Problem:Clients connected on native vlan of mesh link are unable to get an IP address.
DHCP (vlan 100,vlan 350)<----Switch1======Trunk======IAP Mesh Portal ==========IAP Mesh Point====Trunk====Switch2 --->Wired Client (vlan 350)
Network Topology:
1. Mesh Portal is connected to a trunk port on the switch1
Native vlan: 350
Allowed vlan : 1,350,100
2. Mesh point's E0 port is connected to a switch2 & will act as downlink port.
Switch port config:
Native vlan: 350
Allowed vlan : 1,350,100
Requirement:
1. Client connected to Switch2 on access port for vlan 350 should get an IP from the DHCP present on Switch1
This is the same vlan on which mesh portal/point are getting an IP address.
However, if we connect a client on vlan 100 (non native vlan), it gets an IP address without any issues.
Diagnostics:We need to enable debug pkt dump for DHCP one mesh portal/point to understand the issue in a better way.
IAP#debug pkt match mac <mac-address of the client>
IAP# debug pkt type dhcp
IAP# debug pkt dump
Mesh Point :
1. We can see that the discover is seen on vlan 350 as expected.
Received packet from bond0 (timestamp (2016-5-13 16:04:07:246802))
[asap_firewall_forward(5055):firewall entry] len 342, vlan 0, egress CP, ingress bond0:
#mac: etype 0800 smac f0:1f:af:64:d6:c3 dmac ff:ff:ff:ff:ff:ff
#ip: sip 0.0.0.0, dip 255.255.255.255, proto 17, dscp 0, fragment ok, last fragment, fragment offset 0
#udp: sport 68 dport 67 len 308
#dhcp: message-type: request
hardware type: 1, len: 6, hops: 0
txn id: 0x69466a51, seconds elapsed: 768
client mac: f0:1f:af:64:d6:c3
magic cookie: 0x63825363
#dhcp-option: message-type: discover ----------------------------------------------------------------------------->>DISCOVER
[asap_firewall_forward(5229):vlan decision] len 342, vlan 350, egress CP, ingress bond0:-------------->> VLAN 350
[asap_firewall_check_dhcp_packet(2388):dhcp packet from client] len 342, vlan 350, egress CP, ingress bond0:
[asap_firewall_forward(5632):looking up bridge entry] len 342, vlan 350, egress CP, ingress bond0:
2. The OFFER packet is seen on vlan 1 rather than vlan 350 due to which the client is unable to get an IP address.
Received packet from aruba000 (timestamp (2016-5-13 16:04:07:366126))
[asap_firewall_forward(5055):firewall entry] len 342, vlan 0, egress CP, ingress aruba000:
#mac: etype 0800 smac 00:0b:86:95:b9:77 dmac f0:1f:af:64:d6:c3
#ip: sip 10.17.171.176, dip 10.17.171.183, proto 17, dscp 4, fragment ok, last fragment, fragment offset 0
#udp: sport 67 dport 68 len 308
#dhcp: message-type: reply
hardware type: 1, len: 6, hops: 0
txn id: 0x69466a51, seconds elapsed: 768
your ip: 10.17.171.183
next server ip: 10.17.171.176
client mac: f0:1f:af:64:d6:c3
magic cookie: 0x63825363
#dhcp-option: netmask: 255.255.255.224
#dhcp-option: router: 10.17.171.161
#dhcp-option: dns-server: 4.2.2.2
#dhcp-option: dns-name: tac.com
#dhcp-option: message-type: offer----------------------------------------------------------------------------------------------------->>OFFER
#dhcp-option: dhcp-server: 10.17.171.176
[asap_firewall_forward(5229):vlan decision] len 342, vlan 1, egress CP, ingress aruba000:------------------------------->>VLAN 1
[asap_firewall_check_dhcp_packet(2428):dhcp packet to client] len 342, vlan 1, egress CP, ingress aruba000:
Mesh Portal :
1. Mesh Portal also receives the DISCOVER on vlan 350.
Received packet from aruba000 (timestamp (2016-4-13 16:04:13:357822))
[asap_firewall_forward(5055):firewall entry] len 346, vlan 0, egress CP, ingress aruba000:
#mac: etype 8100 smac f0:1f:af:64:d6:c3 dmac ff:ff:ff:ff:ff:ff
#vlan 350, prio 0, etype 0800
#ip: sip 0.0.0.0, dip 255.255.255.255, proto 17, dscp 0, fragment ok, last fragment, fragment offset 0
#udp: sport 68 dport 67 len 308
#dhcp: message-type: request
hardware type: 1, len: 6, hops: 0
txn id: 0x69466a51, seconds elapsed: 2816
client mac: f0:1f:af:64:d6:c3
magic cookie: 0x63825363
#dhcp-option: message-type: discover
[asap_firewall_forward(5229):vlan decision] len 346, vlan 350, egress CP, ingress aruba000:
[asap_firewall_forward(5632):looking up bridge entry] len 346, vlan 350, egress CP, ingress aruba000:
[asap_firewall_forward(5943):bridge section] len 346, vlan 350, egress CP, ingress aruba000:
[asap_firewall_forward(6072):session section] len 346, vlan 350, egress vlan 350, ingress aruba000:
