen of the wizard will allow you to review all the settings configured for your policy.
In order to grant 'root' privileges to users, we will simply repeat steps 1 through 6 but use a different string for the VSA in step 7)
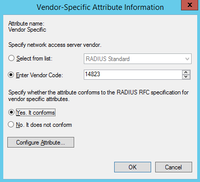
Upon completion of the wizards you will have two Network Policies configured on your NPS Server: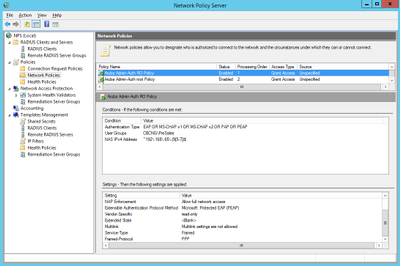
ArubaOS Configuration
Once you have completed your NPS configuration you can now take the necessary modifications to login to your ArubaOS system using AD credentials.
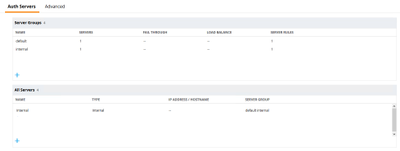
1) Login to your ArubaOS Mobility Master/Contorller and navigate to Configuration > Authentication > Auth Servers:
 2) Click on + under All Servers and add your NPS server:
2) Click on + under All Servers and add your NPS server: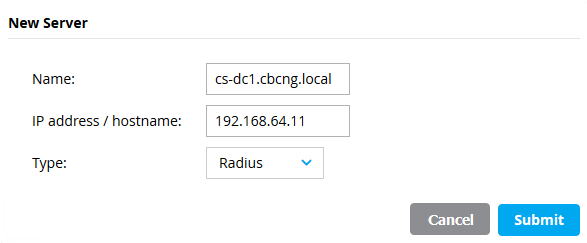
Once you hit 'Submit', make sure to select your newly created server again and configure the Radius Shared Secret that you used on your NPS Radius Client before:
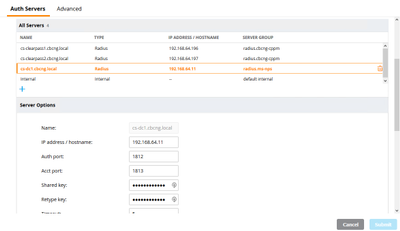
3) Double check your Radius Shared Key :-)
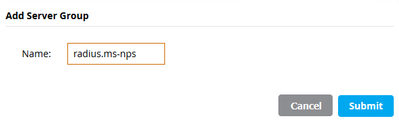
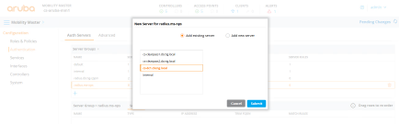
4) Click on + under the Server Groups, enter a name for the group and add your NPS Auth server to it:
5) Navigate to Configuration > System > Admin and expand the section 'Admin Authentication Options'. Select 'Enable' and choose your server group that you previously created.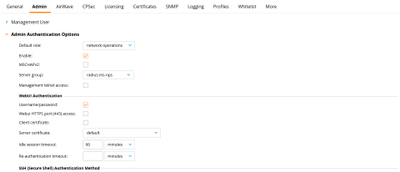
You also have the possiblity to configure the default role here, which is applied in the case where your Authentication server returns a Radius-Accept but does not supply any VSA in the response. If you have not configured any Server-derivation Rules, this role will be applied upon successful authentication.
If you choose a default role here, which is not used in your NPS policies under any circumstances, it is also a good tool to verify immediately, if the Radius response includes the required VSA. If a user is assigned the default role upon authentication, something is wrong in your NPS configuration.
6) Last course of action on ArubaOS 8 is now to commit the pending changes.
You can now try and login using AD supplied credentials to verify your configuration. If anything is not working as expected, I have consolidated a few troubleshooting tips in the next section.
Troubleshooting
A few hints about troubleshooting (unless you get it straight for the first time, then congratulations!). Unfortunately, NPS does not offer anything close to what ClearPass provides with its Access Tracker for Live Monitoring. You need to revert to the Event Viewer. Like with any RADIUS implementation, a few of the most common things that can go wrong:
- Network Access Device (NAD) not listed as an allowed RADIUS Client.
- RADIUS Shared Secret not matching.
- Wrong credentials entered.
