When we use post auth session limit enforcement profile to limit user authentications based on session limit, users will be allowed to authenticate. However post auth check executed periodically will perform the session limit checks and initiate disconnect (Radius CoA) for client devices which are more than the configured session limit.
In this case, the same disconnected client can connect back even after disconnect, which will be disconnected during next periodic post auth check.
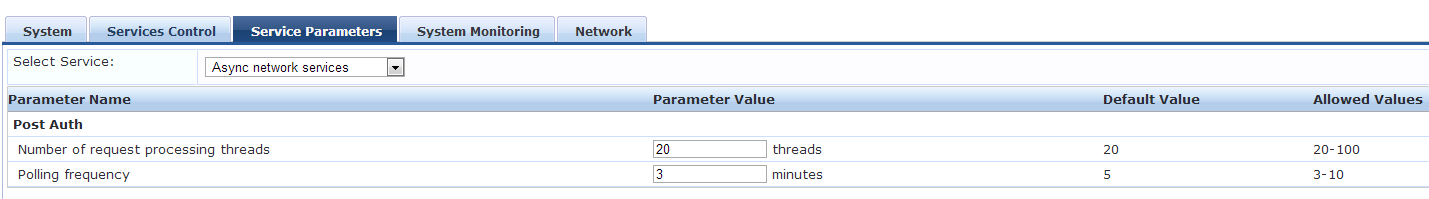
By default post auth check performed every 5 minutes, this can be modified from Administration->Server Manager->Server Configuration->Service Parameters->Async Network Services->Polling Frequency (allowed values are 3-10 minutes).
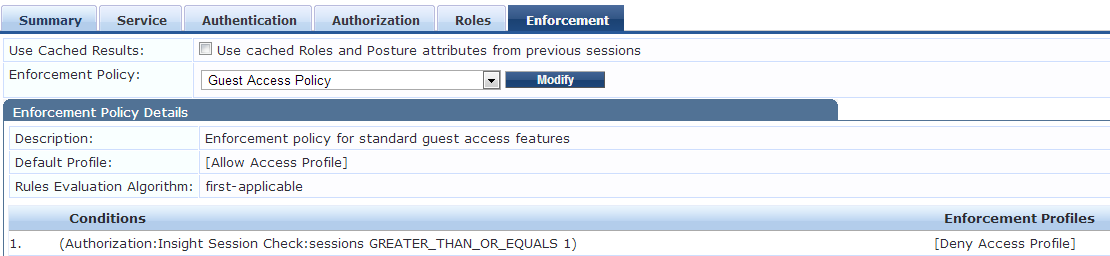
However, if we want to reject user authentications based on session limit, we can use Insight DB as authorization source with custom SQL query to retrieve the active sessions count, then we can define enforcement policy rule to reject access if the user has already reached session limit.
For example:
We can use the below SQL query to check the session count and create a Insight DB as authorization source:
select count(*) as sessions from radius_acct where (username = '%{Authentication:Username}') AND end_time is null AND termination_cause is null AND (updated_at BETWEEN (now() - interval '1 hour') AND now());

We can modify the Enforcement policy and add a first rule to check the session count and deny access based on session count.