2. However, the OFFER from the uplink switch is sent over vlan 1.
Received packet from bond0 (timestamp (2016-4-13 16:04:13:360343))
[asap_firewall_forward(5055):firewall entry] len 342, vlan 0, egress CP, ingress bond0:
#mac: etype 0800 smac 00:0b:86:95:b9:77 dmac f0:1f:af:64:d6:c3
#ip: sip 10.17.171.176, dip 10.17.171.183, proto 17, dscp 4, fragment ok, last fragment, fragment offset 0
#udp: sport 67 dport 68 len 308
#dhcp: message-type: reply
hardware type: 1, len: 6, hops: 0
txn id: 0x69466a51, seconds elapsed: 2816
your ip: 10.17.171.183
next server ip: 10.17.171.176
client mac: f0:1f:af:64:d6:c3
magic cookie: 0x63825363
#dhcp-option: netmask: 255.255.255.224
#dhcp-option: router: 10.17.171.161
#dhcp-option: dns-server: 4.2.2.2
#dhcp-option: dns-name: tac.com
#dhcp-option: message-type: offer
#dhcp-option: dhcp-server: 10.17.171.176
[asap_firewall_forward(5229):vlan decision] len 342, vlan 1, egress CP, ingress bond0:
[asap_firewall_check_dhcp_packet(2428):dhcp packet to client] len 342, vlan 1, egress CP, ingress bond0:
[asap_firewall_forward(5632):looking up bridge entry] len 342, vlan 1, egress CP, ingress bond0:
[asap_firewall_forward(5943):bridge section] len 342, vlan 1, egress CP, ingress bond0:
3. Wired Port profile that we map to E0 profile has native vlan set to 350.
However, wired-port profile only works on downlink port. We enable enet0 bridging on the mesh point which makes its E0 port as downlink which starts using this wired profile.

Hence, the native vlan for the mesh point changes to vlan 350.
4. The native vlan on E0 port of mesh portal is still vlan 1 (by default)

This causes the DHCP OFFER to be sent over vlan 1.
Solution1. We need to configure Enet-vlan on the Mesh Portal .
This will be pushed to the mesh point as well.

The above command informs the AP about the native-vlan of the upstream switch it is connected . By default , AP assumes it to be vlan 1. This ensures that AP does not send out tagged frames for the clients connected on the vlan which has the same vlan
as native vlan of the switch.