- Wrong or no RADIUS VSA returned by NPS
Unfortunately, what the event viewer does not seem to provide is when an authentication request does not match any of the configured Network Policies. If any NPS expert knows how to display those, feel free to add it to this thread.
Some events like a potential Shared Secret or missing Radius Client mismatch can be seen in the Event Viewer of NAP:
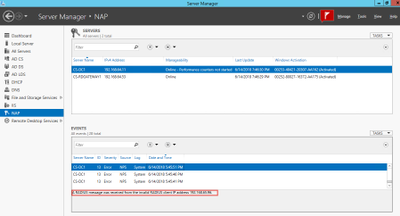
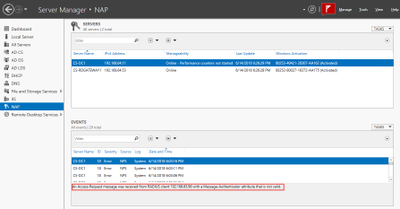
On the ArubaOS side you can validate the role a user has been assigned to by issuing the following command on through CLI:
show loginsessions
Session Table
-------------
ID User Name User Role Connection From Idle Time Session Time Path
-- --------- --------- --------------- --------- ------------ ----
1 admin root 192.168.65.104 00:01:25 00:30:48 /
2 nwadmin read-only 192.168.65.104 00:00:03 00:00:14 /
If you see here the default role here instead of your NPS assigned roles, there is a high probability your policy is not configured correctly.
There are some extended debugging possibilites on ArubaOS:
logging security process authmgr level debugging
logging security subcat aaa level debugging
Upon enabling debuggin on those processes, it will write detailed events into the security log:
show log security 20
<DBUG> |authmgr| Auth GSM: Num dev_id_cache entries aged = 0
<DBUG> |authmgr| RX (sock) message of type 1, len 1032
<DBUG> |authmgr| aal_authenticate: In aal_authenticate
<DBUG> |authmgr| aal_authenticate user:nwadmin vpnflags:0.
<DBUG> |authmgr| unknown user=192.168.65.104, method=Management
<DBUG> |authmgr| aal_authenticate server_group:default.
<DBUG> |authmgr| Select server for method=Management, user=nwadmin, essid=<>, server-group=radius.ms-nps, last_srv <>
<DBUG> |authmgr| server=cs-dc1.cbcng.local, ena=1, ins=1 (1)
<INFO> |authmgr| Selected server cs-dc1.cbcng.local for method=Management; user=nwadmin, essid=<>, domain=<>, server-group=radius.ms-nps
<DBUG> |authmgr| aal_authenticate (1250)(INC) : os_reqs 1, s cs-dc1.cbcng.local type 2 inservice 1 markedD 0
<DBUG> |authmgr| aal_authenticate (1297)(INC) : os_auths 1, s cs-dc1.cbcng.local type 2 inservice 1 markedD 0 sg_name radius.ms-nps
<DBUG> |authmgr| User nwadmin MAC=00:00:00:00:00:00 not found.
<INFO> |authmgr| Administrative User result=Authentication Successful(0), method=Management, username=nwadmin IP=192.168.65.104 auth server=cs-dc1.cbcng.local
<INFO> |authmgr| Authentication result=Authentication Successful(0), method=Management, server=cs-dc1.cbcng.local, user=192.168.65.104
<DBUG> |authmgr| server_cbh (257)(DEC) : os_reqs 0, s cs-dc1.cbcng.local type 2 inservice 1 markedD 0
<DBUG> |authmgr| server_cbh(): response=0 from Auth server 'cs-dc1.cbcng.local for client:9 proto:1 eap-type:0'.
<DBUG> |authmgr| server_cbh (657)(DEC) : os_auths 0, s cs-dc1.cbcng.local type 2 inservice 1 markedD 0 sg_name radius.ms-nps
<NOTI> |authmgr| Administrative user 'nwadmin' authenticated successfully (role=read-only, privileged=0)
<DBUG> |aaa| mgmt-auth: nwadmin, success, read-only, 0
<NOTI> |aaa| Authentication Succeeded for User nwadmin, Logged in from 192.168.65.104 port 56996, Connecting to 192.168.65.96 port 4343 connection type HTTPS
Once you are done troubleshooting, you should disable the logging again.
That's all I wanted to share about ArubaOS Admin Authentication and NPS. Questions / comments always welcome.