The following steps are to be followed.
1: Configure the controllers to use TACACS service for management user authentication.
2: Create a new TACACS based service to handle TACACS request from the controller
3: Add the Aruba controller as a NAD device.
Here are configuration commands to enable TACACS authentication, authorization and accounting on the Aruba Controller. The controllers do not support per command authorization, but will support the pre-defined roles in the controller.
The pre-defined roles for the controllers are:
- root - super user role
- guest-provisioning - guest provisioning role
- network-operations - Network operator role
- read-only - Read only role
- location-api-mgmt - Location API Management Role
aaa authentication-server tacacs <My_Tacacs_Server>
host <TACACS_SERVER_IP>
key <PRESHARE_KEY>
session-authorization
!
aaa server-group <TACACS-SERVER-GRP>
auth-server <My_Tacacs_Server>
!
aaa tacacs-accounting server-group <TACACS-SERVER-GRP> mode enable command [all|action|configuration|show]
aaa authentication mgmt
server-group <TACACS-SERVER-GRP>
enable
!
Below are the steps to Configure the Tacacs service on CPPM to authenticate Aruba Controller's management users.

Select the following details:
Type : TACACS + Enforcement
Name : This will be the name of the service.
Description : Add a note to it for user's understanding.
Make sure that Authorization option is checked. This is used for role based authentication.
Add a rule as shown above : it means that any connection with NAD-IP beginning with 10.30.156 and using TACACS protocol should hit this service.
The Second Service rule is added to make the Service more robust so that any client authentications coming from this NAD are not treated as TACACS.
Click "Next"
On this screen add Active directory as Authentication source and hit "Next"

Make sure that Active directory is added as an authentication source under this and hit "Next".
On this page click on "Add new Role Mapping Policy", this will open a new window as below.
On this page, we can select Default Role a Read Only Role. Click "Next".

On this window, we will add Roles for authorization.

The rule above means : If user is a member of a given group then he will authenticate with "TACACS network Admin" Role.
Similarly we can add new rules based on our requirements as below making sure that below option is set.
|
Rules Evaluation Algorithm:
|
First applicable
|
Once all the rules are configured, click on save and the screen comes back to the configuration of service. Select the role which we created now.

Once all the rules are configured, click on "Save" and the screen comes back to the configuration of service. Select the role which we created now.

Now if required, we can add the Enforcement profile.
Select the default profile " [Admin Network Login Policy]" from the drop down.
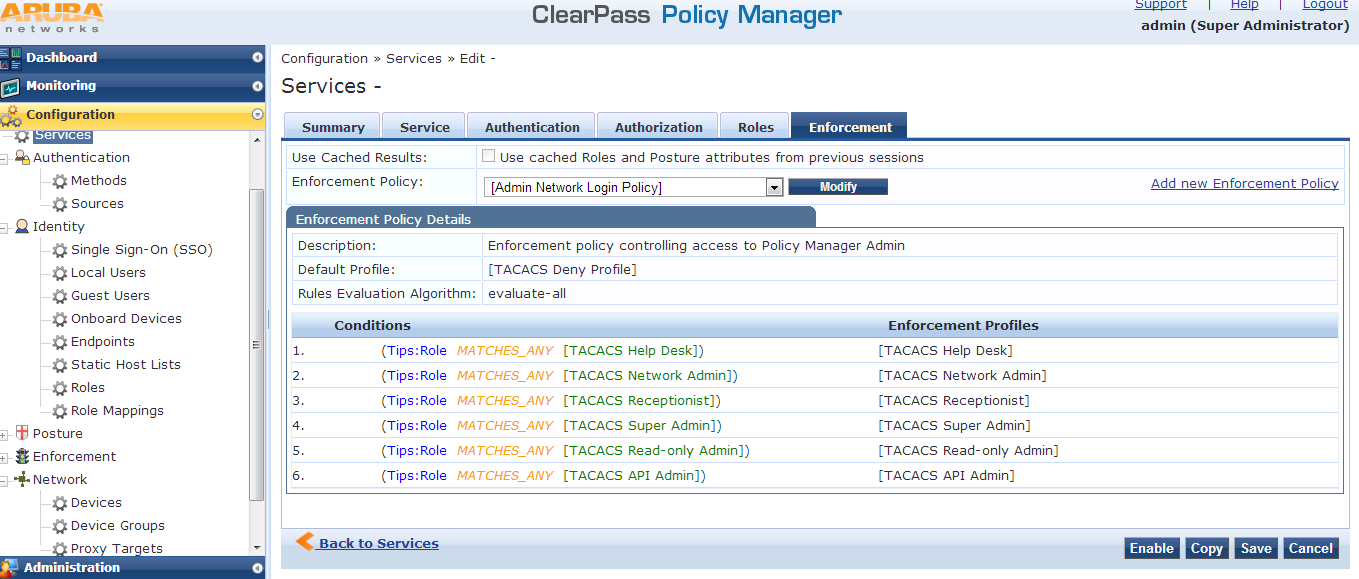
Save the configuration.
3 : Add the device to CPPM.
Navigate to Configuration » Network » Devices and click on "Add Device"

Name: A generic name for user's understanding
IP or Subnet Address: IP or Subnet of the device
TACACS+ Shared secret: Should match with what we have configured on the Switch.
Hit "Save" and exit.
Once done, please logout and login with a remote user ( user which exists on AD) and verify.