2. After running the above command, we can see that native vlan of the mesh portal changes to 350 as well.
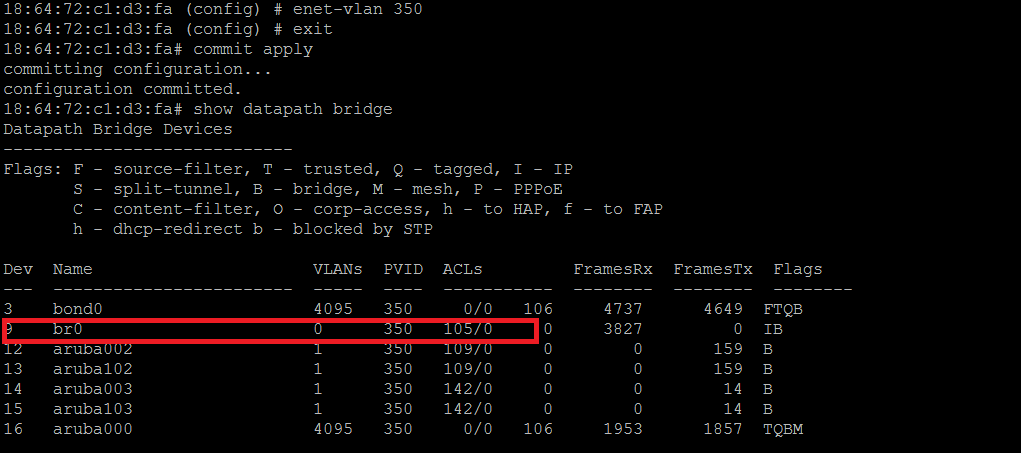
3. We will check the DHCP packet dump again.
Mesh Point :
Received packet from aruba000 (timestamp (2016-5-13 16:07:37:490309))
[asap_firewall_forward(5055):firewall entry] len 342, vlan 0, egress CP, ingress aruba000:
#mac: etype 0800 smac f0:1f:af:64:d6:c3 dmac ff:ff:ff:ff:ff:ff
#ip: sip 0.0.0.0, dip 255.255.255.255, proto 17, dscp 0, fragment ok, last fragment, fragment offset 0
#udp: sport 68 dport 67 len 308
#dhcp: message-type: request
hardware type: 1, len: 6, hops: 0
txn id: 0xb249e8c7, seconds elapsed: 768
client mac: f0:1f:af:64:d6:c3
magic cookie: 0x63825363
#dhcp-option: message-type: discover
[asap_firewall_forward(5229):vlan decision] len 342, vlan 350, egress CP, ingress aruba000:
[asap_firewall_check_dhcp_packet(2388):dhcp packet from client] len 342, vlan 350, egress CP, ingress aruba000:
Received packet from aruba000 (timestamp (2016-5-13 16:07:38:365811))
[asap_firewall_forward(5055):firewall entry] len 342, vlan 0, egress CP, ingress aruba000:
#mac: etype 0800 smac 00:0b:86:95:b9:77 dmac f0:1f:af:64:d6:c3
#ip: sip 10.17.171.176, dip 10.17.171.183, proto 17, dscp 4, fragment ok, last fragment, fragment offset 0
#udp: sport 67 dport 68 len 308
#dhcp: message-type: reply
hardware type: 1, len: 6, hops: 0
txn id: 0xb249e8c7, seconds elapsed: 768
your ip: 10.17.171.183
next server ip: 10.17.171.176
client mac: f0:1f:af:64:d6:c3
magic cookie: 0x63825363
#dhcp-option: netmask: 255.255.255.224
#dhcp-option: router: 10.17.171.161
#dhcp-option: dns-server: 4.2.2.2
#dhcp-option: dns-name: tac.com
#dhcp-option: message-type: offer
#dhcp-option: dhcp-server: 10.17.171.176
[asap_firewall_forward(5229):vlan decision] len 342, vlan 350, egress CP, ingress aruba000:
[asap_firewall_check_dhcp_packet(2428):dhcp packet to client] len 342, vlan 350, egress CP, ingress aruba000:
Mesh Portal :
Received packet from aruba000 (timestamp (2016-4-13 16:07:35:911962))
[asap_firewall_forward(5055):firewall entry] len 342, vlan 0, egress CP, ingress aruba000:
#mac: etype 0800 smac f0:1f:af:64:d6:c3 dmac ff:ff:ff:ff:ff:ff
#ip: sip 0.0.0.0, dip 255.255.255.255, proto 17, dscp 0, fragment ok, last fragment, fragment offset 0
#udp: sport 68 dport 67 len 308
#dhcp: message-type: request
hardware type: 1, len: 6, hops: 0
txn id: 0xb249e8c7, seconds elapsed: 768
client mac: f0:1f:af:64:d6:c3
magic cookie: 0x63825363
#dhcp-option: message-type: discover
[asap_firewall_forward(5229):vlan decision] len 342, vlan 350, egress CP, ingress aruba000:
[asap_firewall_forward(5632):looking up bridge entry] len 342, vlan 350, egress CP, ingress aruba000:
Received packet from bond0 (timestamp (2016-4-13 16:07:36:788040))
[asap_firewall_forward(5055):firewall entry] len 342, vlan 0, egress CP, ingress bond0:
#mac: etype 0800 smac 00:0b:86:95:b9:77 dmac f0:1f:af:64:d6:c3
#ip: sip 10.17.171.176, dip 10.17.171.183, proto 17, dscp 4, fragment ok, last fragment, fragment offset 0
#udp: sport 67 dport 68 len 308
#dhcp: message-type: reply
hardware type: 1, len: 6, hops: 0
txn id: 0xb249e8c7, seconds elapsed: 768
your ip: 10.17.171.183
next server ip: 10.17.171.176
client mac: f0:1f:af:64:d6:c3
magic cookie: 0x63825363
#dhcp-option: netmask: 255.255.255.224
#dhcp-option: router: 10.17.171.161
#dhcp-option: dns-server: 4.2.2.2
#dhcp-option: dns-name: tac.com
#dhcp-option: message-type: offer
#dhcp-option: dhcp-server: 10.17.171.176
[asap_firewall_forward(5229):vlan decision] len 342, vlan 350, egress CP, ingress bond0:
[asap_firewall_check_dhcp_packet(2428):dhcp packet to client] len 342, vlan 350, egress CP, ingress bond0:
18:64:72:c1:d3:fa# show clients wired
Wired Client List
-----------------
Name IP Address MAC Address OS Network Access Point Role Speed (mbps)
---- ---------- ----------- -- ------- ------------ ---- ------------
SATTY-BLR-02-PC 10.17.171.183 f0:1f:af:64:d6:c3 eth0 18:64:72:c9:c4:9c Mesh -
Info timestamp :1048